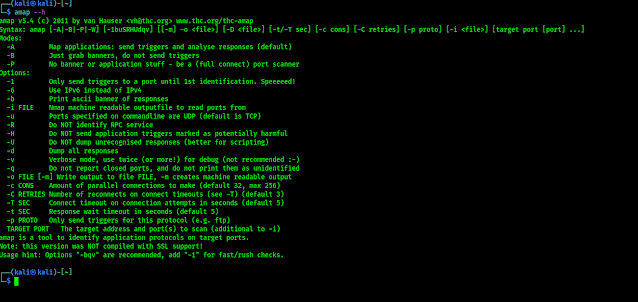
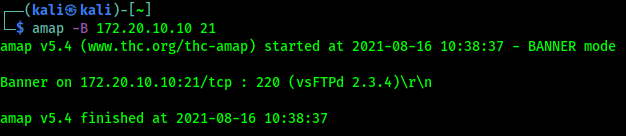
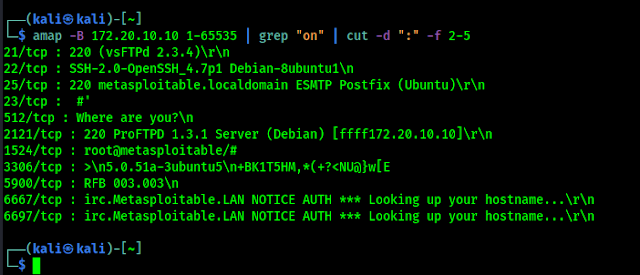
There are lots of scanning tools used by cybersecurity professionals. Not arguably Nmap is the most famous scanning tool, but it is very slow. There are lots of more useful scanners. Masscan is the fastest port scanner in the world, but masscan is not so accurate.
If we need a enough fast scanner that gives us much reliable result we can choose Unicornscan. Unicornscan comes pre-installed with Kali Linux.
Unicornscan is a asynchronous based scanner (unlike nmap is synchronous based). That’s why it is faster.
Unicornscan was designed to provide an engine that is Scalable, Accurate, Flexible, and Efficient. It is released for the community to use under the terms of the GPL license.
Key-Features of Unicornscan
Unicornscan is an attempt at a User-land Distributed TCP/IP stack. It is intended to provide a researcher a superior interface for introducing a stimulus into and measuring a response from a TCP/IP enabled device or network. Although it currently has hundreds of individual features, a main set of abilities include:
- Asynchronous stateless TCP scanning with all variations of TCP Flags.
- Asynchronous stateless TCP banner grabbing
- Asynchronous protocol specific UDP Scanning (sending enough of a signature to elicit a response).
- Active and Passive remote OS, application, and component identification by analyzing responses.
- PCAP file logging and filtering.
- Relational database output.
- Custom module support.
- Customized data-set views.
- Has its TCP/IP stack, a distinguishing feature that sets it apart from other port scannersHas its TCP/IP stack, a distinguishing feature that sets it apart from other port scanners.
Scanning With Unicornscan
While Unicornscan comes built into Kali Linux we don’t need to install it. If if we need to install it we can use following command:
sudo apt-get install unicornscan
First we start with basic scan. To perform a basic scan we can use following command:
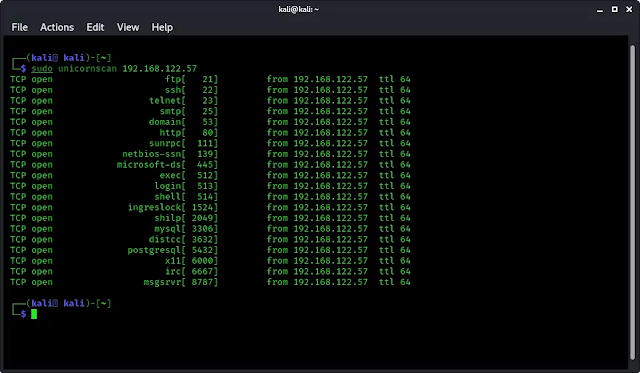
sudo unicornscan 192.168.112.57
The output of the command shows in the following screenshot:
Here we have run unicoenscan on a Metspliotable2 machine and we can see that the normal scan has listed all the opened TCP ports of host machine. It’s kind of similar to -Ss scan in NMap.
If we need to run basic scan using unicornscan on multiple hosts then we can run following command:
sudo unicornscan 192.168.112.57 192.168.102.100
In this case we run the scan cammand and put 2 hosts divided with ‘space’.
We also can run it against live websites, here we want that unicornscan send 30 packets per second, so we use -r30 flag. We also look for TCP ports so we can run the scan using -mT scan (T is for TCP). So the command will be following:
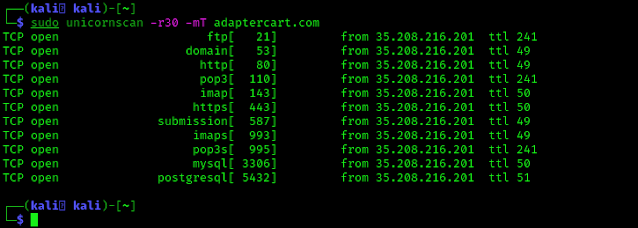
sudo unicornscan -r30 -mT adaptercart.com
And we got the result as we want. As we can see in the following screenshot:
In the above screenshot we can see that unicornscan scans the website’s TCP ports.
We have seen that unicornscan scans the TCP ports using -mT flag, but if we want to scan UDP ports then we can try with -mU flag. Mind the similarities then it will be easy to remember. The command will be as following:
sudo unicornscan -r300 -mU 192.168.112.57
The screenshot is following:
In the above screenshot we can see that we got UDP ports only from the hosts.
We can save the scan result in a PCAP file using following command:
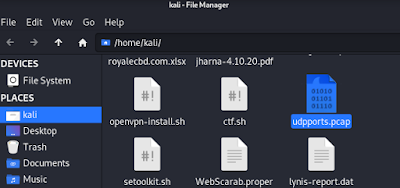
sudo unicornscan -r300 -mU 192.168.112.57 -w udpports.pcap
Using the above command (-w flag) we can save the scan result in a PCAP file. We can choose any name, for an example we have chosen “udpports”. The file will be saved on our home/user directory, as we can see in the following screenshot:
This the the basic uses of Unicornscan. If we want to learn more advanced scans then we can see the help menu of Unicornscan by applying following command:
sudo unicornscan -h
This is how we can scan a host or a website using Unicornscan on our Kali Linux system.
Love our super easy articles ? Don’t wanna miss new articles? We post updates of our articles on GitHub and Twitter. Make sure to follow us there to read and learn about cybersecurity.
Have any problem or any question? Please don’t hesitate to ask us in the comment section. We read every comments and we always reply.