Ncrack is a high-speed network authentication cracking tool. It was built to help companies secure their networks by proactively testing all their hosts and networking devices for poor passwords. Security professionals also rely on Ncrack when auditing their clients. Ncrack comes pre-installed with Kali Linux.
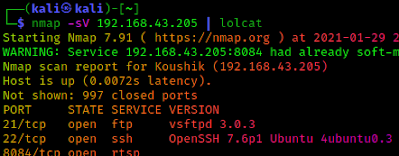
During penetration testing sometimes we got sometimes we got some port opened on some web application. Ports are open for using services. Services like SSH, FTP, HTTP, SMTP etc. We usually use nmap to scan a network.
We can see in the above nmap scan result, this network’s SSH and FTP ports are opened (port 21 and 22). If we can login through SSH then we got the terminal of the system and if we login through FTP then we got the file manager of the system.
We can try various tools to crack them like Hydra. But in this article we are going to learn about Ncrack.
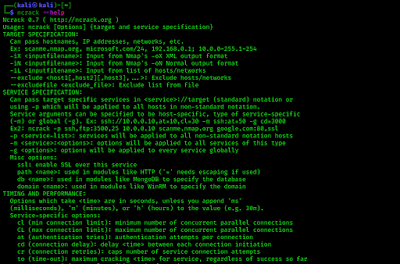
Firstly we run following command to check the helps of Ncrack. Ncrack uses brute force attacks to crack network credentials. We have found lots of network admins using default or easy password, we can crack them using Ncrack in minutes.
ncrack --help
We can see a very big list of options in the help section as we can see in the following screenshot:
Without going much deeper let’s check an basic example of Ncrack brute force attack.
To use Ncrack against a service we can use following command:
ncrack -U path/of/usernamelist -P path/of/passwordlist <ip address or domain name>:port -v
So, if we want to attack on our localhost target using real username and password list, then our command will be following:
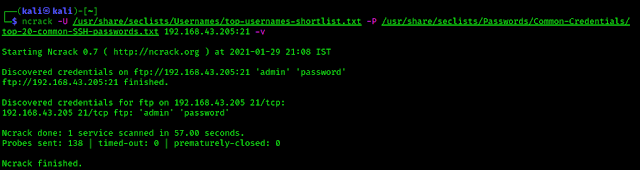
ncrack -U /usr/share/seclists/Usernames/top-usernames-shortlist.txt -P /usr/share/seclists/Passwords/Common-Credentials/top-20-common-SSH-passwords.txt 192.168.43.205:21 -v
Here we have used infamous SecLists, which comes preinstalled with Kali Linux. The output we can see in the following screenshot:
In the above screenshot we can see that Ncrack successfully cracked the credentials. The credentials are username:admin, password:password. Not only our target, there are lots of users around the world still using default or easy passwords.
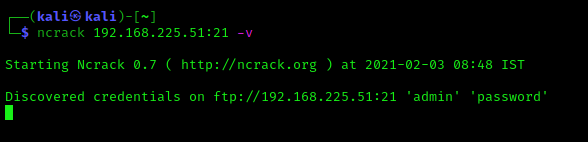
Ncrack also comes with a default (small) username and password list to attack. To use it we can use following command:
ncrack 192.168.225.51:21 -v
This command will use the default password list comes with Ncrack. It has some default username and password lists. The screenshot is following:
If we need to run Ncrack’s brute force attack against ssh (port 22) then we can use following command:
ncrack whatsapp5.com:22 -v
We can find other Ncrack commands using ncrack –help command.
This is the way we can find low security usernames and passwords of FTP, SSH, web server or web application.
In this article we learn how we can use Ncrack on Kali Linux.
Disclaimer:- Use of Ncrack against a network without proper permission is illegal & serious crime. We can test our own system for low security password. If anyone do any illegal activity then we are not responsible for that.
Liked our article? Then make sure to follow our Twitter and GitHub we post new article updates there. To connect directly with us please join our Telegram group.
For any problem or question please comment down in the comment section.