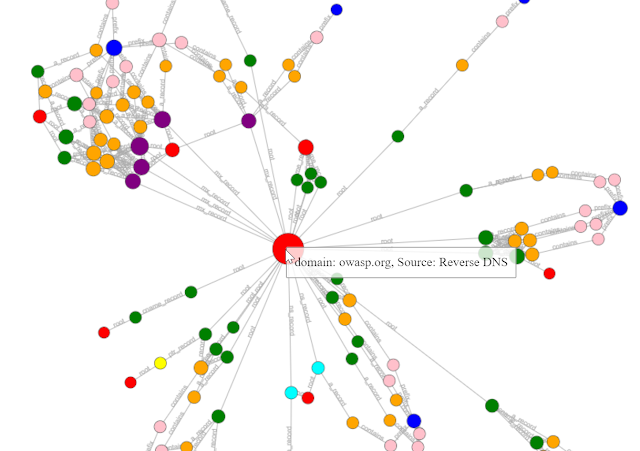
The last update of Kali Linux in 2021 is Rolling to ROCK.
Say Welcome to Kali Linux 2021.4! This release welcomes a mixture of new items as well as enhancements of existing features, and is ready to be downloaded (from our updated page) or upgraded if we have an existing Kali Linux installation.
The summary of the changelog since the 2021.3 release from September 2021 is:
- Improved Apple M1 support
- Wide compatibility for Samba
- Switching package manager mirrors
- Kaboxer theming
- Updates to Xfce, GNOME and KDE
- Raspberry Pi Zero 2 W + USBArmory MkII ARM images
- More tools
Kali on the Apple M1
As we announced in Kali 2021.1 we supported installing Kali Linux on Parallels on Apple Silicon Macs, well with 2021.4, we now also support it on the VMware Fusion Public Tech Preview thanks to the 5.14 kernel having the modules needed for the virtual GPU used. We also have updated the open-vm-tools package, and Kali’s installer will automatically detect if we are installing under VMware and install the open-vm-tools-desktop package, which should allow we to change the resolution out of the box. As a reminder, this is still a preview from VMware, so there may be some rough edges. There is no extra documentation for this because the installation process is the same as VMWare on 64-bit and 32-bit Intel systems, just using the arm64 ISO.
As a reminder, virtual machines on Apple Silicon are still limited to arm64 architecture only.
Extended Compatibility for the Samba Client
Starting Kali Linux 2021.4, the Samba client is now configured for Wide Compatibility so that it can connect to pretty much every Samba server out there, regardless of the version of the protocol in use. This change should make it easier to discover vulnerable Samba servers “out of the box”, without having to configure Kali.
This setting can be changed easily via the command-line tool kali-tweaks. In the Hardening section, one can choose the value Default instead, which reverts back to Samba’s usual default, and only allow using modern versions of the Samba protocol.
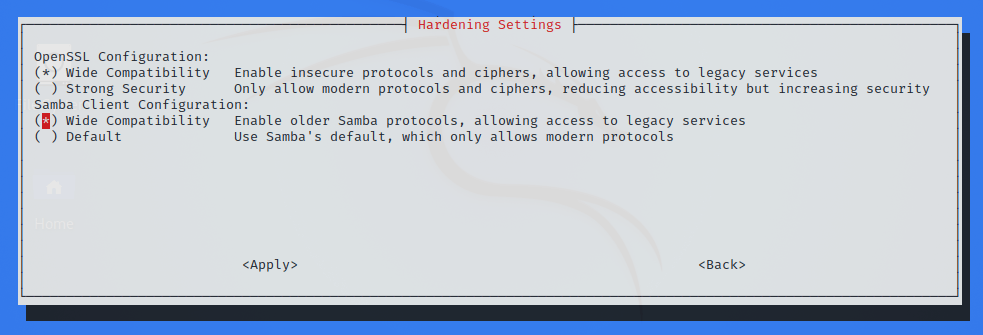
As one can see on this screenshot, there’s also a similar setting for OpenSSL. We might want to refer to the 2021.3 release announcement for more details on this setting.
Easy Package Manager Mirror Configuration
By default, when a Kali system is updated, the package manager (APT) downloads packages from a community mirror nearby. But did we know that it’s also possible to configure Kali to get its package from the CloudFlare CDN? To be honest, this is old news. But what’s new is that we can now use kali-tweaks to quickly configure whether APT should use community mirrors or the CloudFlare CDN.
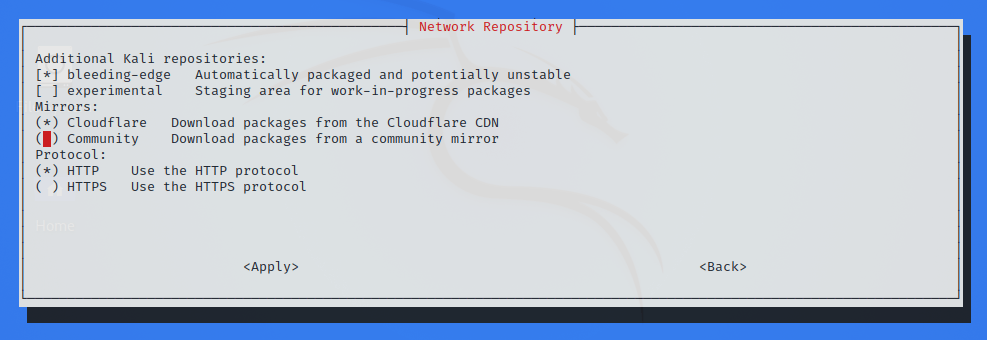
So which one is best, community mirrors or CloudFlare CDN? There’s no good answer. The time that it actually takes to update Kali can vary greatly and depends on many factors, including the speed of our Internet connection, our location, and even the time of day, if ever we live in a place where Internet traffic jam occurs at rush hour. The point is: if ever Kali updates are slow, the best we can do is to try to switch from community mirrors to CloudFlare CDN, or the other way round, and find what works best for we. And with kali-tweaks, it’s never been easier!
Kaboxer Theme Support
With the latest update of Kaboxer tools no longer look out of place, as it brings support for window themes and icon themes (placed respectively inside /usr/share/themes and /usr/share/icons). This allows the program to properly integrate with the rest of the desktop and avoids the usage of ugly fallback themes.
Here is a comparison of how zenmap (zenmap-kbx package) looks with the default Kali Dark theme, compared to the old appearance:
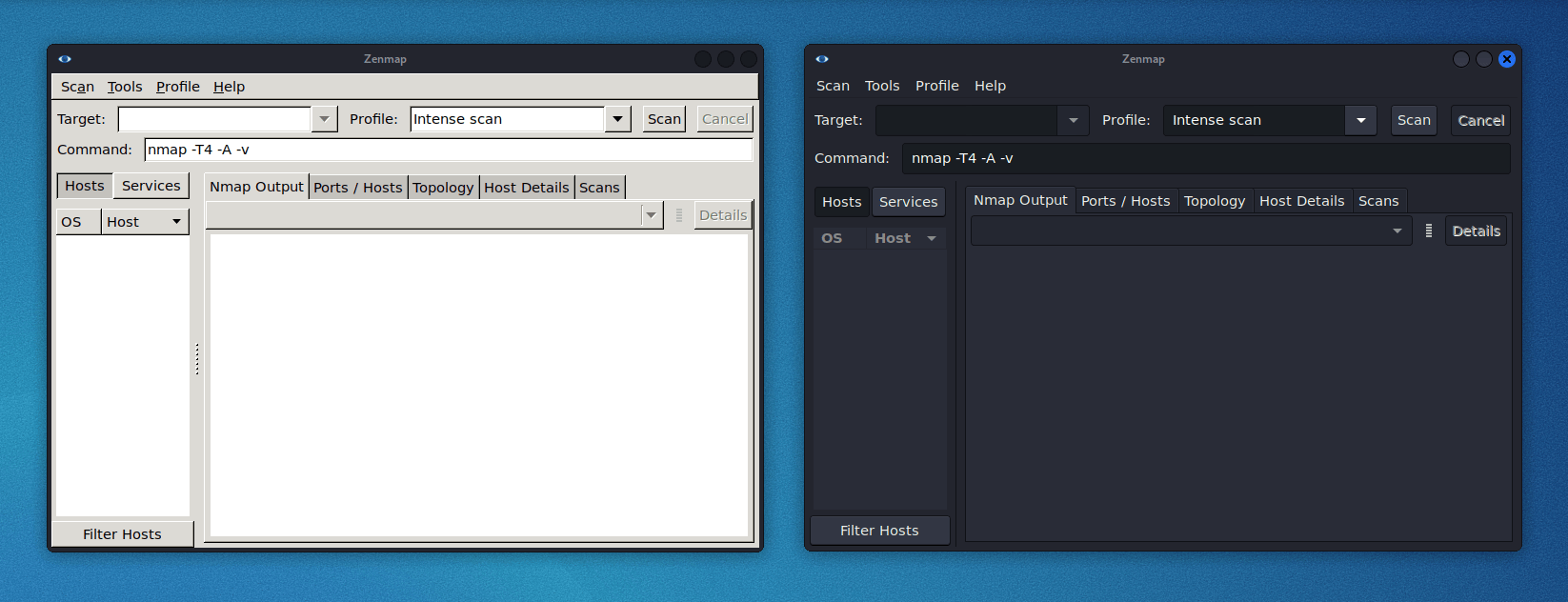
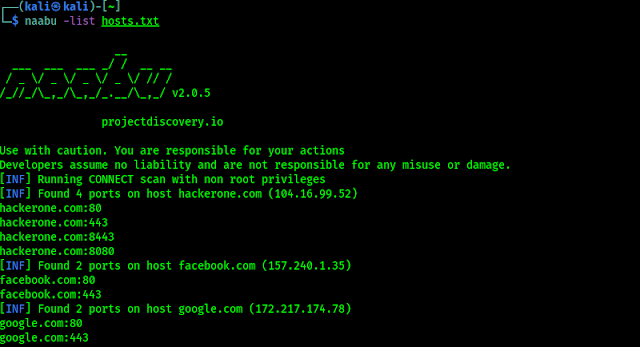
It would not be a Kali release if there were not any new tools added! A quick run down of what’s been added (to the network repositories):
-
Dufflebag – Search exposed EBS volumes for secrets
-
Maryam – Open-source Intelligence (OSINT) Framework
-
Name-That-Hash – Do not know what type of hash it is? Name That Hash will name that hash type!
-
Proxmark3 – if we are into Proxmark3 and RFID hacking
-
Reverse Proxy Grapher – graphviz graph illustrating our reverse proxy flow
-
S3Scanner – Scan for open S3 buckets and dump the contents
-
Spraykatz – Credentials gathering tool automating remote procdump and parse of lsass process.
-
truffleHog – Searches through git repositories for high entropy strings and secrets, digging deep into commit history
-
Web of trust grapher (wotmate) – reimplement the defunct PGP pathfinder without needing anything other than our own keyring
Desktop & Theme Enhancement
This release brings updates for all the 3 main desktops (Xfce, GNOME, and KDE), but one that is common to all of them is the new window buttons design. Previous buttons were designed to fit the window theme of Xfce but did not work well with the other desktops and lacked personality. The new design looks elegant on any of the desktops and makes it easier to spot the currently focused window.

Xfce
The panel layout has been tweaked to optimize horizontal space and make room for 2 new widgets: the CPU usage widget and the VPN IP widget, which remains hidden unless a VPN connection is established.
Following the steps of other desktops, the task manager has been configured to “icons only”, which, with the slight increase in the panel’s height, makes the overall look cleaner and improves multitasking in smaller displays.
The workspaces overview has been configured to the “Buttons” appearance, as the previous configuration “Miniature view” was too wide and a bit confusing for some users. Now that each workspace button takes less space in the panel, we have increased the default number of workspaces to 4, as it’s a usual arrangement in Linux desktops.
To finish with the modifications, a shortcut to PowerShell has been added to the terminals dropdown menu. With this addition, we can now choose between the regular terminal, root terminal, and PowerShell.
If we prefer the previous configuration for any of the widgets, we can modify or remove them by pressing Ctrl + Right-Click over it.
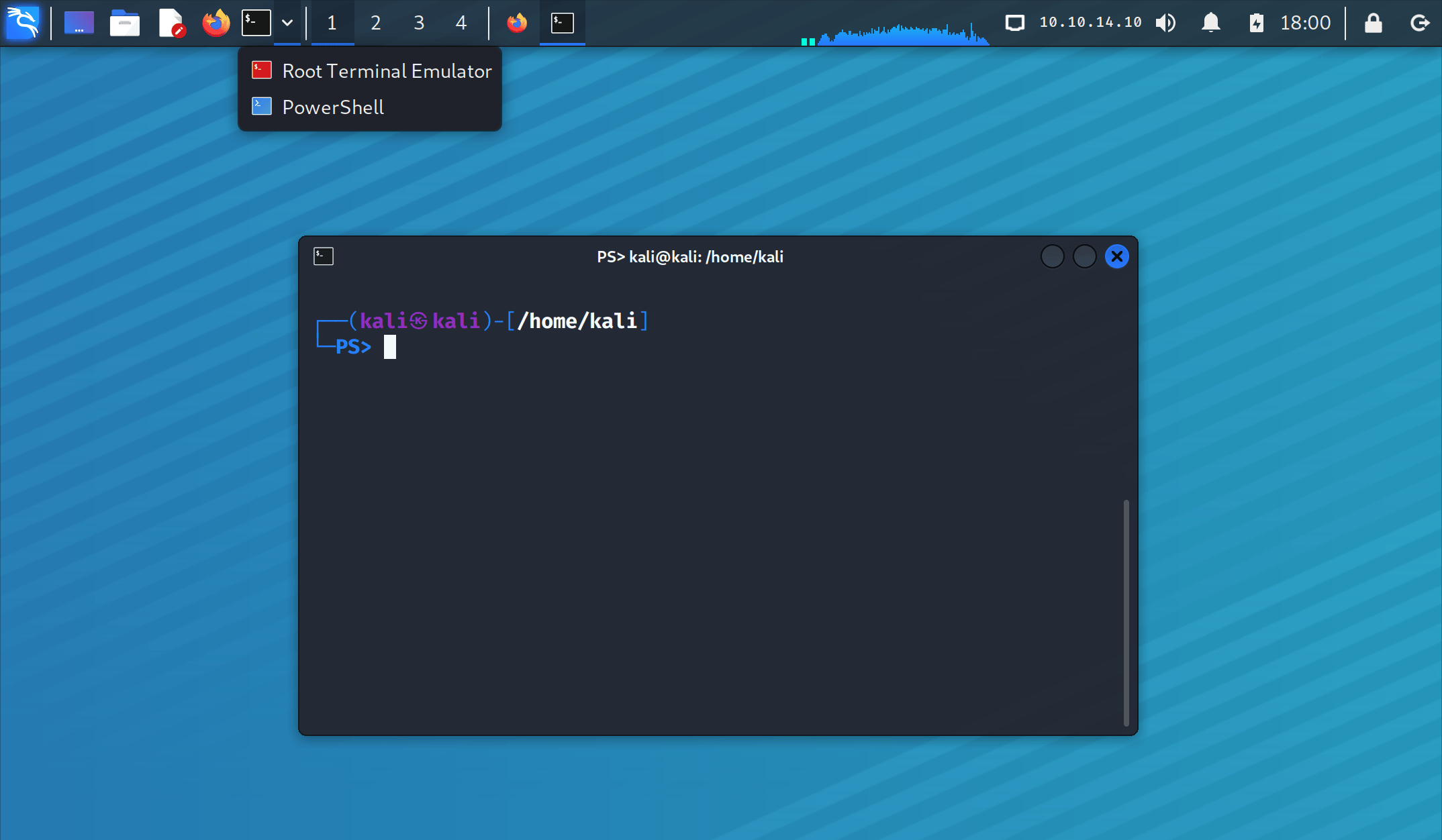
In addition to the Xfce design tweaks, In the image above, we can also observe the new customized prompt for PowerShell (in the two-line mode). Same as for zsh and bash, it includes an alternative one-line prompt that can be configured with kali-tweaks.
Bonus Tips For Virtual Desktops!
- We can add or remove workspaces with the shortcuts:
Alt + Insert / Alt + Delete
- We can move through workspaces with the shortcuts:
-
Ctrl + Alt + <ARROW_KEY> to move in the direction of the arrow key.
- (if we add
Shift we move the current focused window)
-
Ctrl + Alt + <WORKSPACE_NUM> to move to a specific workspace, based on its number.
-
Ctrl + Super + <WORKSPACE_NUM> to move a window to a specific workspace, based on its number.
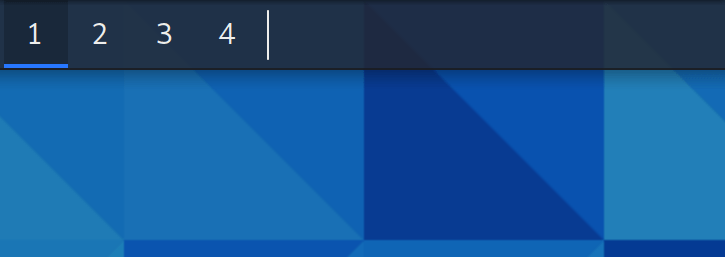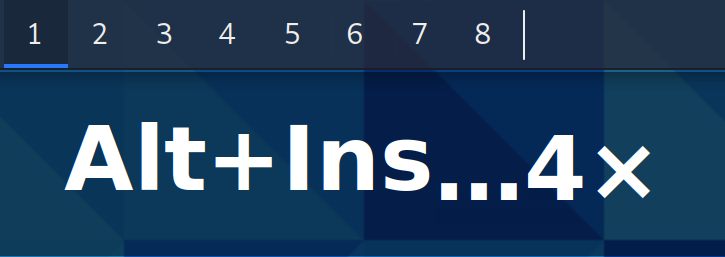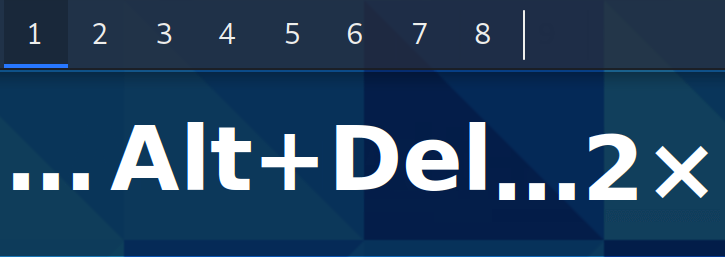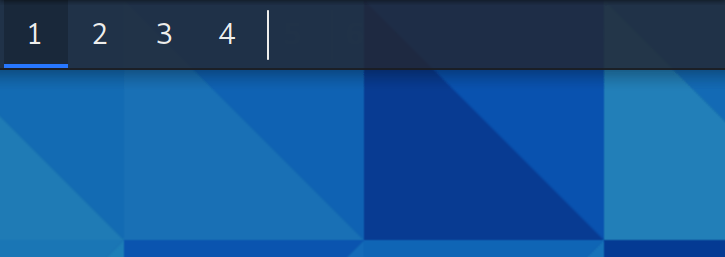
GNOME 41
In this update, GNOME desktop has received not one, but two version bumps. It’s been one year since the last major update of the GNOME desktop in Kali (with GNOME 3.38) and since then there have been two releases of the desktop environment:
All themes and extensions have been updated to support the new shell:
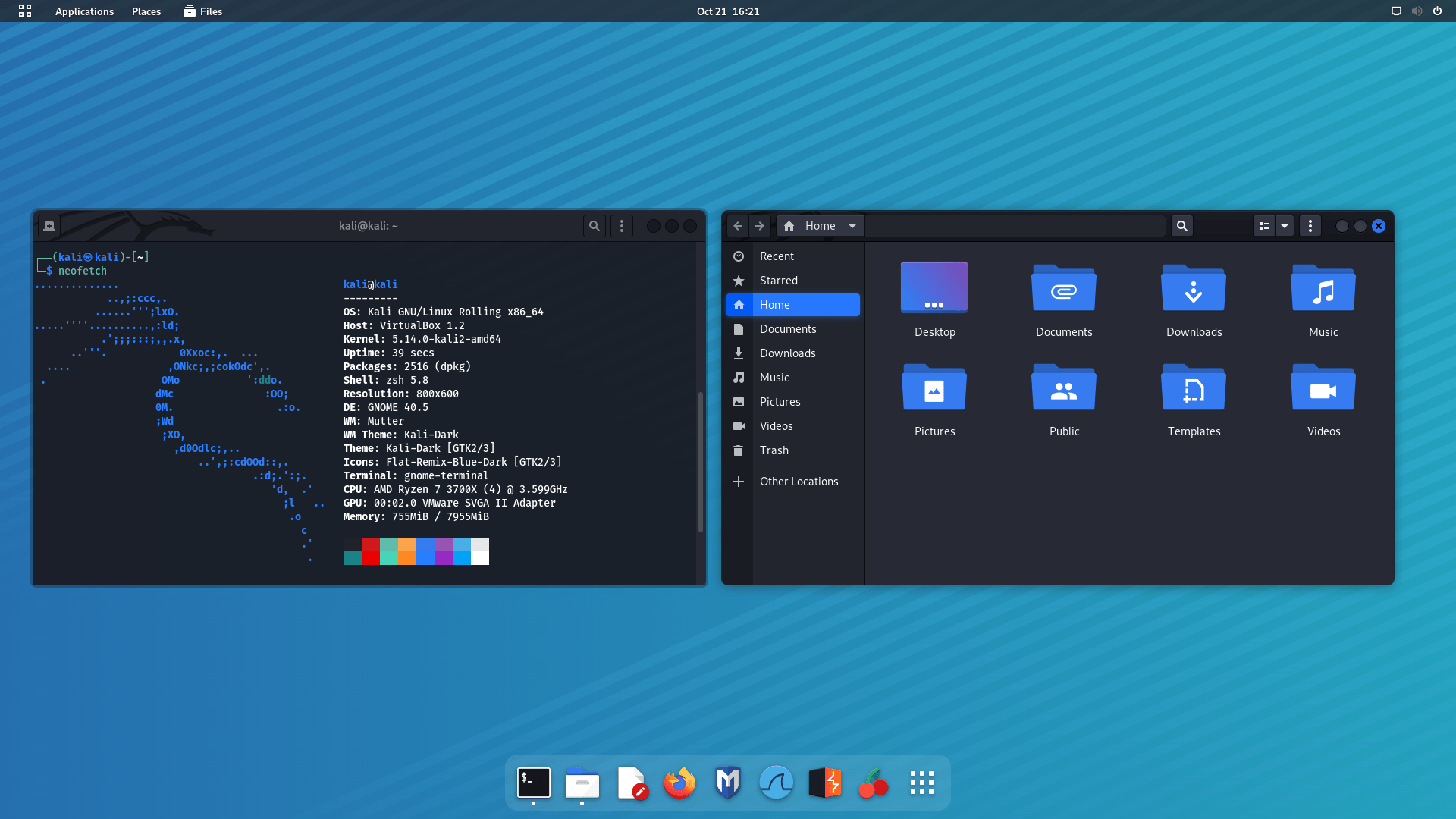
KDE 5.23
The KDE team celebrated its 25th anniversary releasing the update 5.23 of the Plasma desktop. This update, now available in Kali, brings a new design for the Breeze theme, which improves the look of Plasma with details that add glossiness and style to the desktop. Along with the theme improvements, the System Settings (Under Global Theme > Colors) brings a new option to pick the desktop accent color.
From Kali’s side, the new window theme for KDE is now based on the source code of the breeze theme instead of using the Aurorae theme engine. This fixes previous issues with window scaling for HiDPI displays.
How to Upgrade Your Kali Theme
With these theme changes, we may not get them if we upgrade Kali. This is because the theme settings are copied to our home folder when our user is first created. When we upgrade Kali, it is upgrading the operating system, so upgrading does not alter personal files (just system files). As a result, in order to get these theme tweaks, we need to either:
- Do a fresh Kali install
- Create a new user and switch to that
- Delete our Desktop environment profile for the current user and force reboot. Example of Xfce can be found below:
kali@kali:~$ mv ~/.config/xfce4{,-$(date +%Y.%m.%d-%H.%M.%S)}
kali@kali:~$
kali@kali:~$ cp -rbi /etc/skel/. ~/
kali@kali:~$
kali@kali:~$ xfce4-session-logout --reboot --fast
Kali NetHunter Updates
Thanks to the amazing work of @yesimxev, we have a new addition to the NetHunter app: The Social-Engineer Toolkit!
This release features the first module from SET: the Spear Phishing Email Attack, with many more to come – watch this space…
Now we can use the Kali NetHunter app to customise our own Facebook, Messenger, or Twitter direct message email notifications for our social engineering attacks:

Thanks to everyone that contributed to this feature by participating in the Twitter poll. We could not have done it without input!
Kali ARM Updates
Notable changes this release
-
All images now use ext4 for their root filesystem, and resize the root filesystem on first boot. This results in a speed-up over previous releases which were using ext3, and a reduced boot time on the first reboot when resize happens.
-
Raspberry Pi Zero 2 W support has been added, but like the Raspberry Pi 400, there is no Nexmon support.
- Speaking of the Raspberry Pi Zero 2 W, since it is so similar to the Zero W, we have also added a PiTail image to support the new processor with better performance.
-
Raspberry Pi images now support USB booting out of the box since we no longer hardcode the root device.
-
Raspberry Pi images now include versioned Nexmon firmware. A future release of
kalipi-config will allow we to switch between them, if we would like to test different versions.
- Images that use a vendor kernel will now be able to set the regulatory domain properly, so setting our country will give access to channels properly for wireless.
-
Pinebook Pro can now be overclocked. The big cores get 2GHz and the little cores get 1.5GHz added.
-
echo 1 | sudo tee /sys/devices/system/cpu/cpufreq/boost to enable
-
echo 0 | sudo tee /sys/devices/system/cpu/cpufreq/boost to disable
-
USBArmory MkII image has been added.
Kali ARM build-scripts have seen a massive amount of changes:
- They are vastly more simplified – thanks to Francisco Jose Rodriguez Martos, and cyrus104 for all of their contributions to make this happen.
- We can now choose which desktop we would like to install (or none at all using
--minimal)
- There is even an option of no desktop and no tools (
--slim) if we would like to build a custom image up from scratch
Kali-Docs Updates
Anyone can help out, anyone can get involved!
Miscellaneous
Kali-Cloud & Cron
Some users noticed that the venerable cron package was missing from the Kali AWS Cloud image. This was not intentional, and it’s now fixed.
Remote Desktop Protocol Audio
“The quieter you become, the more you are able to hear”, goes the saying. And for those running Kali in a VM and using RDP to connect, it’s been very quiet indeed, as the sound never worked with this configuration. However this long period of silence is coming to an end! Sound should be enabled and work out of the box from now on. If ever it does not, make ourself heard on the bug tracker 😉
Python Command
The command python is no more! Instead, we need to use python3 (or if we have to, python2 due it being at End Of Life). Alternatively we can install python-is-python3 to restore python as an alias for python3.
Download Kali Linux 2021.4
Fresh Images: So what are waiting for? Start downloading already!
Seasoned Kali Linux users are already aware of this, but for the ones who are not, we do also produce weekly builds that you can use as well. If you cannot wait for our next release and you want the latest packages (or bug fixes) when you download the image, you can just use the weekly image instead. This way you’ll have fewer updates to do. Just know that these are automated builds that we do not QA like we do our standard release images. But we gladly take bug reports about those images because we want any issues to be fixed before our next release!
Existing Installs: If you already have an existing Kali Linux installation, remember you can always do a quick update:
echo "deb http://http.kali.org/kali kali-rolling main non-free contrib" | sudo tee /etc/apt/sources.list
sudo apt update && sudo apt -y full-upgrade
[ -f /var/run/reboot-required ] && sudo reboot -f
┌──(kali㉿kali)-[~]
└─$ grep VERSION /etc/os-release
VERSION="2021.4"
VERSION_ID="2021.4"
VERSION_CODENAME="kali-rolling"
┌──(kali㉿kali)-[~]
└─$ uname -v
#1 SMP Debian 5.14.16-1kali1 (2021-11-05)
┌──(kali㉿kali)-[~]
└─$ uname -r
5.14.0-kali4-amd64
NOTE: The output of uname -r may be different depending on the system architecture.
As always, should you come across any bugs in Kali, please submit a report on our
bug tracker.
We’ll never be able to fix what we do not know is broken! And Twitter is not a Bug Tracker!










 Northern Michigan University’s (NMU) YooperCon event helped facilitate capture the flag (CTF) competitions and other cybersecurity awareness-focused sessions to support nearly 240 high school students interested in pursuing cybersecurity education pathways in the Upper Peninsula region of Michigan. [Tampa, FL, January 10, 2022]: Northern Michigan University, an EC-Council Academia and ATC partner, hosted the YooperCon 2021 events in November for […]
Northern Michigan University’s (NMU) YooperCon event helped facilitate capture the flag (CTF) competitions and other cybersecurity awareness-focused sessions to support nearly 240 high school students interested in pursuing cybersecurity education pathways in the Upper Peninsula region of Michigan. [Tampa, FL, January 10, 2022]: Northern Michigan University, an EC-Council Academia and ATC partner, hosted the YooperCon 2021 events in November for […]