Networking
This article is based on Categories of Security Challenges in Cloud Computing Networking and their securities.
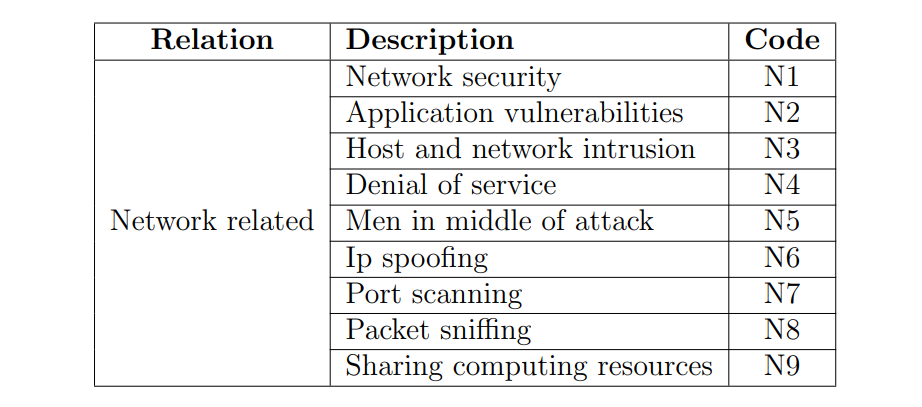
Network security (N1)
Information from articles that discuss network security and VPN network are considered.
Data should not be leaked while transmission and it is one of the requirements of information security [136]. To prevent leakage of sensitive information while transferring, a strong traffic encryption technique such as Secure Socket Layer (SSL) and Transport Layer Security (TLS) is required, and discuss network security and a VPN network. Sensitive data are obtained from enterprises, processed by any service application, and stored at the service vendor end. Amazon Web Services (AWS), provide more protection to its users from traditional network-based attacks like MITM (Man-In-The-Middle) attacks, IP spoofing, port scanning, packet sniffing, etc. The Assessment tests to find vulnerabilities in security are based on the following [144]:
- Network penetration and packet analysis
- Session management weaknesses
- Insecure SSL trust configuration
VPN network: If an organization is distributed globally and employs a single vendor, then the such organization might experience lower transfer rates when sending a file from one side to another side. A solution to this is the usage of Virtual Security Gateway and maintaining multiple vendors, for implementing this usage of some commercial solutions that give customer-controlled security in a cloud is necessary. This helps to establish a bridge over private infrastructure, where control over the cloud lies within the organization. It enables confidential leverage over the cloud for redundancy, scalability, and failover during critical transitions, which may lead to scale up grow or scale down to the organization or business [3].
Given below are some of the network attack types, concerns, and suggestions that various authors mention that can be aggregated under network security:
• The author in [14] mentions how challenging it is to identify the intrusion severity in CC.
• Author of [90] mentions attack methods such as phishing, fraud, Denial of Services (DoS), and account hijacking that are used to steal user credentials.
• The authors of [51] mention that using traditional network-based methods such as IPSec proxy encryption and digital signature, and key exchange through SSL proxy which is still being used in the cloud is insecure. The authors mention vulnerabilities of using such methods in the article by considering Amazon Web Services (AWS), Azure, and Google App Engine (GAE) as examples.
• Attack types mentioned in [169] launching dynamic attack points, key and password cracking, hosting malicious data, botnet command, and control, DDOS, building rainbow tables, and also CAPTCHA solving farms.
• The author in [134] mentions, backdoors, TCP hijacking, replay, social engineering (where the attacker tries to gain private information from the user’s social behavior), dumpster diving (information from the trash can be helpful), password guessing, trojan horses and malware are some of the network attacks mentioned.- Metadata spoofing is another kind of attack where a new system similar to cloud system can be built by analyzing and re engineering from metadata
- Account or service hijacking [17][5][110]. In addition to these Dos, IP address modification helps malicious users to hack into accounts.
- Some attack types that are specific to IaaS are DDOS, MITM, port scanning and IP spoofing [38]. The author of [164] points out network security, transport security as key security issues for IaaS in CC.
- Side channel attacks and incident handling [110]. SQL injection and phishing by service provider [7].
- The problems account or service hijacking mentioned above affects public and not private cloud [142].
In addition to all these kinds of attacks, the author in [75] mentions that even the cloud firewalls are still in a chaotic state. From all the attack types and points put before us there is a strong requirement for security measures, anyone’s credentials can be stolen easily with all these different types of security risks pointed out. If an attacker can gain access to someone’s credentials, he or she can eavesdrop on a customer’s activity, and transactions and also become a huge threat to the user’s data [51]. Server-side protection which includes application security and virtual server should also be provided to strengthen network security
Application security (N2)
Information from articles that discuss web application security, API security, application vulnerabilities, and application security is considered. With new advantages cloud also brings developers novel vulnerabilities and threats related to APIs [5]. It is known that in the cloud, any application or software that is used lies but not with the actual user, and if this software/application has vulnerabilities then it can have a decremental impact on all the customers using the cloud [142][17][164]. If the insecure APIs are not secured the vulnerabilities in that can lead to compromising security, can also lead to men in the middle of attacks, and affect the availability of CC [166][169][139]. Security surveys bring to notice that application-level attacks are more bandwidth efficient compared to network-level attacks [65]. In [110] the author mentions insecure APIs as one of the top threats to CC. Traditional security mechanisms such as network firewalls, network intrusion detection, and prevention mechanisms do not adequately satisfy being used as a solution [70]. The typical issues arising with Applications technology are Session riding, hijacking, and injecting vulnerabilities. Other web-application-specific vulnerabilities are the browser’s front-end components in which, data sent from the user component to the server component is manipulated [144]. The author of [31] also mentions that modern browsers compatible with AJAX are not secure though it’s good for I/O and data encrypted by XML needs to be also encrypted by using transport layer security. XML signature attacks and browser-based attacks for cloud authentication are a few other insecurities in application security that can be used for cloud authentication [80]. One easy way of accessing the cloud for an intruder is to search for saved passwords in history which can be a huge risk and use insecure browsers [123]. Hence securing the browser is necessary to secure transactions between users and their applications that are stored in the cloud [92]. Application security is the main threat to the SaaS platform [164]. In the article [142] author mentions that both public and private clouds are affected by insecure applications
Host and Network intrusion (N3)
This problem arises in PaaS, where control might be given to the user by SP to some extent. Service providers should keep in mind that control below the application level, such as host and network intrusion shall not be given to the user and the provider should maintain inaccessibility between applications [144]. Using programs such as trojan horses and malware which leak Sensitive data can help intruders to gain access to sensitive information
Denial of service (N4)
Denial of service attacks is possible in the cloud which can be a threat to data under transmission [32][136][169] [105]. Unlike bypassing preventive and security measures the attacker uses methods such as packet splitting, payload mutation, shell-code mutation, and duplicate insertion [65]. The three proposed distinctions are:
• Direct denial of service: If the workload becomes high in the cloud computing operating system, the environment will automatically allocate more computational power (more service instances, more virtual machines) to overcome this additional workload. But since resources are limited with service providers even providing additional resources for an extended amount of time is not quite possible. In such a case (flooding scenario) the cloud system is not working against the attackers (providing more computational power) but to some extent system is giving attackers the right to do damage to the service’s availability, starting from a single flooding attack. The attacker to cause disturbance does not need to attack ‘n’ servers, an attacker can target one of the cloud-based addresses to attack ‘n’ servers, and perform full loss of availability [80][67].
• Indirect denial of service: In-direct denial of service, attackers damage the availability of a service. If an instance in a cloud service is flooded with too much workload, other services running on the same cloud server might face issues with availability. If resources are completely utilized by a single instance, another instance has to face the consequence and wait for resources to be allocated.
Depending on the level of sophistication, if a cloud service provider notices a lack of availability and tries to “evacuate”, affected instances onto other servers the complexity rises even further. The reason for over-complication is, the flooding attack which existed in the previous server will now get extended to the server where it is transferred and this situation is called “jump over” [79][80]. In the worst case, to manage flooding attacks utilization of another cloud computing system is suggested. In that case, the cloud should provide more computational resources, respectively fending, until it reaches the full loss of availability
• Distributed Denial of Service (DDoS): This is even more dangerous and difficult to identify or control. In this type of attack, the attacker floods the target servers by controlling a large group of geographically distributed hosts. Since Cloud is shared by a large group of users, DDoS could have a greater impact on customers
Men in middle of attack (N5)
Attackers create an independent connection that relay on the messages between the user and the provider. The attacker makes the user and provider believe that this connection is secured and makes them talk directly, but behind the scene, the attacker controls the whole connection and receives every message which is sent between them (user and provider) [159][46][100]. The attacker can also possibly modify the message before sending it to the respondent [134]. XML signature wrapping is one such attack where the attacker without changing the header modifies the data in it and sends it to the receiver [31]. This makes it clear that in cloud computing, while data is in a transfer state denial of service is a Threat.
IP Spoofing(N6)
Using somebody’s IP address and creating TCP/IP packets is called IP spoofing. In this scenario, the intruder gains access to the trusted system and sends messages as if the trusted host is sending these messages. Here the malicious user impersonates the actual user with the help of an IP address [169][134]. Amazon EC2 cannot send instance spoofed network traffic. A firewall designed in the amazon web server prohibits an instance from sending messages with any other IP address or MAC address other than its own.
Port scanning (N7)
A port is a place from which data goes in or out of a system. When a system’s security fields are configured to send or receive data through a port. Then that specific port is vulnerable to port scan. When a network is scanned for vulnerabilities port scanning shows these vulnerable ports as open doors. When a computer tries to access the internet, a port is opened by default and it is not possible to stop port scanning [130][46]. This can cause security breaches in cloud computing platforms.
Packet Sniffing (N8)
Packet sniffing is listening to network devices and capturing raw packets [169]. If the software finds a packet suiting particular criteria, it logs into a file (login and password may be mandatory and significant ones). A virtual instance running in promiscuous mode can’t receive or “sniff” traffic that is intended for a different virtual instance. The hypervisor will not deliver any traffic when customers place their interfaces into promiscuous mode. If two virtual instances are determined on the same physical host and are owned by the same customers then they cannot listen to each other’s traffic. For Amazon EC2 attacks such as Address Resolution Protocol (ARP) cache poisoning do not work at all. Protection is provided by Amazon EC2 against a customer who is attempting (maliciously) to view another’s data, sensitive traffic should be encrypted by customers as a standard practice.
Sharing computing resources (N9)
Sharing technology is a top threat to cloud computing because it inherits all the problems that are possible with sharing resources in stand-alone systems [5][17][110][71]. In the world of the cloud, computing information is stored in data servers that are globally distributed. This cloud computing architecture is supported by virtual machines that run on hypervisors [90]. Due to this, the user will lose control of physically securing data and this might result in security risks because this data is stored in a location where resources (storage, computational resources, etc.,) are shared with some other Organizations [119][34]. Sharing resources between different projects and products and remote storage and processing of data can be beneficial but there are also some risks (such as how data is handled and misuse in command) and can complicate computation (i.e., monitoring, analysis, and reporting for company needs) [50][169][123]. In addition to the complications, there are various challenges that the author mentions need immediate attention when sharing computing resources, such as for tenant-isolation, customer-specific application customization, etc., that can affect customers if not using proper measures [50]. The issues that arise with shared technologies affect both public and private clouds.
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com