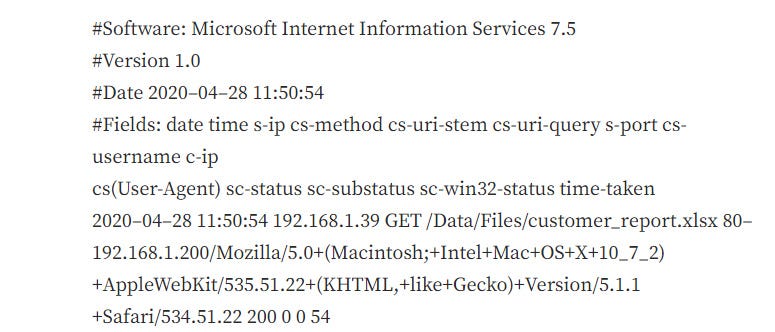
How to Crack Entry-Level Cybersecurity Jobs with No Experience
| Cybersecurity Technician Revenue in the cybersecurity market is projected to grow by 9.63% in 2023, resulting in a volume of 256.5 billion USD in 2028. (Statista, 2023). Market analysis projects a bright future for cybersecurity, making it an attractive choice for aspiring professionals today. Furthermore, with employers offering lucrative compensation for entry-level cybersecurity jobs,…
The post How to Crack Entry-Level Cybersecurity Jobs with No Experience appeared first on Cybersecurity Exchange.