March 30, 2023
CHFI v10 Practice Test (Full 600+ Questions)
https://www.udemy.com/course/chfi-v10-certmaster-exam-prep/?referralCode=79DFFB9D994A3B22461A
- A forensic examiner encounters a computer with a failed OS installation and the master boot record (MBR) or partition sector damaged. Which of the following tools can find and restore files and information in the disk?
A
Helix
B
Wireshark
C
NetCat
D
R-Studio
Correct answer are Helix. It is a digital forensics toolkit that can be used in such situations. It contains a suite of tools, including data recovery tools, that can help in recovering files and information from a damaged disk, even with a damaged MBR or partition sector. However, it is important to note that Helix is no longer actively maintained or updated.
So, while Helix can be used for this purpose, R-Studio remains a dedicated and powerful data recovery software, which is still actively maintained and updated. Both options can potentially help a forensic examiner in this scenario, but R-Studio might be a more focused and up-to-date choice for data recovery.
2. Recently, an internal web app that a government agency utilizes has become unresponsive. Betty, a network engineer for the government agency, has been tasked to determine the cause of the web application’s unresponsiveness. Betty launches Wireshark and begins capturing the traffic on the local network. While analyzing the results, Betty noticed that a syn flood attack was underway. How did Betty know a syn flood attack was occurring?
Wireshark capture shows multiple ACK requests and SYN responses from single/multiple IP address(es)
Wireshark capture does not show anything unusual and the issue is related to the web application
Wireshark capture shows multiple SYN requests and RST responses from single/multiple IP address(es)
Wireshark capture shows multiple SYN requests and ACK responses from single/multiple IP address(es)
Betty could determine that a SYN flood attack was occurring because the Wireshark capture showed multiple SYN requests being sent to the web application without corresponding ACK responses. This is a common indicator of a SYN flood attack, where an attacker sends a large number of SYN requests to overwhelm the target system and cause it to become unresponsive.
Correct answer is Wireshark capture shows multiple SYN requests and ACK responses from single/multiple IP address(es)
3. You are working as an independent computer forensics investigator and received a call from a system administrator for a local school system requesting your assistance. One of the students at the local high school is suspected of downloading inappropriate images from the Internet to a PC in the computer lab. When you arrive at rgb the school, the system administrator hands you a hard drive and tells you that he made a “simple backup copy” of the hard drive in the PC and put it on this drive and requests that you examine the drive for evidence of the suspected images. You inform him that a “simple backup copy” will not provide deleted files or recover file fragments. In this scenario, what type of copy do you need to make to ensure that the evidence found is complete and admissible in future proceedings?
Full backup copy
Incremental backup copy
Bit-stream copy
Robust copy
Correct answer is Bit-stream copy
In this scenario, a bit-stream copy is needed to ensure that the evidence found is complete and admissible in future proceedings. A bit-stream copy creates an exact duplicate of the original hard drive, including deleted files, slack space, and unallocated space. This type of copy is essential for forensic investigations, as it preserves all the data on the drive, allowing for a thorough examination and ensuring the integrity of the evidence.
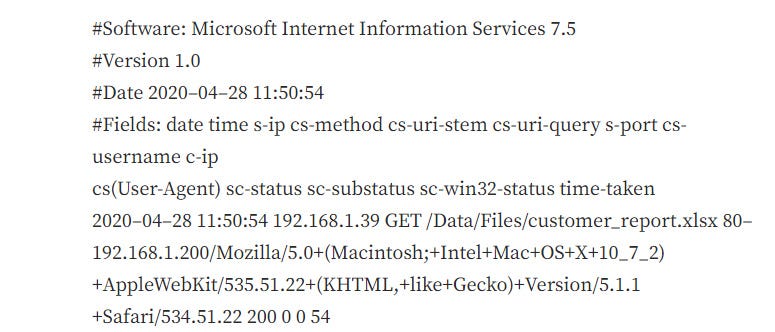
4. You are an information security analyst for a national retain chain. The organization has a web server which provides customer reports to internal users for marketing purposes. You are analyzing IIS logs on the web server and find the following log entry:

Based on the contents of this log entry, what occurred?
A user at IP address 192.168.1.200 requested the customer_report.xlsx file and the web server at IP address 192.168.1.39 processed the request
A user at IP address 192.168.1.39 requested the customer_report.xlsx file and the web server at IP address 192.168.1.200 processed the request
A user at IP address 192.168.1.200 requested the customer_report.xlsx file and the web server at IP address 192.168.1.39 failed to process the request
A user at IP address 192.168.1.39 requested the customer_report.xlsx file and the web server at IP address 192.168.1.200 failed to process the request
Correct answer : A user at IP address 192.168.1.200 requested the customer_report.xlsx file and the web server at IP address 192.168.1.39 processed the request
The log entry shows that a GET request was made for the customer_report.xlsx file by a user with IP address 192.168.1.200. The web server with IP address 192.168.1.39 processed the request, and the status code 200 indicates that the request was successful.
5. Chloe is a forensic examiner who is currently cracking hashed passwords for a crucial mission and hopefully solve the case. She is using a lookup table used for recovering a plain text password from cipher text; it contains word list and brute-force list along with their computed hash values. Chloe is also using a graphical generator that supports SHA1.
a. What password technique is being used?
b. What tool is Chloe using?
a. Brute-force b. MScache
a. Cain & Able b. Rten
a. Rainbow Tables b. Winrtgen
a. Dictionary attack b. Cisco PIX
Correct answer :
Chloe is using Rainbow Tables as her password cracking technique and the tool she is using is Winrtgen.
a. Rainbow Tables: Rainbow Tables are a time-memory trade-off technique used in password cracking. They are precomputed tables that allow recovering a plaintext password from a given hash value. These tables are generated by calculating the hash values for a large number of possible plaintext passwords, which can be compared to the target hash value to find a match. Rainbow Tables are efficient in cracking hashes because they save time compared to brute-force or dictionary attacks, but they require more storage space for the precomputed tables. They are particularly effective for cracking hashed passwords when the hashing algorithm is known (in this case, SHA1).
b. Winrtgen: Winrtgen is a Windows-based graphical generator for creating Rainbow Tables. It supports various hash algorithms, including SHA1, which is the one Chloe is using. The tool allows users to customize the character sets, chain lengths, and other parameters for the Rainbow Tables they generate. Once the tables are generated, they can be used with password cracking tools to recover plaintext passwords from their hashed values.
https://www.youtube.com/watch?v=G8RUz4CSeXY
6. Smith, a network administrator with a large MNC, was the first to arrive at a suspected crime scene involving criminal use of compromised computers. What should be his first response while maintaining the integrity of evidence?
Switch-off the systems and carry them to the laboratory
Perform data acquisition without disturbing the state of the systems
Record the system state by taking photographs of physical system and the display
Open the systems, remove the hard disk and secure it
Correct answer : Smith’s first response while maintaining the integrity of evidence should be to:
Record the system state by taking photographs of the physical system and the display.
It is crucial to document the initial state of the systems before taking any further action. This includes taking photographs of the physical setup, computer screens, and any other relevant peripherals. This will help preserve the context of the scene and provide a reference point for future analysis. Only after proper documentation should Smith proceed with other steps, such as data acquisition or securing hardware, under the guidance of digital forensics experts.
7. An investigator is examining a file to identify any potentially malicious content. To avoid code execution and still be able to uncover hidden indicators of compromise (IOC), which type of examination should the investigator perform:
Static analysis
Threat hunting
Dynamic analysis
Threat analysis
The investigator should perform:
Static analysis
Static analysis involves examining the file’s content, structure, and properties without actually executing the code. This approach helps the investigator identify potentially malicious content, such as suspicious patterns, embedded resources, or indicators of compromise (IOC), without risking code execution that could compromise the system or environment.
8. An investigator needs to perform data acquisition from a storage media without altering its contents to maintain the integrity of the content. The approach adopted by the investigator relies upon the capacity of enabling read-only access to the storage media. Which tool should the investigator integrate into his/her procedures to accomplish this task?
Data duplication tool
BitLocker
Backup tool
Write blocker
The investigator should integrate a:
Write blocker
A write blocker is a tool designed to allow read-only access to storage media, ensuring that the contents of the media are not altered during the data acquisition process. By using a write blocker, investigators can maintain the integrity of the evidence while preventing any modifications to the original data.
9. The Recycle Bin exists as a metaphor for throwing files away, but it also allows a user to retrieve and restore files. Once the file is moved to the Recycle Bin, a record is added to the log file that exists in the Recycle Bin. Which of the following files contains records that correspond to each deleted file in the Recycle Bin?
LOGINFO2
INFO2
LOGINFO1
INFO1
When a file is deleted, the complete path of the file and its name is stored in a hidden file called INFO2 ( in Windows 98) in the Recycled folder.
The INFO2 file is a hidden system file located within the Recycle Bin folder on Windows operating systems. It is used to maintain metadata associated with each deleted file that has been moved to the Recycle Bin. The INFO2 file helps the system track and manage these deleted files, allowing users to restore them if needed.
When a file is deleted and moved to the Recycle Bin, a record is added to the INFO2 file. This record contains information such as the original file path, the file’s deletion date, and a unique identifier for the deleted file. If a user chooses to restore a file from the Recycle Bin, the operating system refers to the INFO2 file to locate the original file path and move the file back to that location.
It is important to note that the INFO2 file is specific to older Windows operating systems like Windows XP. In newer versions of Windows, the Recycle Bin metadata is managed differently, using the $I and $R file pairs.

10. A computer forensics investigator or forensic analyst is a specially trained professional who works with law enforcement as well as private businesses to retrieve information from computers and other types of data storage devices. For this, the analyst should have an excellent working knowledge of all aspects of the computer. Which of the following is not a duty of the analyst during a criminal investigation?
To fill the chain of custody
To dismantle and rebuild the system when the data is damaged
To enforce the security of all devices and software in the scene
To recover data from suspect devices
The option that is not a duty of the analyst during a criminal investigation is:
To dismantle and rebuild the system when the data is damaged
A computer forensics investigator’s main responsibilities during a criminal investigation include collecting, preserving, and analyzing digital evidence, maintaining the chain of custody, and recovering data from suspect devices. Dismantling and rebuilding a system when the data is damaged is not a typical responsibility of a forensic analyst, as their primary focus is on preserving the integrity of the evidence and avoiding any potential alterations or damage to the original data. In cases where data recovery is necessary due to damage, forensic analysts may collaborate with data recovery specialists or use specialized tools and techniques to extract data without compromising the integrity of the evidence.
CHFI v10 Practice Test (Full 600+ Questions)
https://www.udemy.com/course/chfi-v10-certmaster-exam-prep/?referralCode=79DFFB9D994A3B22461A
Article posted by: https://certmaster.me/1-a-forensic-examiner-encounters-a-computer-with-a-failed-os-installation-and-the-master-boot-70d233cdb515?source=rss-d9e5f258a4e8——2
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com