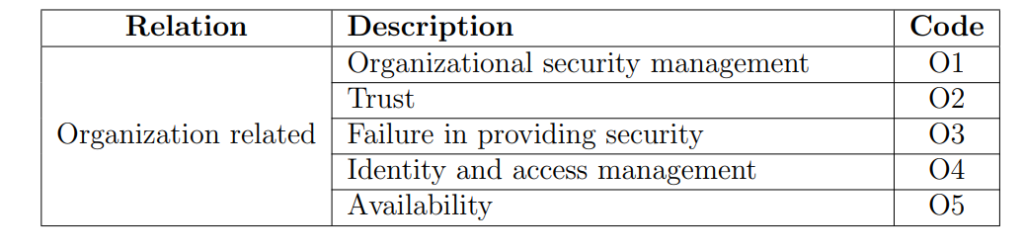
Organizational security management (O1)
When adapting to cloud computing, some changes are introduced to the security management, information security lifecycle models, even the corporate IT standards and policies need to be changed [160]. There are issues such as less coordination among different communities of interest within client organizations.
The customer also has to face new risks introduced by perimeter-less environment, such as data leakage due to multi-tenancy, issues like local disasters and provider’s economic instability. But since the cloud computing environment is distributed in nature, re-evaluate best practices and adoption of secure cloud
computing applications become extremely complex as they require to have a well structured cyber insurance [146]. Another way is to adjust to the new features
provided by the cloud computing else gaining complete benefit from CC would not be possible [50]. Some point needed to be considered and as follows:
• Will proprietary interfaces used to administer services provided be accessible? [65]
• Security models must be assessed in detail [142].
• Gather and manage security related information on non native interfaces such as CC is important [91].
• Some organization policy and legislations are non compliant with CC, example enterprise network which uses NAT (Network Address Translation) and company specific firewalls and is not easy to integrate with CC
Trust management and Policy integration (O2)
Trust is the key problem in the CC environment as CC is not completely trustable for users [164][136][67]. An organization using cloud computing application has to give some of its critical information to use certain services provided by the cloud service provider. For this organization needs to develop trust in remote execution/storage and placing sensitive data in the cloud is tough as the company feels that its loosing control over data and there is much less transparency
in cloud [89][77][4][32]. Lack of this control is leading to distrust in CC [123].
The remote execution in CC is carried out based on some policies and principles. There are evidences that even though the policies at individual domains remain verified, the violation is still possible to occur at integration that needs to be taken care of or have some attention. Hence, there is a need for a trust based secure interoperation which helps in managing trust and support policy integration [146]. Insider access, data stored or processed outside organizational boundaries and security controls are some features which when used with Cloud Computing could have some inherent risks. Threats that arise with the insider access are well known for various organizations. Its influence over cloud computing has not at all changed [78][84]. These threats could be raised by a user or a third party organization that was given access to a part of application in the cloud. These threats could result in theft of critical information or various types of frauds [78]. The CSA mentions that violation in cloud can be caused by a third party provider when it tries to access users data stored in the cloud [7]. The author for [4] mentions that trust in customers can be increased when SP develops trust worthy tools, automated processes for working in cloud and methods that establish healthy connections between user and provider. The author also mentions other attributes of CC such as, compositional chain of trust, trust re-evaluation and transparency vs trust evaluation [4]. The author of this article illustrates multiple examples of possible threats and possible security measures [179]. Since there are no extensible trust building models available in CC, SLAs should be monitored and enforced properly as they are one way to build trust between user and provider [38][64]. Mutual auditing users/providers in the CC will help in increasing trust and assurance on others in the cloud [110]. In article [148] author suggests a need for trust building approach to negotiate, establish and maintain trust. He mentions that this should adaptively support policy integration. The author poses some questions that need to be answered [148]:
- How to manage and maintain dynamically changing trust values
- How to adapt to the access requests as trust keeps evolving
- The most important one, how to establish trust and determine assess Mapping which satisfies inter-domain access requirements
Failure in providing security (O3)
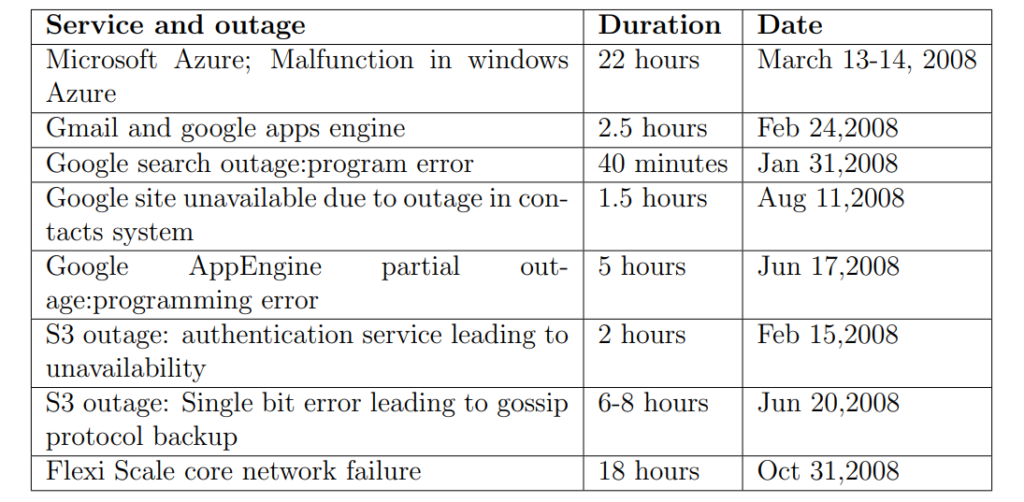
Information from different articles that discuss about fault tolerance and failure in providing security are considered. Failure in providing security to the infrastructure under control of cloud provider can result in compromising subscriber’s security. Even a single weak link in cloud computing can cause a security threat to Multiple Entities connected in it. For customer to secure his data, he/she should believe in service provider’s security [154][87][46]. It is evident that customer must also have trust in providers security. For a cloud to be trusted and considered strong simple but yet important features such as logging, security policies ,incident response, etc., should also be strong [90]. A third party poor management can lead to damaging the provider and also the user indirectly [138]. In addition to the above discussion, article [127] gives us a few examples that are tabulated in table 4.5, which exemplify different cloud failures.
Identity and access management (O4)
Information from articles that discuss about identity Management system, identification, identity and access management, identity provisioning (Independent IDM stack, credential synchronization and federated IDM) are considered. Identity management is an administrative process area, where all users of
a system are identified (entities), and by enforcing some restrictions on these entities access to resources in that system are controlled [144]. Since this plays a
key role in securing Cloud Computing (CC) environment access should be given only to privileged users, which should also be blackened by physical monitoring and background checking [92]. The major concern in this is how complex it is to manage a diverse population of users, and provide access to internal and external services in a constantly changing environment (changes can happen due to change in business needs/processes) [104]. It is also true that need for fine grained access control on the information stored on CC is increasing and since CC is vast satisfying these needs and meet growing requirements has become complicated [170]. For this there are various mechanisms but not all are up to the satisfaction of users [170]. The browser based authentication protocols are not secure as they cannot issue XML based security tokens [75]. In addition to this, organizations may contain complex web of user identities, access rights and procedures.
Author of [126][105] says access control in CC is an issue and it is necessary that a user is able to view only the portion of data he is given access. Access
control models should also be able to a pick out relevant areas of SLA and change access rights accordingly [148]. Generally organizations give access to its employees based on principle of least access, where access is given to only those services to which he/ she needs basic access [119]. Identity is the core of any system and to have a manageable control on users and identify breaches, there are various areas need to be considered: “Identity Provisioning and deprovisioning, identity information privacy, identity linking, identity mapping, identity federation, identity Attributes federation, single sign on, authentication and authorization” [6].
Identity management can be done in three different ways [144]:
• To just create, manage and delete entities without regard to access or knowledge regarding the access rights of the entity. This is known as a pure identity paradigm.
• Access can be provided to users with the help of some smart cards or a traditional scheme of authenticating. This enables user to log on to a system
for accessing a service or services, which is other way, called as the user access (log-on) paradigm.
• Providing access to users on various devices based on different distinctions such as Role based, online, on-demand, multimedia content and presence
based, is termed as a service based paradigm. A traditional way of having control over an application was to keep track of collection of users and manage them and they are still not sufficient in CC [170][112].
This system is no longer easy as sharing of Personal Identifiable Information (PII) is not suggested because doing so can cause a breach to privacy. The PII is the information that a user sends to Service Provider (SP) to authenticate it. PII differs from user to user [124][18]. Some suggested methods for managing identities are [144]:
• Independent IDM stack: In this system, all information related to user accounts, passwords, etc., is stored with the Cloud Service Provider (CSP)
and it provides management and sign on services.
• Credential synchronization: In this system, user account information is replicated between enterprise and service provider. The user account information is done at each guest who pays for the services provided by the CSP. This replication is done at each user based on their company regulations. Replication also considers relevant portions of user credentials at the CSP to provide sign on and other access control features for services used in CC.
• Federated IDM: Within this kind of system, user credentials are stored and managed at the enterprise itself. Authentication is done in enterprise
boundary itself and if necessary, certain attributes are communicated to the CSP [144][165]. Another issue here is that companies having a strong IDM system might not be able to extend its functionalities on CC or change the existing framework to support this new architecture of cloud [148]. To separately maintain a different authentication for internal (organization authentication) and external (authentication at SP’s end) is a complex solution to this problem [78]. To nullify the effect of these challenges on CC, systems need to find possible breaching zones/areas before they cause some impact. Given below are some assessment test to validate the security in IDM [144]:
• Authentication weakness analysis
• Insecure trust configuration
The author in [90] explains a special case, by taking an example of a employee with malicious intent, working in a company which provides CC services. This
employee can easily gain access to secure areas and perform malicious activities which could be difficult for outsiders. The impact of this employee could be severe if this employee is not identified by the service provider. Supporting the previous example, article [142] mentions that more than 67% of respondents in a survey by CERT insider threat center 2010 cyber security watch survey admitted that insider incidents are the costliest. The author also suggests to use a insider security policy to avoid insider attacks [142]. The author for [166] expresses that insider attacks are alarming and this might happen when security standards provided by SP do not meet the standards used by customer’s standards. The author of [109] mentions that one third of breaches happen form lost or stolen devices and from employees sharing their data accidentally on the internet and nearly 16% due to insider threat. This issue of malicious insider has also been mentioned in following articles [17][5][105]. Not only there is an insider threat but even a malicious user might gain access to CC and deploy malware if he can produce a stolen credit card from legitimate user [138]. These insider threats or entry for a hacker or malicious insider is easy because SPs don‘t give customers transparency into security in CC. Inefficient access and identity management can lead to illegal service process, fabricated services process and malicious service interruption [32]. The author for [43] also mentions various types of insider and the impact and also mentions that it can be dangerous if go unattended. Article [91] mentions Identity management, credential management, attribute management, privilege management, cryptographic key management as security management areas in CC.
Authentication and authorization: Most companies store their employee information in some kind of Lightweight Directory Access Protocol (LDAP), Small
and Medium Business (SMB) companies which have SaaS as their highest adoption rate seem to use ‘Active Directory’ as the most popular tool for managing users. In case of SaaS, the user credentials get stored multiple times in provider’s databases, because SaaS requires the user data to be stored in SP’s data repositories. To avoid misuse SaaS customers should remember to remove/disable accounts or create/enable as employees leave or join the company [144].
Authentication and identity management: Identity management and authentication is being realized as a critical requirement in CC [66][163]. Users can be
authenticated based on service based credentials and characteristics using identity management (IDM) mechanism. This system is supposed to protect private
and sensitive information related to users and processes [162]. In multi-tenant cloud environments customer’s identity and authentication information should
be segregated. These components need to be easily integrated table with other security component. It is not clear yet on how multi-tenant cloud environments
can effect privacy of information [146].
Most of the service providers use Security Assessment Mark-up Language (SAML) in administering and authenticating user before giving access to resources. This language provides an interface where information related asserting subjects or authentication information is exchanged between cooperating domains. SAML request and response messages are mapped over Simple Object Access Protocol (SOAP) which in turn depends on extensible Mark-up Language
(XML) for formatting. This SOAP message security validation can become complicated and threat prone. As this SAML depends on XML, there are some
evidences where wrapping attacks on XML were successful and in turn that can be effecting SOAP message. This in turn can become a threat to the SAML
authentication procedure [78]. The detailed description on challenges with implementation of other modes of authentication such as, single sign-on, OpenID,
RBAC, etc., are given in [66].
Given below are some cloud specific issues mentioned in [62] article:
• Denial of service by account lockout: The most general way of authenticating a user is by username and password. To avoid misusing an account,
after a certain numbers of failed attempts an account is locked. This feature can be used by an attacker to launch a Denial of Service (DoS) attack
against an authorized user
• Weak credential-rest mechanism: Password recovery mechanism prevailing is proven to be weak, if a Cloud computing (CC) provider manages user
credentials manually than using a federated authentication, there should be a method provided for resetting credentials in case of lost or forgotten
credentials.
• Insufficient or faulty authorization checks: Web applications and service cloud are vulnerable to faulty or insufficient techniques of verification that
can make users access unauthorized information. URL guessing attacks are the outcome of missing some authorization checks, the user can modify
URL’s to display other user’s information.
• Coarse authorization control: Cloud service management interface needs to offer the authorization control models, which are still not refined. This
makes standard security mechanism (duty separation) not so easy to be implemented in a cloud environment.
• Insufficient logging and monitoring: Present day cloud has no standards or mechanisms that can help customers to monitor and log data within cloud
resources. This can cause problems when the log file needs to be searched for a single tenant and also there is not all possibilities from CSP’s side to
monitor user’s data.
Authorization and authentication is an important information security requirement on which cloud architecture designer must concentrate and build a
secure and trusted cloud computing infrastructure [123][8]. Inefficient authorization mechanism can cause side-channel attacks in the cloud [8]. The author in
[171] gives an example of a special case where two parties using the cloud as a medium for transferring applications/code/information, only the target user is
supposed to get access to the piece of program but with the help of an insider (an employer in cloud) the target user can create another copy of the same code and sell it. This is a copyright issue which can cost the developing company. Traditional encryption, hashes or access-control labels can not help to avoid this.
Which gives an example that shows if access management is not given enough importance a user who is not fit for having access to a part of the transaction can misuse his rights and cause damage to customer. To avoid this proper monitoring should be done for employees in cloud.
Some suggestions to prevent illegitimate access are as follows:
• Mentioning human resource requirements as part of SLAs, transparency in overall information security and management practices, compliance, reporting and determining a security breach notification method and the most important enforcing strict supply chain management are some suggestions given by CSA
• Before committing to a SP the customer must make a note about the privileged user access policies, know who will be gaining access to the data, how can it be accessed etc., [55][85][123].
• An effective and continuous monitoring system which detects malicious activity will be better than depending on firewall and security mechanism
Availability (O5)
Information from articles that discuss about availability, cloud provider goes down, job starvation due to virtualization, business continuity and service availability are considered. Availability is a primary concern for CC and is one of the key issues in information assurance [169][65][166][164]. Not being able to access services can become a serious issue [169]. It is evident in literature that the availability of a system is important and many organizations/researchers have their questions such as “if downtime occurs can the business still operate?” [162].
Availability of a system can be defined as, the extent to which an organization provides its user with round the clock service (resources accessible and usable)
is availability. There are chances of having a complete or permanent impact on the organizations when the availability of a system is affected. Denial of Service
(DoS) attacks, natural disasters and equipment outages are all threats to availability [78][134][31][100]. The cloud services also have experience in outages and
performance slowdowns; if not planned and designed properly customers using cloud computing services will be at loss. There are various examples illustrated
by [78], where the effect of shortcomings were borne by well-established organizations such as Twitter (in 2009), lighting storm caused some IaaS customers go
down (in July 2009), gmail (in 2008 for one day) etc., [78][35][7], these outages can also occur because of non-technical issues [13][12]. Service interruptions could also be due to malicious users/use [32]. If at all there is an outage or server crash all the VM, services running on that server become unresponsive, in addition to that high availability or automatic fail over or high availability is not possible in public cloud [138]. If an organization wishes to migrate its servers which is so vast that it has multiple data centers distributed over different geographical locations using a variety of network providers but with some common software service to connect with a cloud, in such situation the organization might not want to migrate to a new system without a good business continuity plan modeled. In this case, it is suggested to have a multiple service providers providing different stacks, such that if one stack fails there will be another stack (i.e., Service Provider) supporting as a substitute [13][12][72][116].
Generally CSP has to provide required application level scalability and availability, by making necessary changes to the applications at the architecture level and satisfy the customer requests. CSP can design specialized hardware and software to deliver higher reliability and earn an additional penny out of this [13][12].
CC should be constantly available with all the access control mechanisms and data access working [70]. To make this possible, a multi-tier architecture is deployed with a load balancing architecture running on a variable number of servers.
To enhance the availability of a system built in CC, it is also suggested to secure system for hardware/software failures and DoS attacks. For safeguarding data
from unplanned emergencies or minimizing enterprise downtime there is a need to have an appropriate plan for Business Continuity (BC) and Disaster Recovery (DR). For example the amazon API’s use a Standard Distributed Denial of Service (DDoS) mitigation techniques such as synchronous cookies and connection limiting. Amazon also maintains a higher level internal bandwidth than supplied to its customer, to further ensure mitigation of DDoS attacks. To validate the vendor’s availability, given below are few tests [144]:
• Authentication weakness and
• Session management weakness
Another solution for maintaining availability is, securing the system by usage of a Trusted Third Party (TTP). TTP provides end to end security services
which are scalable across different domains and usable with different geographical areas. TTP’s are impartial organizations delivering business confidence through some technical security features and securing an electronic transaction. These TTP’s are generally connected through a chain of trust to provide a web of trust using the Public Key Infrastructure (PKI). PKI in a distributed information system becomes effective when combined with a directory (it is a set of similar
attributes organized in a hierarchical and logical way). The Light weight Access Protocol is internet’s (LDAP) general way of accessing a directory service. In CC
environments PKI used in combination with Single Sign On (SSO) mechanism is ideal as they provide smooth and transparent authentication across various
physical resources. The reasons for depending on TTP’s are as follows [179]:
• Low and High level confidentiality.
• Server and Client Authentication.
• Creation of Security Domains.
• Cryptographic Separation of Data.
• Certificate-Based Authorization
Usage of TTP or any other method used for ensuring availability is generally mentioned through the Service Level Agreements (SLA). To ensure greater extent
of availability it is important to identify the right deployment and delivery model set out by the International Organization for Standardization (ISO) [123]. Usage of HTTPS+WS security can cause heavy load on the server leading to service break down (reasons for outages in google and amazon in 2008), there should be perfect balance between availability and security measures to keep services active
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com