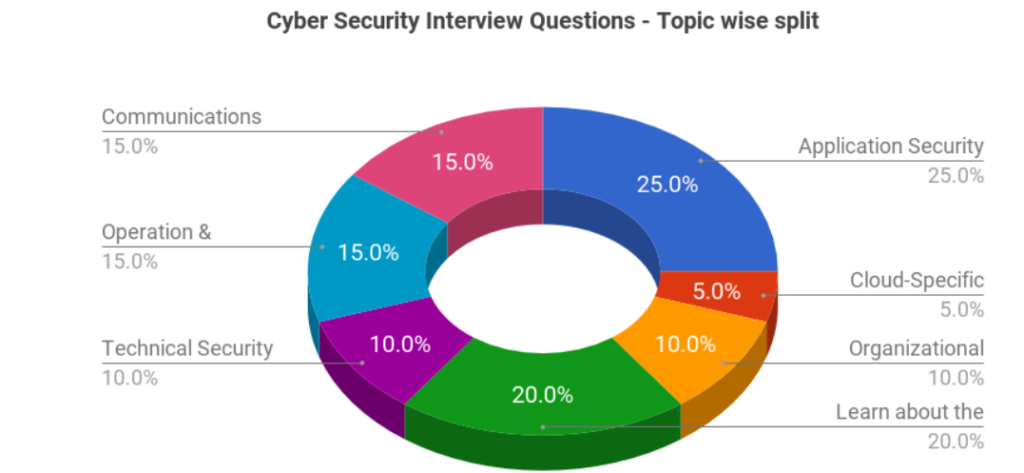
50 Cyber Security Interview Question & Answers For Sure Shot Success – Networking and Security
12. The world has recently been hit by ……. Attack/virus etc. What have you done to protect your organization as a security professional? Different organizations work in different ways, the ways to handle incident is Different for all. Some take this seriously and some not. The answer to this should be the process to handle …