- How do you keep yourself updated with the information security news?
TIP: Just in case you haven’t followed any: the hacker news Threat Post, Pentest mag etc. Be sure to check and follow a few security forums so that you get regular updates on what is happening in the market and about the latest trends and incidents.
12. The world has recently been hit by ……. Attack/virus etc. What have you done to protect your organization as a security professional?
Different organizations work in different ways, the ways to handle incident is Different for all. Some take this seriously and some not. The answer to this should be the process to handle an incident. Align this with one you had and go on… just don’t exaggerate.
13. CIA triangle?
Confidentiality: Keeping the information secret. Integrity: Keeping the information unaltered. Availability: Information is available to the authorized parties at all times.
14. HIDS vs NIDS and which one is better and why?
HIDS is host intrusion detection system and NIDS is network intrusion detection system. Both the systems work on the similar lines. It’s just that the placement in Different. HIDS is placed on each host whereas NIDS is placed in the network. For an enterprise, NIDS is preferred as HIDS is did cult to manage, plus it consumes processing power of the host as well.
Level 02 – Learners (Experienced but still learning)
15. What is port scanning?
Port scanning is process of sending messages in order to gather information about network, system etc. by analyzing the response received.
16. What is the Different between VA and PT?
Vulnerability Assessment is an approach used to find flows in an application/network whereas Penetration testing is the practice of finding exploitable vulnerabilities like a real attacker will do. VA is like travelling on the surface whereas PT is digging it for gold.
17. What are the objects that should be included in a good penetration testing report?
A VAPT report should have an executive summary explaining the observations on a high level along with the scope, period of testing etc. This can be followed by no of observations, category wise split into high, medium and low. Also include detailed observation along with replication steps, screenshots of proof of concept along with the remediation.
18. What is compliance?
Abiding by a set of standards set by a government/Independent party/organization. E.g. An industry which stores, processes or transmits Payment related information needs to be complied with PCI DSS (Payment card Industry Data Security Standard). Other compliance examples can be an organization complying with its own policies.
19. Tell us about your Personal achievements or certifications?
Keep this simple and relevant, getting a security certification can be one personal achievement. Explain how it started and what kept you motivated. How you feel now and what are your next steps.
20. Various response codes from a web application?
1xx – Informational responses
2xx – Success
3xx – Redirection
4xx – Client side error
5xx – Server side error
21. When do you use tracert/traceroute?
In case you can’t ping the final destination, tracert will help to identify where the connection stops or gets broken, whether it is firewall, ISP, router etc.
22. DDoS and its mitigation?
DDoS stands for distributed denial of service. When a network/server/application is flooded with large number of requests which it is not designed to handle making the server unavailable to the legitimate requests. The requests can come from different not related sources hence it is a distributed denial of service attack. It can be mitigated by analyzing and faltering the traffic in the scrubbing centers.
The scrubbing centers are centralized data cleansing station wherein the traffic to a website is analyzed and the malicious traffic is removed.
23. What is a WAF and what are its types?
TIP: This topic is usually not asked in detail.
WAF stands for web application firewall. It is used to protect the application by filtering legitimate traffic from malicious traffic. WAF can be either a box type or cloud based.
24. Explain the objects of Basic web architecture?
TIP: Different organizations follow different models and networks. BE GENERIC.
A basic web architecture should contain a front ending server, a web application server, a database server.
Level 03 – Master (Entered into a managerial position or sitting for one)
25. How often should Patch management be performed?
Patch should be managed as soon as it gets released. For windows – patches released every second Tuesday of the month by Microsoft. It should be applied to all machines not later than 1 month. Same is for network devices, patch as soon as it gets released. Follow a proper patch management process.
26. How do you govern various security objects?
Various security objects are governed with the help of KPI (Key Performance Indicators). Let us take the example of windows patch, agreed KPI can be 99%. It means that 99% of the PCs will have the latest or last month’s patch. On similar lines various security objects can be managed.
27. How does a Process Audit go?
The first thing to do is to identify the scope of the audit followed by a document of the process. Study the document carefully and then identify the areas which you consider are weak. The company might have compensatory controls in place. Verify they are enough.
28. What is the difference between policies, processes and guidelines?
As security policy defines the security objectives and the security framework of an organization. A process is a detailed step by step how to document that specifies the exact action which will be necessary to implement important security mechanism. Guidelines are recommendations which can be customized and used in the creation of procedures.
29. How do you handle AntiVirus alerts?
Check the policy for the AV and then the alert. If the alert is for a legitimate File then it can be whitelisted and if this is malicious File then it can be quarantined/deleted. The hash of the File can be checked for reputation on various websites like virus total, malwares.com etc. AV needs to be Fine-tuned so that the alerts can be reduced.
30. What is a false positive and false negative in case of IDS?
When the device generated an alert for an intrusion which has actually not happened: this is false positive and if the device has not generated any alert and the intrusion has actually happened, this is the case of a false negative.
You may also like: What are the Top 7 Security certifications?
31. Which one is more acceptable?
False positives are more acceptable. False negatives will lead to intrusions happening without getting noticed.
32. Software testing vs. penetration testing?
Software testing just focuses on the functionality of the software and not the security aspect. A penetration testing will help identify and address the security vulnerabilities.
33. What are your thoughts about Blue team and red team?
Red team is the attacker and blue team the defender. Being on the red team seems fun but being in the blue team is difficult as you need to understand the attacks and methodologies the red team may follow.
34. What is you preferred – Bug bounty or security testing?
Both are fine, just support your answer like Bug Bounty is decentralized, can identify rare bugs, large pool of testers etc.
35. Tell us about your Professional achievements/major projects?
This can be anything like setting up your own team and processes or a security practice you have implemented. Even if the achievement is not from a security domain just express it well.
36. 2 quick points on Web server hardening?
TIP: This is a strong topic, get over with the exact answer and carry on the conversation over the lines.
Web server hardening is filtering of unnecessary services running on various ports and removal of default test scripts from the servers. Although web server hardening is a lot more than this and usually organizations have a customized checklist for hardening the servers. Any server getting created has to be hardened and hardening has to be re-confirmed on a yearly basis. Even the hardening checklist has to be reviewed on a yearly basis for new add-ons.
37. What is data leakage? How will you detect and prevent it?
Data leak is when data gets out of the organization in an unauthorized way. Data can get leaked through various ways – emails, prints, laptops getting lost, unauthorized photographs etc. There are various controls which can be placed to ensure that the data does not get leaked, a few controls can be restricting upload on internet websites, following an internal encryption solution, restricting the mails to internal network, restriction on printing confidential data etc.
Level 04 – Grandmaster (Senior management roles)
38. What are the different levels of data classification and why are they required?
Data needs to be segregated into various categories so that its severity can be defined, without this segregation a piece of information can be critical for one but not so critical for others. There can be various levels of data classification depending on organization to organization, in broader terms data can be classified into:
Top secret – Its leakage can cause drastic effect to the organization, e.g. trade secrets etc.
Confidential – Internal to the company e.g. policy and processes.
Public – Publicly available, like newsletters etc.
39. In a situation where a user needs admin rights on his system to do daily tasks, what should be done – should admin access be granted or restricted?
Users are usually not provided with admin access to reduce the risk, but in certain cases the users can be granted admin access. Just ensure that the users understand their responsibility. In case any incident happens, the access should be provided for only limited time post senior management approval and a valid business justification.
40. What are your views on usage of social media in office?
TIP: Keep an open mind with these kinds of questions.
Social media is acceptable, just ensure content filtering is enabled and uploading features are restricted. Read only mode is acceptable till the time it does not interfere with work.
41. What are the various ways by which the employees are made aware about information security policies and procedures?
There can be various ways in which this can be done:
- Employees should undergo mandatory information security training post joining the organization. This should also be done on yearly basis, and this can be either a classroom session followed by a quiz or an online training.
- Sending out notifications on regular basis in the form of slides, one pagers etc. to ensure that the employees are kept aware.
42. In a situation where both Open source software and licensed software are available to get the job done. What should be preferred and why?
TIP: Think from a security perspective and not from the functionality point.
For an enterprise, it is better to go for the licensed version of the software as most of the software have an agreement clause that the software should be used for individual usage and not for commercial purpose. Plus, the licensed version is updated and easy to track in an organization. It also helps the clients develop a confidence on the organizations’ software and practices.
43. When should a security policy be revised?
There is no fixed time for reviewing the security policy but all this should be done at least once a year. Any changes made should be documented in the revision history of the document and versioning. In case there are any major changes the changes need to be notified to the users as well.
44. What all should be included in a CEO level report from a security standpoint?
A CEO level report should have not more than 2 pages:
1. A summarized picture of the state of security structure of the organization.
2. Quantified risk and ALE (Annual Loss Expectancy) results along with countermeasures.
45. How do you report risks?
Risk can be reported but it needs to be assessed first. Risk assessment can be done in 2 ways: Quantitative analysis and qualitative analysis. This approach will cater to both technical and business guys. The business guy can see probable loss in numbers whereas the technical guys will see the impact and frequency. Depending on the audience, the risk can be assessed and reported.
46. What is an incident and how do you manage it?
Any event which leads to compromise of the security of an organization is an incident. The incident process goes like his:
- Identification of the Incident
- Logging it (Details)
- Investigation and root cause analysis (RCA)
- Escalation or keeping the senior management/parties
- Remediation steps
- Closure report.
47. Is social media secure?
TIP: This is another debatable question but be generic.
Not sure if the data is secure or not but users can take steps from their end to ensure safety.
- Connect with trusted people
- Do not post/upload confidential information
- Never use the same username password for all accounts
48. Chain of custody?
For legal cases the data/device (evidence) needs to be integrated, hence any access needs to be documented – who, what when and why. Compromise in this process can cause legal issues for the parties involved.
49. How should data archives be maintained?
Gone are the times when there used to be files and cabinets which held data over the years. This phase was long followed by archiving data over magnetic tapes and storing the tapes. There is another overhead for the maintenance and safety of the tapes. These are few conventional approaches, but the world is slightly moving to the cloud storage architecture. The only hurdle is the data privacy. Companies are not very sure about handing the critical data. This will actually take time but securely configured and managed cloud can be one of the best options.
50. What are your thoughts on BYOD?
There is no correct answer for this but just ensure that whatever side you are on, justify it with examples, scenarios and logic.
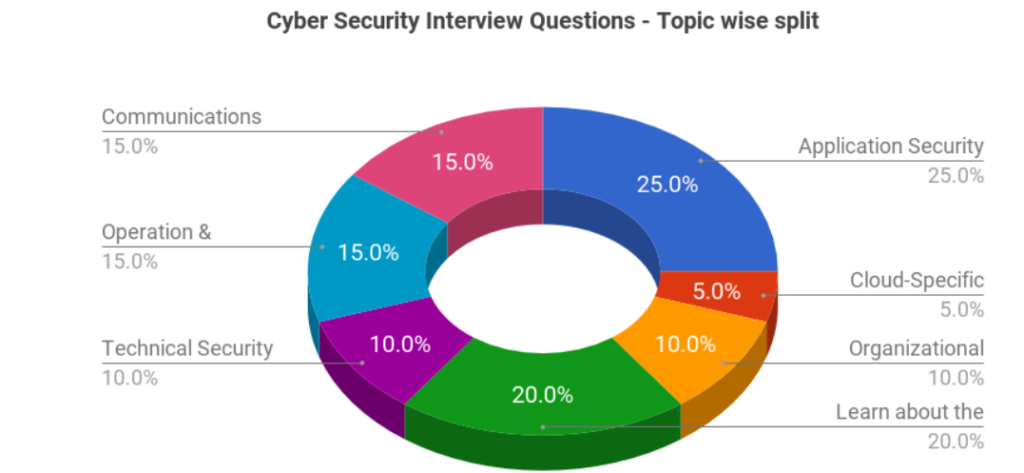
Although there is no defined scope and end to the questions, but having a strong foundation of the basic concepts and awareness about the latest trends will give you an upper hand in the interview.
TIP:
- BACKUP your answers with examples wherever
- Provide DETAILS, this will leave less chance for the interviewer to dig into details.
- BE PRECISE in what you say, LISTEN carefully, THINK and ANSWER.
- BE CONFIDENT with what you speak.
- MAINTAIN a good posture.
- BE AWARE about the security news, recent incidents, attacks etc.
- Remember the question and answer accordingly, DO NOT get deviated from the topic.
- Most importantly “KEEP A POSITIVE ATTITUDE” even if the interview is not going as you expected.
- Sometimes it is kept that way to check the attitude.
Not to miss, to be in a top shape for your cybersecurity interview being a certified ethical hacker is an essential hiring criterion.
Get trained by Cybersecurity Industry Experts
