Nowadays Kali Linux repository comes with OWASP Maryam Open-Source Intelligence (OSINT) Framework. Maryam Framework will be very helpful for penetration testers and cybersecurity experts. This is based on Recon-ng and written on Python3. This framework collects informations very intelligently from our given data and gather the informations in a systematic and structured way.
What is Maryam
Open-source intelligence (OSINT) uses open source tools to collect information and analyze them for a specific purpose. OSINT can be very helpful for cybersecurity experts to use to garner data about particular organizations.
Today, using Open sources like Bing, Google, Yahoo, etc, for data gathering, are essential steps for reconnaissance, which is a common task. It should be a tool to automate this routine. One of the best tools in this field is The OWASP Maryam. The interface of Maryam is is very similar to Recon-ng and Metasploit. If we are familiar with these tools then Maryam will be very easy to use.
Key Features of Maryam
- Metasploit like Interface.
- Identifying WebApps and WAF.
- Extracts Emails, Docs and Subdomains from search engines.
- Extracts Links, CSS and JS files, Emails, Keywords from Web Sources.
- Extracting DNS, TLD by brute-force.
- Crawl Web Pages and search our RegExp.
- More upgrading in developing…
Installing Maryam on Kali Linux
As we told that Maryam comes with Kali Linux repository, so we don’t need much effort to install it. We can install it simply using following command:
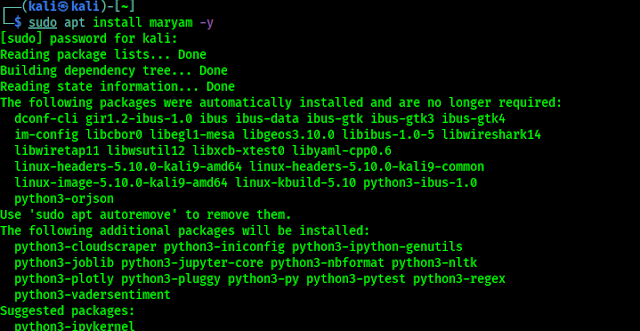
sudo apt install maryam -y
After putting our sudo password Maryam installing will be start on our system. As we can see in the following screenshot:
After the installation process is done, we can check the the tool is running by following command:
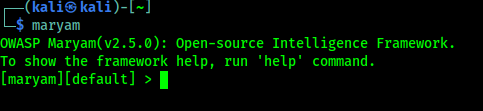
maryam
We can see the output of the above command in the following screenshot:
Here we need to run help command to see the the help options of Maryam Framework as we can see in the following screenshot:
It’s interface is seems very similar to Metasploit. Here we can run following command to see the modules:
show modules
Grabbing Social Media using Maryam
Let’s run this tool. For an example we are running social_nets OSINT module. Before running it we can check it’s help by just entering the module name or <module-name> –help, as we can see the help of social_nets in the following screenshot:
Let’s run this module by following command:
social_nets -q hax4us -e google,yahoo,bing
By using the above command we are trying to discover social media accounts of hax4us (my friend’s brand) on the search results of Google, Yahoo and Bing. We can use more supported search engines here (like Yandex etc).
Now multiple use of this function may be detected by search engines and they will detect the bot and it gives following CAPTCHA errors.
 |
| Google got the bot |
Finding Document Files
We can easily find Document files like PDF files, text files etc by using Maryam Open-Source Intelligence Framework, we are going use docs_search module for this, and the command will be like following:
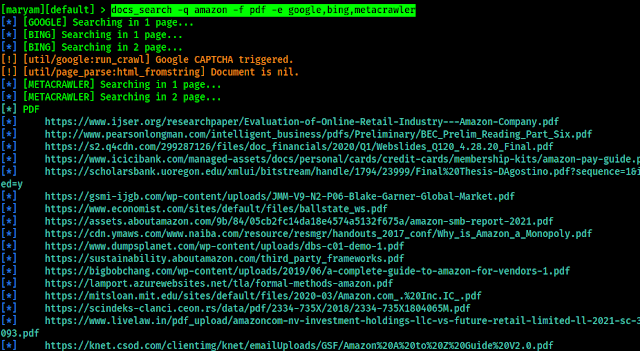
docs_search -q amazon -f pdf -e google,bing,metacrawler
For searching document we had used docs_search module in the above command, and -q flag to set our query, -f flag used to specify file format and -e to specify engines (search engines) to find these files.
And in the following screenshot we can see that we got links of PDF files related to Amazon.
DNS Brute Force using Maryam
Let’s have a look how can we Brute Force DNS records using Maryam’s dnsbrute module. To do so we are going to use following command:
dnsbrute -d target.com --thread 10 --wordlist /path/of/wordlist
Crawling Pages using Maryam
Now we are going to use the crawl_pages module to crawl an website (Regex search) for juicy information. To do so we are going to use following command:
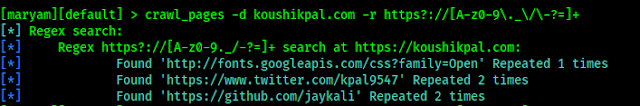
crawl_pages -d koushikpal.com -r https?://[A-z0-9./]+
In the following screenshot we can see the output. It scans the website for duplicate information.
Final Words
This is how we can install and use Maryam on our Kali Linux system, we learned basic things we can do with OWASP Maryam OSINT Framework. OWASP Maryam is a modular open-source framework based on OSINT and data gathering. It is designed to provide a robust environment to harvest data from open sources and search engines quickly and thoroughly.
It has a lots of advanced features like we can set proxy, agents and timeout. For more information we can check the official page.
Love our articles? Stay updated with our articles by following us on Twitter and GitHub. Be a part of the KaliLinuxIn community by joining our Telegram Group, where we focus on Linux and Cybersecurity. We’re always available to help in the comment section and read every comment, ensuring a prompt reply.