15 Powerful Gadgets For Ethical Hackers | Hardware Tools for Hackers in 2021
Our in this platform we usually talk about various applications and their uses to check loopholes on systems. But penetration testers not only uses software applications, they also need some hardware to perform the tasks. In this detailed article we are going to cover hardware devices & gadgets used by an ethical hacker. Let’s start with a warning.
Warning:- This article is written for educational purpose only. To make it more ethical, we just only talk about the hardware devices publicly available in Amazon. Using these devices on our own for educational purpose isn’t crime, but using these devices against others without proper permission is illegal. So use these devices responsibly, we and Amazon will not be responsible for talking and selling these kind of product.
Lets start with a computer, most of cybersecurity experts prefer laptops, not desktops because laptops are portable. We had wrote an entire article about best laptops for Kali Linux, Moving forward ethical hackers uses some other hardware devices that is our main topic for today.
1. Raspberry Pi 4
Raspberry Pi dominating the market of single board computers (SBC). This device used by almost every security personals.
This is very useful we can install entire Kali Linux on this credit card sized computer. Raspberry Pi also can be used in many other projects. Cybersecurity experts use it on various way. We can see in Mr. Robot Season 1 Episode 5, how Elliot hacked the climate control network to destroy magnetic tapes.
There are unlimited uses of raspberry pi for an ethical hacker. This device is a must have for everyone on infosec field.
2. Raspberry Pi Zero W
This is a small handheld computer, ideal for carrying the best penetration testing software tools, and to handle all the external hardware hacking tools. The most known Cybersecurity distro for it is P0wnP1 A.L.O.A. and Kali Linux. P4wnP1 is a highly customizable USB attack platform, based on a low cost Raspberry Pi Zero or Raspberry Pi Zero W. The successor of P4wnP1 is called P4wnP1 A.L.O.A. We recommend the USB type-A pongo-pin adapter shown in the above picture.
We also can use it a headless system (without monitor). This device connected with a power bank in our bag and we can control it from our mobile device on our hand(using VNC).
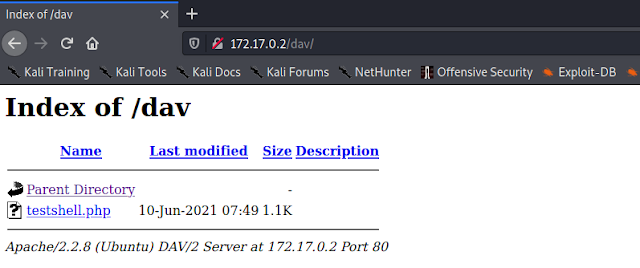
3. USB Rubber Ducky
USB Rubber ducky is created and developed by Hak5. Nearly every computing devices accepts human input from keyboards, hence the ubiquitous HID specification – or Human Interface Device. Keyboards announce themselves to computers as HID devices and are in turn automatically recognized and accepted.
The USB Rubber Ducky delivers powerful payloads in seconds by taking advantage of the target computers inherent trust all while deceiving humans by posing as an ordinary USB drive.
In simple words, if we plug it on a computer, the computer think it is a keyboard and it will inject (type, save and execute) our preset payload on the computer. There are lots of payload available for this device. Also we can easily write our own code.
This is one of the bast way to compromise a system having physical access.
4. WiFi Pineapple
The Wi-Fi pineapple is the original Wi-Fi attack tool developed by Hak5. There are three different models available from Hak5. They all are good, here we choose Mark VII model for it’s value for money.
This will automate the auditing of WiFi networks and saves the results. We can control it with awesome web based interface. This is really a very good product for security testing o wireless networks.
5. HackRF One
HackRF One from Great Scott Gadgets is a Software Defined Radio peripheral capable of transmission or reception of radio signals from 1 MHz to 6 GHz. Designed to enable test and development of modern and next generation radio technologies. We can read and manipulate radio frequencies using this device.
HackRF One is an open-source hardware platform that can be used as a USB peripheral or programmed for stand- alone operation. This SDR offers one important improvement compared to other cheap alternatives. But the Radio Frequency (RF) quality isn’t good as expected.
6. Ubertooth One
Ubertooth One is the most famous Bluetooth hacking tool we can find on the market. It is an open source 2.4 GHz wireless development platform suitable for Bluetooth hacking. Commercial Bluetooth monitoring equipment can easily be priced at over $10,000 , so the Ubertooth was designed to be an affordable alternative platform for monitoring and development of new BT, BLE and similar wireless technologies.
Ubertooth One is designed primarily as an advanced Bluetooth receiver, offering capabilities beyond that of traditional adapters, which allow for it to be used as a BT signal sniffing and monitoring platform. Although the device hardware will accommodate signal broadcasting, the firmware currently only supports receiving and minimal advertising channel transmission features.
7. WiFi Deauther Watch
As the name said it’s a deauther, it de-authenticate the WiFi users and they got disconnected. It’s not a jammer. It uses ESP8266 WiFi development board to do so. Here it’s watch version is looks super cool gadget for every hacker.
While a jammer just creates noise on a specific frequency range (i.e. 2.4 GHz), a deauthentication attack is only possible due to a vulnerability in the Wi-Fi (802.11) standard. The deauther does not interfere with any frequencies, it is just sending a few Wi-Fi packets that let certain devices disconnect. That enables us to specifically select every target. A jammer just blocks everything within a radius and is therefore highly illegal to use.
8. USB Killer
Computers doesn’t check the current flowing through USB, because it uses computers own power and can’t transmit more voltage. But what if we took an advantage of this to burn our (using on others is totally illegal) entire system.
When plugged into a device, the USB Killer rapidly charges its capacitors from the USB power lines. When the device is charged, -200VDC is discharged over the data lines of the host device. This charge/discharge cycle is repeated many times per second, until the USB Killer is removed. As the result target device becomes burned and unrepairable.
Its compact size and flash-drive style housing makes it an important device in every pen-tester’s toolkit. It can be used multiple times as we want.
9. Bad USB
This is a super alternative of USB Rubber Ducky. This device contains customized HW based on Atmega32u4 and ESP-12S. This device allows keystrokes to be sent via Wi-Fi to a target machine. The target recognizes the Ducky as both a standard HID keyboard and a serial port, allows interactive commands and scripts to be executed on the target remotely.
Attacker can easily carry it as a thumb drive and plug into any PC to inject payload, running own command on it, it also can be controlled over WiFi. It looks like innocent USB thumb drive, which is a great advantage. But this is doesn’t have faster speed like USB Rubber Ducky.
10. Hardware Keylogger
A hardware keylogger can be inserted between USB keyboard and computer. It captures all the keystrokes made from the keyboard, must have thing for every cybersecurity expert.
This is a basic hardware keylogger. It has 16 MB storage. Which is sufficient to capture keystrokes for a year generally. Later we can remove it and plug on our computer to read the keystrokes. Some keyloggers comes with WiFi controlling and SMS controlling functionality. No software can detect it’s there.
11. Adafruit Bluefruit LE Sniffer
Adafruit luefruit LE Friend is programmed with a special firmware image thatturns it into an easy to use Bluetooth Low Energy sniffer. We can passively capture data exchanges between two Bluetooth Low Energy (BLE) devices, pushing the data into Wireshark, the open source network analysis tool, where you can visualize things on a packet level, with useful descriptors to help us make sense of the values without having to crack open the 2000 page Bluetooth 4.0 Core Specification every time.
Note: We can only use this device to listen on Bluetooth Low Energy devices! It will not work on Bluetooth (classic) devices. Firmware V2 is an improved firmware from Nordic now has better Wireshark-streaming sniffer software that works with all OS for live-streamed BLE sniffing. The sniffer firmware cannot be used with the Nordic DFU bootloader firmware, which means that if we want to reprogram this device you must use a J-Link (and a SWD programmer board). We cannot over-the-air (OTA) reprogram it.
12. Micro-controllers
There are lots of micro-controllers used by ethical hackers. Some of them are must have in a ethical hackers backpack.
NodeMCU ESP8266
ESP8266 is a $6 WiFi development board and it can be used in various way, we can make WiFi deauther by our own. It also can be used to create phishing pages over WiFi.
Arduino Pro Micro
This tiny micro-controller is one of the best choice for ethical hackers. We can make our own DIY USB Rubber Ducky.
Arduino Pro Micro is really good thing at a very low price. But if we want to change the script then we need to reset and upload new script on it from our computer.
13. RTL-SDR
RTL-SDR is a very cheap software defined radio that uses a DVB-T TV tuner dongle based on the RTL2832U chip-set.
It can be used to intercept radio frequencies. We can use it for listening others conversations. It is also able to intercept GSM mobile calls and SMS. It is very useful for cybersecurity experts.
14. Proxmark3 NFC RFID Card Reader
Owning a Promark3 means owing the most powerful and most complete device RFID/NFC (LF & HF) testing in the frequencies of 125KHz / 134KHz / 13.56MHz.
This devices can make read the data of RFID and NFC cards and then make a copy of it. We can write the new copies on blank cards provided with this package. We we need more we can buy more blank cards on Amazon.
Therefore, investing some more bucks in upgrading it, it’s not a bad idea. To improve its range we need the extended range antennas for LF and HF.
Another new and nice upgrade for it, is the Blue Shark Bluetooth 2.0 upgrade, that permits controlling the proxmark3 wirelessly plus adding an external battery to create an autonomous proxmark3 that can be connected and controlled from your computer or smartphone. The Walrus NFC application has been updated to permit control by Bluetooth. It also fixes the high temperature concerns adding a metal cooler.
WiFi Adapters (Monitor Mode & Packet Injection)
WiFi adapter specially which supports monitor mode and packet injection is essential for WiFi penetration testing. So most of the hackers uses it. We had noticed that Alfa makes awesome adapters for cyber-security personals. We already discussed it on our Best WiFi adapter for Kali Linux article. Please check out that article before buying an WiFi adapter.
Something Extra
This is the gadgets for hackers we can directly buy from Amazon and help us on our ethical hacking journey. There are some more gadgets used by hackers but talking about them will be not ethical here. Most of them manufactured from china and available on some online stores. There are some cool stores like Hak5, but in this article we discussed about some gadgets which are openly available on Amazon.
Warning:- Using the above devices is not illegal. They are selling publicly on Amazon. But using these devices to harm anyone is totally illegal. We listed them for educational purpose and to safe ourselves from these kind of devices. If anyone uses this devices to harm anyone then we are not responsible for that, Amazon also not responsible. So use this devices responsibly, always remember:
That’s for today. Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.





















![Best USB WiFi Adapter For Kali Linux 2021 [Updated July] Best USB WiFi Adapter For Kali Linux 2021 [Updated July]](https://infocerts.com/wp-content/uploads/2021/07/Best-USB-WiFi-Adapter-For-Kali-Linux-2021-Updated-July-infocerts.jpg)