Introducing ATT&CK v10: More Objects, Parity and Features
Introducing ATT&CK v10: More Objects, Parity, and Features
By Amy L. Robertson (MITRE), Alexia Crumpton (MITRE), and Chris Ante (MITRE)
As announced a couple of weeks ago, we’re back with the latest release and we’re thrilled to reveal all the updates and features waiting for you in ATT&CK v10. The v10 release includes the next episode in our data sources saga, as well as new content and our usual enhancements to (sub-)Techniques, Groups, and Software across Enterprise, Mobile and ICS, which you can find more details about on our release notes.
Making Sense of the New Data Sources: Episode II
In ATT&CK v9, we launched the new form of data sources which featured an updated structure for the data source names (Data Source: Data Component), reflecting
“What is the subject/topic of the collected data (file, process, network traffic, etc.)?” :
“What specific values/properties are needed in order to detect adversary behaviors?”
These updates were linked to Yaml files in GitHub, but weren’t fully integrated into the rest of ATT&CK yet. Our updated content in ATT&CK v10 aggregates this information about data sources, while structuring them as the new ATT&CK data source objects (somewhat similar to how Mitigations are reflected).
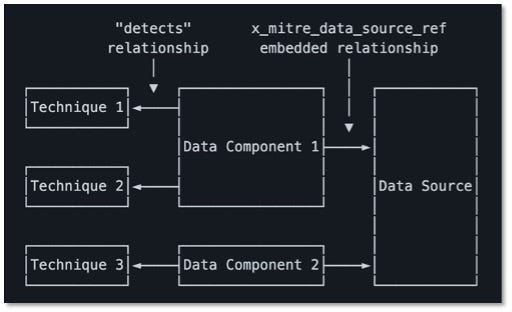
The data source object features the name of the data source as well as key details and metadata, including an ID, a definition, where it can be collected (collection layer), what platform(s) it can be found on, and the data components highlighting relevant values/properties that comprise the data source. Featured below is an example of a data source page in ATT&CK v10.
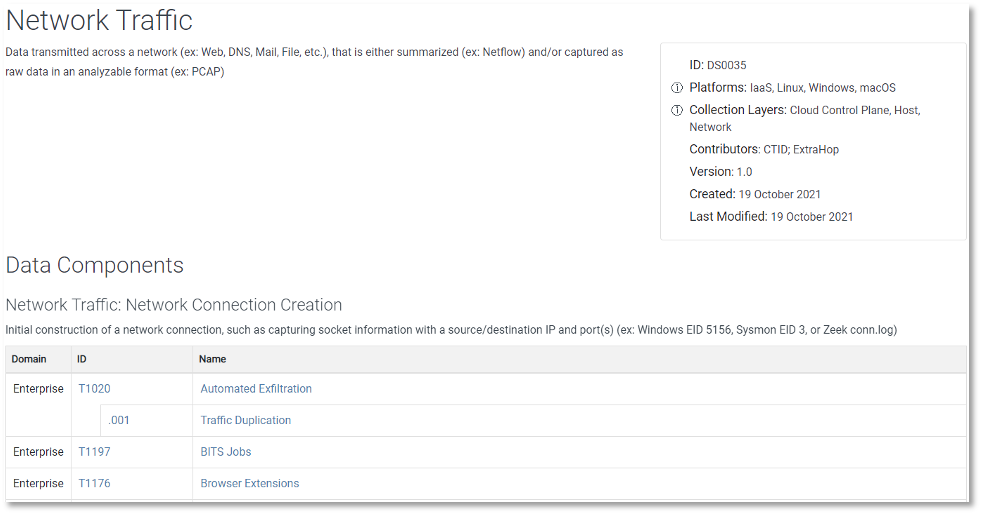
Data Components are also listed below, each highlighting mappings to the various (sub-)techniques that may be detected with that particular data. On individual (sub-)techniques, data sources and components have been relocated from the metadata box at the top of the page to be collocated with Detection content.
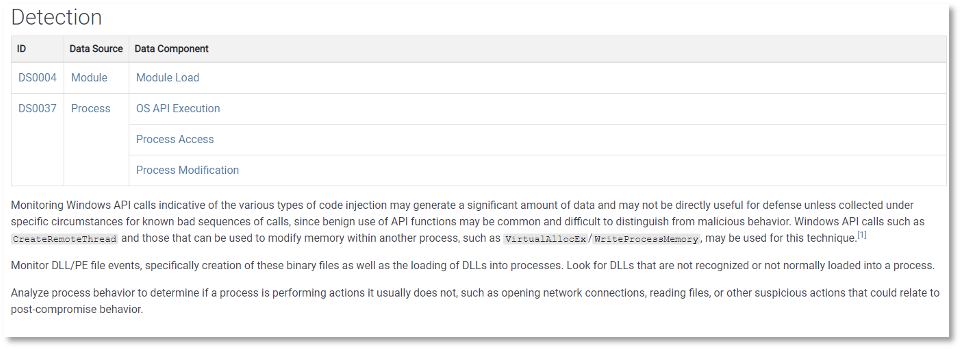
These data sources are available for all platforms of Enterprise ATT&CK, including our newest additions that cover OSINT-related data sources mapped to PRE platform techniques.
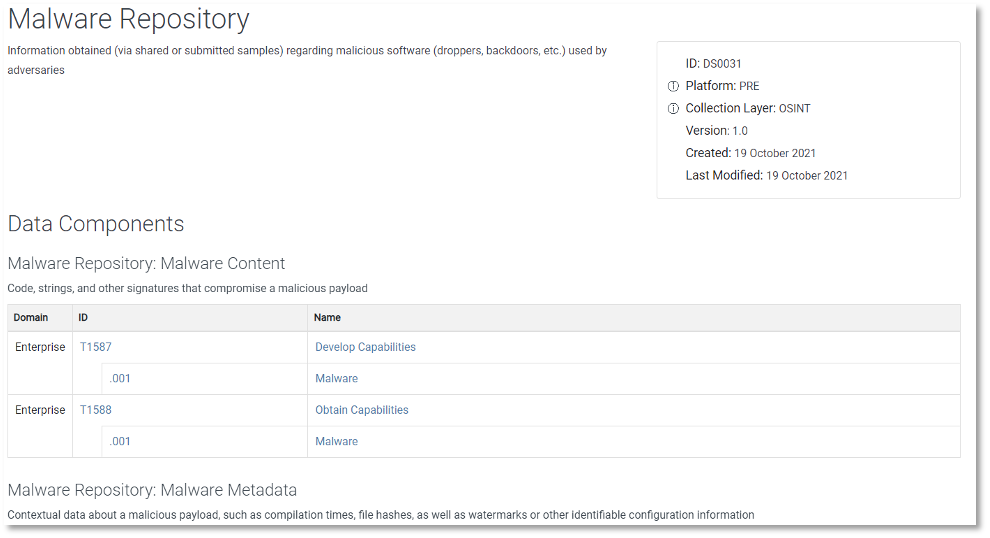
These updated structures are also visible in ATT&CK’s STIX representation, with both the data sources and the data components captured as custom STIX objects. You’ll be able to see the relationships between those objects, with the data sources featuring one or more data components, each of which detects one or more techniques. For more information about ATT&CK’s STIX representation, including these new objects and relationships, you can check out our STIX usage document.

We hope that these enhancements further increase our ability to translate our understanding of the adversary behaviors captured within ATT&CK to the data we collect as defenders. We are very excited to see these data source objects grow and evolve, and like the rest of ATT&CK, invite the community to submit contributions and feedback!
Note: We will no longer be working with Enterprise data sources in GitHub after ATT&CK v10. Moving forward we will accept all related contributions through our normal contribution process.
MacOS and Linux: Now with New Content!
Over the past several months, we’ve been continuing to improve and expand coverage across the macOS and Linux platforms. We understand adversaries actively target these platforms, however there is significantly less public reporting for adversarial hands-on-keyboard procedures and malware analysis. We’re pleased to report that we’ve been collaborating with macOS security and vulnerability research contributors across the globe to address these challenges. In upcoming releases, we’re hoping to leverage this same community engagement for Linux. We’re excited to see the growth in content from the community’s contribution, and the improvements ranging from how we capture new techniques to conveying the impact of existing techniques was a collaborative effort.
One of the most notable changes we made for techniques across the board was providing more in-depth references and use-cases on how procedures and processes work, and the impact they have. Remote services along with additional techniques for macOS and Linux received some attention, but most improvements were more detailed examples in the description section with supporting detection ideas. Along with the rest of Enterprise, we also updated our macOS data sources to enhance defender visibility.
ICS : Object-Oriented and Integrating
ICS has been focusing on feature equity with Enterprise, including updating data sources, adding and refining techniques, revamping assets, and charting out our detections plan. We’re also making some key changes to facilitate hunting in ICS environments. As we noted in the 2021 Roadmap, v10 also includes cross-domain mappings of Enterprise techniques to software that were previously only represented in the ICS Matrix, including Stuxnet, Industroyer, and several others. The fact that adversaries don’t respect theoretical boundaries is something we’ve consistently emphasized, and we think it’s crucial to feature Enterprise-centric mappings for more comprehensive coverage of all the behaviors exhibited by the software. With Stuxnet and Industroyer specifically, both malware operated within OT/ICS networks, but the two incidents displayed techniques that are also well researched and represented within the Enterprise matrix. Based on this, we created Enterprise entries for the ICS-focused software to provide network defenders with a view of software behavior spanning both matrices. We also expect the cross-domain mappings to enable you to leverage the knowledge bases together more effectively.
For data sources, we’re aligning with Enterprise ATT&CK in updating data source names. ICS’s current release reflects Enterprise’s v9 data sources update, with the new name format and content featured in GitHub. These data sources will be linked to YAML files that provide more detail, including what the data sources are and how they should be used. For future releases we plan on mapping the more granular assets to techniques to enable you to track how these behaviors can affect a technique, or what assets these behaviors are associated with. On the detections front, we’re working behind the scenes to add detections to each technique, and this will be reflected in future releases (we expect detections to really help out in hunt and continuous monitoring). Also in 2022, we’re preparing to integrate onto the same development platform as Enterprise, the ATT&CK Workbench, and join the rest of the domains on the ATT&CK website (attack.mitre.org).
Expanding Our Mobile Features
In the Mobile space, we’ve been focused on catching up on the contributions from the community, updating (sub-)techniques, Groups, and Software, and enhancing general parity with Enterprise. We’ve also been working hard behind the scenes to implement sub-techniques as mentioned in our 2021 Roadmap. We’re excited to introduce this new Mobile structure in April 2022, to better align with other platforms on Enterprise. Our plan is to do a beta release for the sub-techniques prior to the release of v11 to provide you with an opportunity to test out those updates and provide feedback.
About Cloud
Along with the rest of Enterprise, we’ve been updating content across Cloud, collaborating with community members on activity in the Cloud domain, and keeping an eye out for new platforms to add to the space. We also continued working on data sources, although as we outlined for the v9 release, our Cloud data sources are a little different than the host-based data sources, specifically aligning more with the events and APIs involved in detections instead of just focusing on the log sources.
What’s Next in 2022?
We hope you’re as excited as we are about v10, and we’d love your feedback and for you to join us in shaping our v11 release. We already have a lot on the horizon for 2022, included structured detections, campaigns, tools to enable overlays and combinations, and ATT&CKcon. If you have feedback, comments, contributions, or just want to ask questions, connect with us on email, Twitter, or Slack.
©2021 The MITRE Corporation. ALL RIGHTS RESERVED. Approved for public release. Distribution unlimited 21–00706–18.
Introducing ATT&CK v10: More Objects, Parity and Features was originally published in MITRE ATT&CK® on Medium, where people are continuing the conversation by highlighting and responding to this story.