Module 4: Enumeration Techniques and Commands with Examples
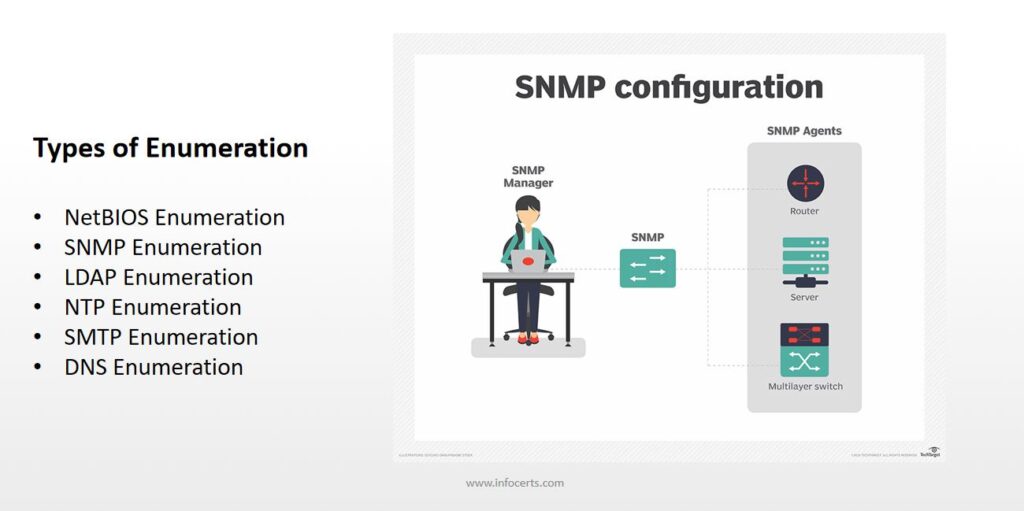
Description: This guide provides an overview of common enumeration techniques used in penetration testing and network assessment. Each technique is accompanied by a Kali Linux command and an example to demonstrate its usage. Please exercise ethical responsibility and proper authorization while utilizing these techniques. Enumeration Type Kali Linux Command Example Summary NetBIOS Enumeration nbtscan <target> …
Module 4: Enumeration Techniques and Commands with Examples Read More »