Description: This guide provides an overview of common enumeration techniques used in penetration testing and network assessment. Each technique is accompanied by a Kali Linux command and an example to demonstrate its usage. Please exercise ethical responsibility and proper authorization while utilizing these techniques.
| Enumeration Type | Kali Linux Command | Example | Summary |
|---|---|---|---|
| NetBIOS Enumeration | nbtscan <target> | nbtscan 192.168.1.1 | Enumerates NetBIOS names and shares on a target system. |
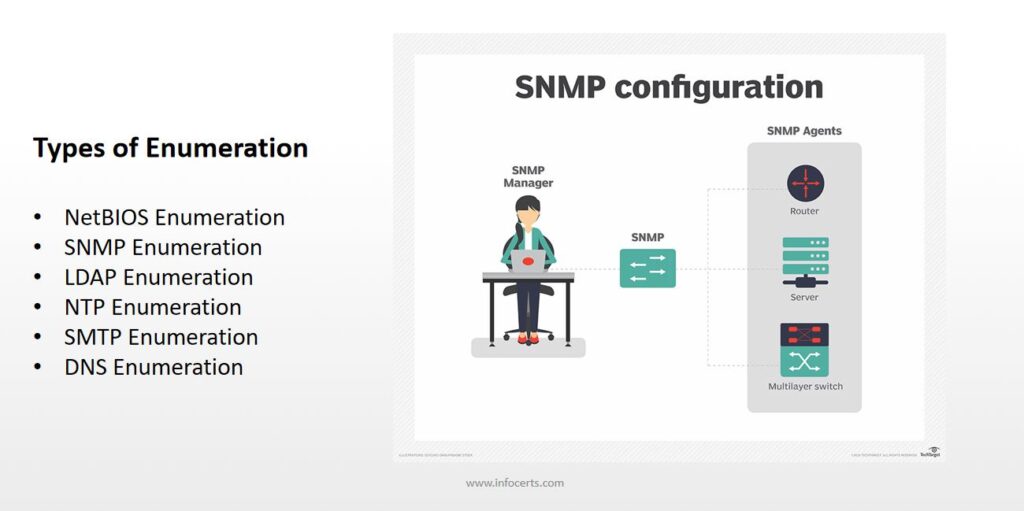
| SNMP Enumeration | snmpwalk -c public -v1 <target> | snmpwalk -c public -v1 192.168.2.1 | Retrieves SNMP information from a target device using the community string “public.” |
| LDAP Enumeration | ldapsearch -x -h <target> -b <base_dn> | ldapsearch -x -h 192.168.3.1 -b "dc=example,dc=com" | Searches the LDAP directory on a target system for specified base DN (Distinguished Name). |
| NTP Enumeration | ntpdate -q <target> | ntpdate -q 192.168.4.1 | Queries an NTP server for time information and clock offset. |
| SMTP Enumeration | smtp-user-enum -M VRFY -U <user_list> -t <target> | smtp-user-enum -M VRFY -U users.txt -t 192.168.5.1 | Enumerates valid email addresses on an SMTP server using the VRFY command. |
| DNS Enumeration | dnsrecon -d <domain> | dnsrecon -d example.com | Performs DNS enumeration, including subdomain discovery, zone transfers, and DNSSEC checks. |
Please keep in mind that these tools and commands should be used responsibly and only in environments where you have proper authorization.