Right way to record and share our Terminal sessions
The Terminal, also known as the command line or a Terminal emulator, is an crusial component of any useful operating system. It is by far one of the most important applications on MacOS and Linux. The Terminal provides an efficient interface to access the true power of a computer better than any graphical user interface.
Sometimes we need to share our terminal or terminal commands to others to show or solve some issue. In that case we use screenshots which are not so satisfying. If we use a screen recorder apps but recording a screen and send the video file is annoying, here steps in asciinema.
Asciinema is a free and open source solution for recording terminal sessions and sharing them on the web in a easy way. Now this seems very interesting, lets try asciinema on our Kali Linux system. It also can be installed on various systems like MacOS, Linux, BSD even from source and pip.
To install it on our Kali Linux system we can run following command:
After giving sudo password the installation process will start. In the following screenshot we can see that asciinema is installing.
This is very little tool should be installed on some seconds. After the installation process is complete we can run this tool and start record our terminal.
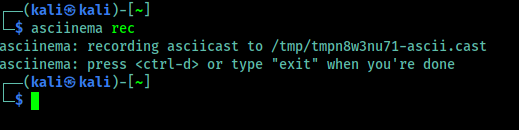
To start the recording we need to use the following command on our terminal.
In the following screenshot we can see that it is started and we can see in the following screenshot:
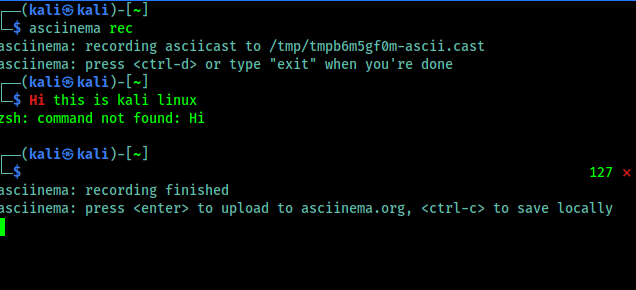
Now we can type any command and it will be recorded. Now we need to remember one thing that it records only the terminal, not other apps or the whole screen. When we feel that our recording is complete we can press CTRL+D or run exit command, shown in the following screenshot:
Here it is clearly written that if we want to upload it on asciinema.org then we need to just press Enter⤶ and to save it on just our system we need to use CTRL+C.
We press Enter⤶ to upload it on asciinema.org and in the following screenshot we got the link of the recording.
Now we can open this on our browser, here we might need an asciinema.org account. If it requires then we can easily create it by using mail id. Asciinema doesn’t requires any password they verify the mail address (?We can use temp-mail for a temporary mail id?), and we are ready to rock. We can see various options there as shown in the following screenshot.
We can share it in various way. We can directly send someone the link. Asciinema also supports oEmbed/Open Graph/Twitter Card protocols, displaying a nice thumbnail where possible. We can also easily embedded an asciicast on any HTML page. If we want to put a recording in a blog post, project’s documentation or in a conference talk slides. As we embedded a asciinema terminal record, please check below:
We also can play our locally saved asciinema records (with *.cast file extension), by using following command:
This is about record and share our terminal in a very easy way. Forget screen recording apps and blurry video. Enjoy a lightweight, purely text-based approach to terminal recording on our Kali Linus system.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.