Hope you are all doing awesome. As always, today we’re agin going to learn something from the basics of cybersecurity world, where a seemingly harmless string of characters can become our nightmare. Yes, you guessed it—we’re talking about default passwords. Not only that We also learn how we can use a tool called Passhunt on our Kali Linux system and find loopholes on various devices.
Why Default Passwords Are So Dangerous?
Now, imagine we’re working on our own home or office. We’ve got all these trusty devices—like routers, webcams, printers—keeping our connection the world and running our work smoothly. But here’s the catch: many of these devices come with default usernames and passwords straight out of the box.
At first glance, default passwords might seem like a easy shortcut. After all, who wants to spend time to set up a new password when we can just use the one that’s already there, right? Wrong! Default passwords are like leaving the front door of our system wide open for bad characters. Devices with default credentials aren’t just in danger—they are the danger. Anybody can enter the system without knocking the door.
Let we have a look how default passwords can lead to some serious cyber attacks on us.
- Network Nets: Imagine that—we’ve got our brand new router up and running, blissfully unaware that it’s still using the default password. Along comes a crafty bad attacker who sniffs out our router’s vulnerability faster than we can type “password123.” With access to our router, the attacker can wreak havoc on our entire network—slowing down our internet, eavesdropping on our data, or even launching full-blown cyber attacks. It’s like handing over the keys to our system on a silver platter!
- Web Woes: Next up, we’ve got webcams. These little things might seem innocent enough, but with default passwords, they’re serious trouble makers. Imagine a attacker gaining access to our webcam without we even knowing it. They could spy on our every move, invade our privacy, or even use the footage for blackmail. It’s like having an unwanted guest lurking in the shadows of our home, and nobody wants that!
- Printer Predicaments: Last but not least, let’s talk about printers. Yes, even these humble machines aren’t safe from the perils of default passwords. With access to our printer, a attacker could intercept sensitive documents, manipulate print jobs, or even launch a good old-fashioned printer hack (yes, that’s a thing!), gaining unauthorized access to sensitive documents stored on the printer’s memory. It’s like turning your trusty printer into a cyber tool, ready to strike at a moment’s notice.
So, what’s the moral of the story? It’s simple: always, always, always change default passwords. Whether it’s for our router, our webcam, our printer, or any other device in our supervision, we shouldn’t take shortcuts when it comes to security. Humans are the most weakest point in any security system. Humans are normally stupid, not really, a better word would ignorant, they don’t aware how stuff works. We just want that our router runs perfectly for Netflix and chill.
Hunting down default passwords using Passhunt
Enough talking about layman’s who ever reading this considers as a cyber security expert and we cyber security experts didn’t came here to learn those above things. We wanna test these kind of vulnerabilities due to human errors. Passhunt is a Python script which is going to help us on this matter.
This Passhunt tool originally created by Viral Maniar which can search through 523 vendors and their 2084 default passwords. It works like a database. Passhunt was giving some issues on newer Python and Kali Linux version. We have updated this script and removed some unwanted lines to run it on our Kali Linux system.
Let’s fire up our Kali Linux Terminal and type following command to clone Passhunt from Github:
git clone https://github.com/jaykali/Passhunt
After pressing Enter ↲ button on our keyboard Passhunt will be downloaded on our system as we can see in the following screenshot.
Now we are going to use cd command to go to the Passhunt directory. The command will be following:
cd Passhunt
Now we need to install required dependencies to run Passhunt and the command will be following:
pip3 install -r requirements.txt
It may take some seconds depending on our internet speed and system configuration. In the following screenshot we can see the output of above commands.
Now we are going to run Passhunt by using following command:
python passhunt.py
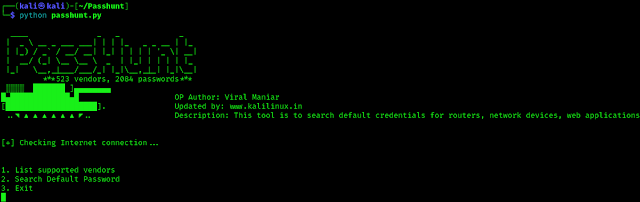
Now our password hunter Passhunt is ready and running as we can see in the following screenshot.
In the above screenshot we can see that there are 3 options only on the main menu.
- List supported vendors: By pressing 1 and Enter we can see all the supported vendors (brands) names list.
- Search Default Password: We can Hit 2 and Enter to search for a Vendor’s default credentials.
- Exit: To quit this tool we just need to type 3 and hit Enter.
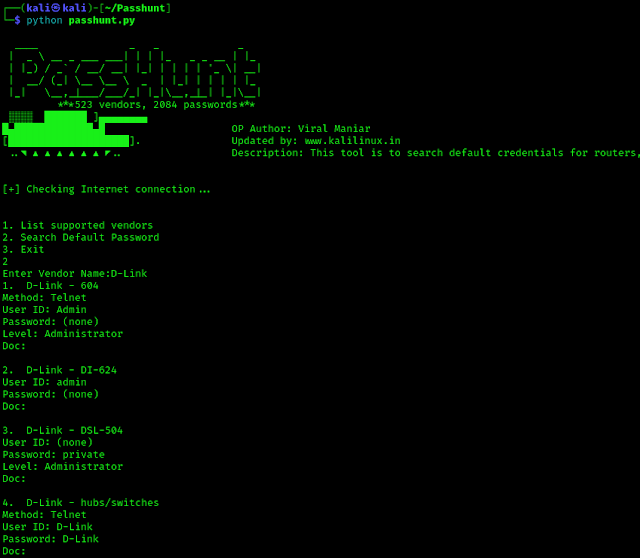
Now assume we have encountered with a D-Link device, and we are thinking to try default passwords login on this then we can search for it on Passhunt by pressing 2 and hit Enter ⤶.
Then it will prompt for vendor’s name we can use D-Link in our case. After that we are able to see the list of D-Link devices and their default credentials. Here we can choose our target device as we can see in the following screenshot:
This is how we can search for default password database using Passhunt on our Kali Linux system. Nowadays default password devices are rare every device have it’s own default password written on somewhere in the packets. But there are some web services which are old and not updated for a while even offices, universities, households use very old model routers for saving some bucks. Humans are
Humans are ignorant they really don’t care about these online security. They uses same passwords on internet banking, social media even in shopping sites also. They don’t change the default passwords of devices. Those things are really scary.
One more thing, If our target device is a router and it have a WPS button (ultra modern routers usually don’t have WPS button, others may have) then we can also try Pixie Dust Attack to crack it.
That is it for today. We already knows that default passwords are very risky and learn something new i.e using Passhunt on our Kali Linux system and search for default passwords and credentials.
Love our article? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group & Whatsapp Channel We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.