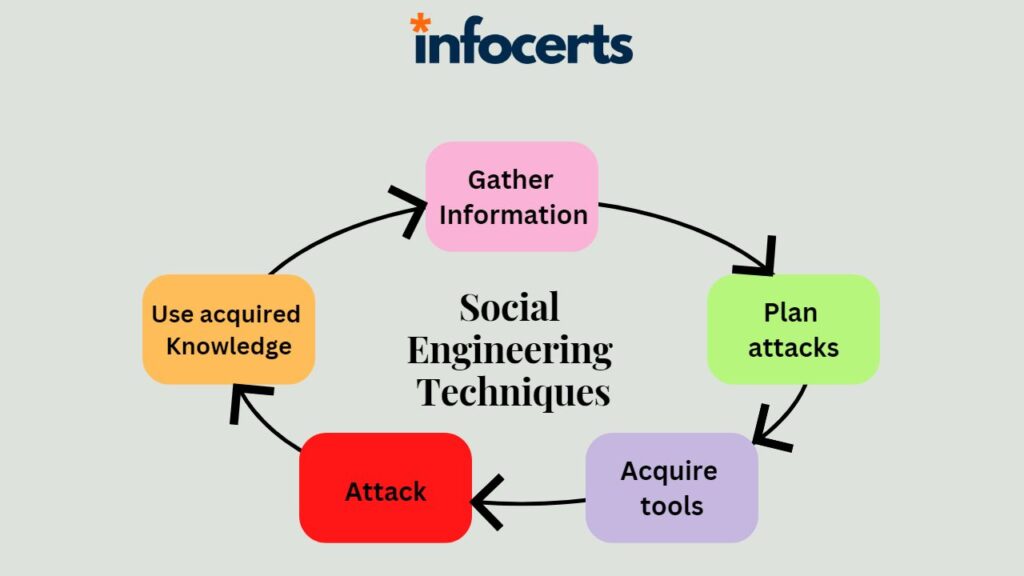
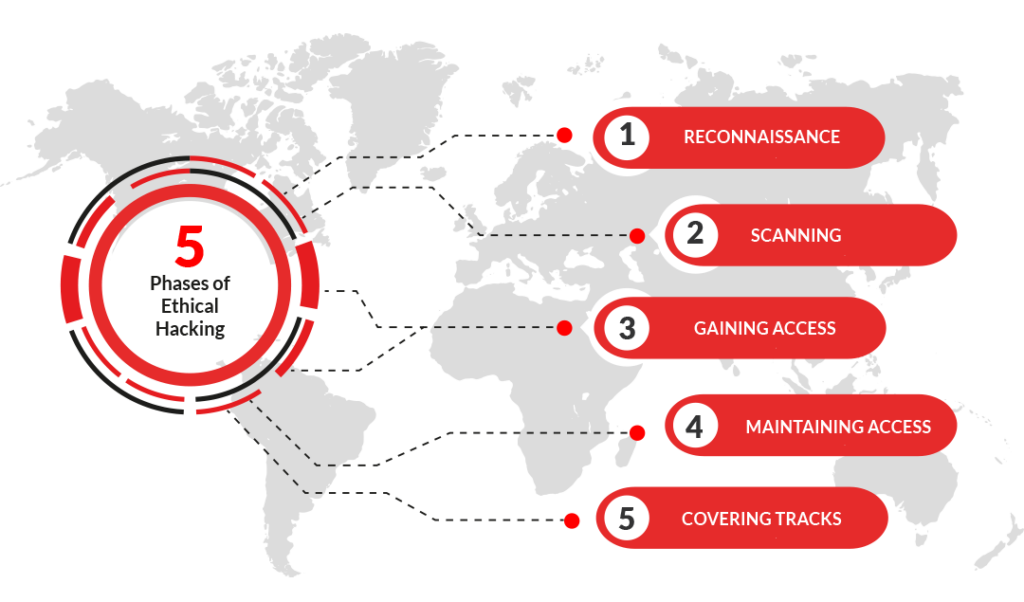
The Art of Cyber Resilience: Strategies for Effective Protection
Date: October 17, 2023 Time: 3:30 PM CAT | 9:30 AM EDT | 7:00 PM IST Topic: The Art of Cyber Resilience: Strategies for Effective Protection Register Abstract: Modern-day cybersecurity primarily revolves around cyber resilience, i.e., an organization’s ability to prepare for, respond to, and recover from cyber attacks. Organizations are said to be resilient…
The post The Art of Cyber Resilience: Strategies for Effective Protection appeared first on Cybersecurity Exchange.