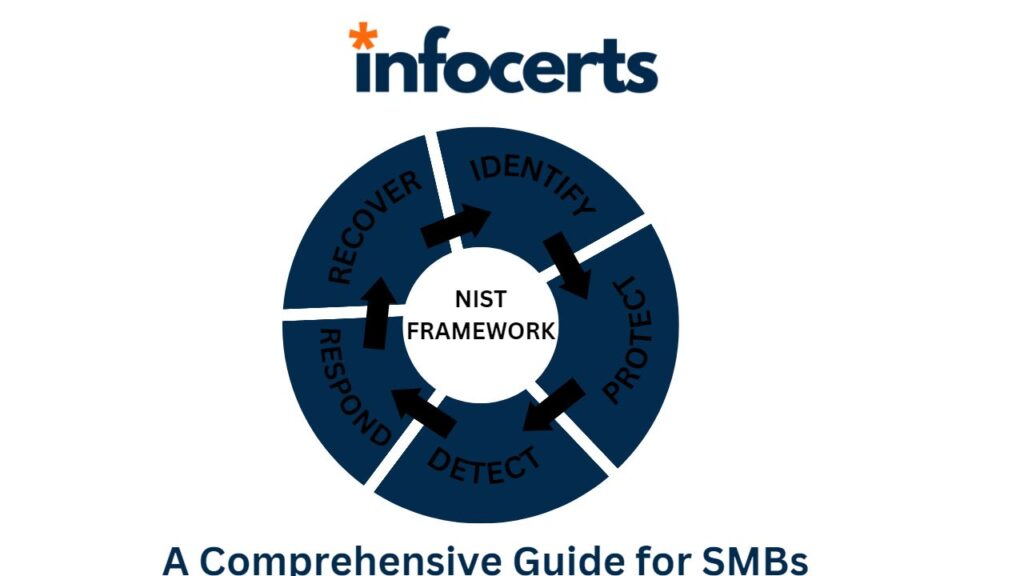
Collaborative Security: Incorporating the NIST Cybersecurity Framework into Third-Party Vendor Management
Introduction: In today’s interconnected business landscape, organizations rely on numerous third-party vendors to support their operations and deliver essential services. While these partnerships offer numerous advantages, they also introduce potential cybersecurity risks. A breach in a vendor’s security can have a detrimental impact on the organization, its customers, and its reputation. To mitigate these risks …