So, we have searched for
Facebook account hacking. Almost all new comer in hacking field wants to
hack Facebook or Instagram account or Instagram or others Wi-Fi password, this is the main priority of every noobies. After ending this tutorial we will have a clear idea on Facebook hacking in depth. Not only just about Facebook, this tutorial applies on social media accounts like
Instagram, Facebook, Twitter, Snapchat etc.
First off all we have to clear the truth that we simply can’t hack Facebook or Instagram. But when we search on Google there have a lots of free tools that giving us password of any Facebook user by just typing user’s email address. If you tried this kind of tools, then you are not on the general level of stupidity. Congratulations, you have achieved a higher level of stupidity. Come on, if this was so easy then Facebook needs to shut down their business.
When some sites or tool says it can hack Facebook passwords by just typing username or e-mail id you should understand that it is fake. They all have some common things which are following :
- All have very user-friendly interface. We just need to type user-id and click on hack.
- Then it will show that the password is successfully cracked, but they will not revel the password.
- All have links which will lead you to a survey or some annoying ads even may be say to download malicious software.
- All are 100% not working.
Then what does actually meaning of Facebook hacking. Many of us are mislead by the term of hacking. They think hacking means steal someone’s password and gaining unauthorized access but hacking is so much more.
When we try to learn hacking Facebook we need to understand some things how Facebook works means understand the functioning of the website, find about Facebook’s database management systems, scripts used, use of cookies, language use to build the website.
Then need to find out vulnerabilities in the the website in our case that is Facebook or Instagram.
Then need to code exploits to break through the obstacles and gain privileges into Facebook’s system, using suitable payloads. Then we need to check their database and the passwords will be encrypted in Facebook’s own way, we need to decrypt the passwords, then the last step is to set a backdoor for easy access next time, and we must need to clear our traces so that we don’t get caught.
Believe us, not everyone can do this, means we read some blogs and learned much things on hacking and Kali Linux, that is not enough for Facebook Hacking. So, the conclusion is that hacking Facebook is a real big deal, not everyone’s cup of tea. Even elite level hackers can’t do it. Nothing is impossible but hacking Facebook in above way is practically very close to impossible.

But wait, here we are talking like this, but that kid next door claims he can get Facebook password of anyone, and he is good, but not “code a exploit for Facebook” good, no not that kind good. This is where the social engineering steps in.
With time the level of security in technology fields are getting stronger. The encryption has reached to the unbeatable stage with 256 bit encryption, cracking a password will take practically forever (thousands of years). But it is very easy to make fool a human brain.
Humans are the weakest point in any security system.
Humans are normally stupid, not really, a better word would ignorant, they don’t aware how stuff works. Most of users have no idea on what Facebook or Instagram is doing for their account’s security, and they easily ruin each and everything of Facebook’s/Instagram’s effort to protect their privacy by their carelessness.
So, how our Facebook or Instagram accounts can be hacked and how we can be safe ?
Here is some Facebook and Instagram hacking method and techniques to be safe.
1. Phishing
Phishing is the most common method to terminate someone’s Facebook account. The most popular type of phishing is creating a fake login page, and send the link of page by e-mail or SMS or social media. The login page will look exactly like the Facebook login page.
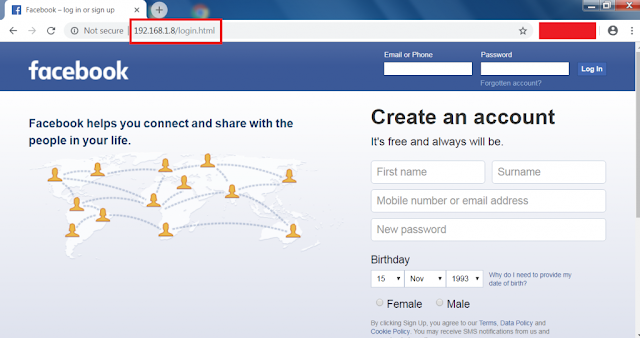 |
| Check the URL please. It’s not real Facebook |
If the victim logs in, the credentials (id and password) will be sent to attacker not in real Facebook. This process is a bit difficult because we need to host a website and create a login page. But some tools really made it kids play. We have some tutorials which makes phishing very easy. Tools like Modlishka can even bypass two factor authentication on a phishing attack. Check following :
How to be safe from Phishing?
- We should not click on any link through email/website/chatroom or text messages etc.
- we need to check the link is driving to original Facebook, mean to say check the links is https://www.facebook.com/ or not. If not and the page is looking like Facebook like the above picture, then this is a phishing page.
- Sometimes phishing links hided with normal looking genuine links. To know more read our hide phishing URL article.
- Windows user should use anti-virus and web-security software , like norton or McAfee . Linux user should take care before clicking unknown links.
2. Keylogger
Keyloggers works can be simply understand by it’s name. Yes it logs all the key strokes on the keyboard that user makes, without their knowledge. When user types their username and password keyloggers capture it.
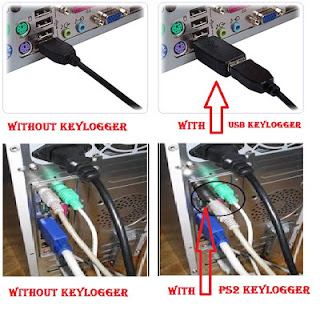 |
| Hardware Keylogger |
Keylogger are generally two types “software keylogger” and “hardware keylogger”.
- Software Keylogger:- Software keylogger is a program has to be download (or send by any way) and install on the the victim’s computer or mobile phone. It will automatically start capturing the keystrokes of keyboard. After device turned on this program starts it’s work, and runs in background to be undetected. Software keyloggers sends the details of key strokes to the attacker by email.
- Hardware Keylogger:- The work is same as software keylogger but method is different. Hardware keylogger is a USB/ps2 tool that connects between USB keyboard and the computer. The USB port of keyboard is plugged with this hardware and then it connects to the computer. It capture and saves the keystrokes in it’s inbuilt memory, and attacker need physical access to victim’s computer. Some premium hardware keyloggers have Wi-Fi enabled which can email captured keystrokes or can be accessed remotely over Wi-Fi.
How to be safe from Keyloggers ?
- Use a firewall. Software keyloggers usually send information through the internet, so a firewall will monitor our computer’s online activity and find out if anything suspicious.
- Installing anti-virus or anti-malware is good for windows users to detect software keyloggers.
- Shouldn’t use or download third party programs or apps. It may be embed with malicious apps like keylogger or any other payload.
- Now this is very easy to be safe from hardware keylogger. We need to be aware for it, that someone could not plant a USB hardware on our computer.
3. Reset The Password/Recover Account
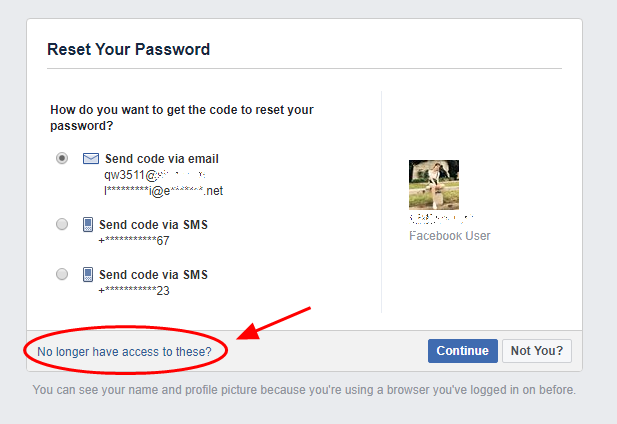
Resetting the password is the easiest method to hack someone’s Facebook account. This will be very easy if the attacker is victim’s friend or personally know the victim. Attackers need to know victim’s email id, then they click on “Forgot Password” and type victim’s email. When the account comes up they click on “This is my account“.
Then if it asks to reset the password by the email. This will not work for the attacker. The attacker need to choose “No longer have access to these ?“
Then depending on Facebook’s recent policy attacker might need to choose the pictures of friends uploaded or answer the security question or type email that isn’t linked any Facebook account.
In this method of Facebook hacking if attacker is a close friend of victim then it will be grate for him. Attacker just need to make an educated guess.
How to be safe from recover account?
- we should use an fresh email address specially for Facebook account and we never show that email id on Facebook profile. We never publish that email id.
- When we choose the security question and answer we need to make it difficult that no one can figure it out by know us personally or checking our Facebook posts. No pet names neither anniversaries, not even the names of best teacher. These questions are very easy for guessing and known personalities.
4. Hacking the Email
If the attacker terminate our email address then he can easily access our Facebook account by just resetting our Facebook password.
But how attacker can get into our email address ? By phishing or any other social engineering attacker can get the password of our mail address.
How to be safe from E-mail hacking ?
- We need a special care at mail id like Facebook accounts.
- Using a special email for Facebook would be batter. We shouldn’t tell anyone our that email id.
5. Easy Passwords
Peoples are getting smarter, now these days very few people choose 12345678 or 00000000 as password. But for easily remember they choose easy passwords, like birthday, old or current mobile numbers, nicknames. These type of passwords are very easily hacked.
How to be safe from easy passwords?
- First we should choose an uncommon password. A perfect password will be 13 characters long or more, it must contains some upper case and lower case letters and some numbers and one or more special character like @, *, #, ? etc. Here is a beautiful guidance on choosing secure passwords Click Here.
- We should not write down our password or any personal information anywhere, some hackers check dustbins for personal information.
6. Man in the Middle
If attacker get close to his target, he can use
man in the middle attack (MITM) by creating a free fake Wi-Fi network, When target connects with his network attacker can steal credentials. Tools like
Wi-Fi Pumpkin makes easy to creating rouge Wi-Fi access point.
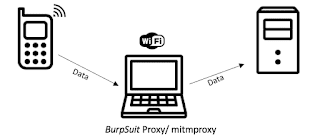 |
| Man-In-The-Middle Image Copyright researchgate.net |
Once victim connects to that Wi-Fi attacker can inspect the data packets sends and receives between Facebook and the user. Because all data is trafficking through attackers Wi-Fi. Tools like
Wireshark and
Ettercap may helps a lot.
How to be safe from MITM ?
- Don’t connect to any open and unsecured Wi-Fi networks.
- Don’t connect to any network that are out of place. May be we can see “Google Starbucks” when there is no Starbucks near. Attacker knows that our devices will connects automatically to our used same named networks.
- If we got trouble connecting ton our own Wi-Fi, then we need to look at our Wi-Fi list of nearby, If there are any copy of our Wi-Fi network, it might be the attacker using Evil-Twin or any other same types of attacks.
- If our router asks to enter password for firmware upgrade then it might be someone trying to get our credentials. How attackers are able to do it ? Read our this tutorial.
7. Looking for Passwords
Our Facebook can be hacked if someone who is peeping from behind, watching us type our passwords.
Another way of looking password is checking the victim’s personal computer physically. A common man always saves the username and the password in the browser in his personal computer for easy access next time, but the password can be seen very easily if attacker have access to victim’s personal computer. Attacker will check the advanced settings and privacy section of the browser.
How to be safe from this?
- Be careful while typing passwords, is anyone looking at our keyboard or is there any camera behind ?
- If we are saving our credentials in browser then we need to make our personal computer personal, for better result we recommend to not save password in browser because they also can be stolen remotely by using malicious web apps.
- Stay away from typing our password on public place or logging our social media account on public device (like cybercafe etc).
8. Low Security Websites
Here the question comes how our Facebook account can be hacked by a low security website ? Again we need to scan human’s brain. Most of common internet user have accounts in multiple websites. To remember passwords easily users use same passwords everywhere.
Here is a chance if any old (not updated) or low security website’s database got hacked then the attacker can try those hacked passwords to log in our Facebook account.
How to be safe from low security websites?
- Choose different passwords for different websites.
- Must choose an unique long password for e-mail, Facebook and other social media.
9. Viruses or Malware
Some times in our devices such as phone and computer may be infected with malicious software like virus, malwares or spywares. These types of apps sends our all saved passwords and cookies in browsers to the hacker. In this way our accounts can be terminated.
How to be safe from viruses?
- We should not download 3rd party applications, because hackers can bind a malicious application in a normal looking application. We should always download from the official app store.
- We should not click on any suspicious link.
- If we are using Windows PC then we should buy a good antivirus, anti-spyware, antimalware for our computer, and keep updating it.
So, this is how our Facebook account got hacked. From this tutorial we learned how to be safe, and Facebook hacking is very easy if the user is careless. There are some zero day hacking. Great hackers able to find vulnerabilities in Facebook or Instagram but we don’t need care for this. Facebook developers will fix it as soon as possible. Zero day attackers normally targets the celebrates because zero day attacks is the code exploit attacks that we talked on the starting of this tutorial. This type of hacks needs high end skills and hard works, for this they normally don’t choose normal users they targets well known personalities or celebs.
We need to make our Facebook stronger. Follow our provided steps and be safe from Facebook hacking.
This tutorial is for new learners who is new in this field. Everyone should have an clear idea how Facebook, Instagram and other social media account can be hacked and how to be safe. This tutorial is for educational purpose only. Hacking Facebook, Instagram or any other account is a serious crime. If anyone do any illegal activity then we are not responsible for that.
Love our writings? Make sure to follow us on Twitter and GitHub, we post article updates there.
To join our family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity.
For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.