March 30, 2023
Let’s make a hot cup of coffee, and listen to the presentation.
………………………
………………………………..
………………………………………………..
CHFI v10 Practice Test (Full 600+ Questions)
https://www.udemy.com/course/chfi-v10-certmaster-exam-prep/?referralCode=79DFFB9D994A3B22461A
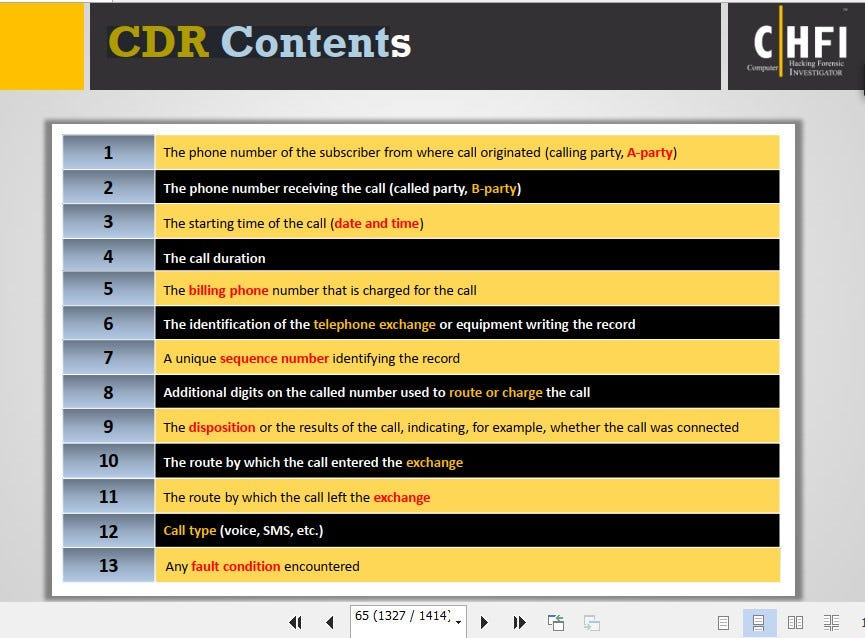
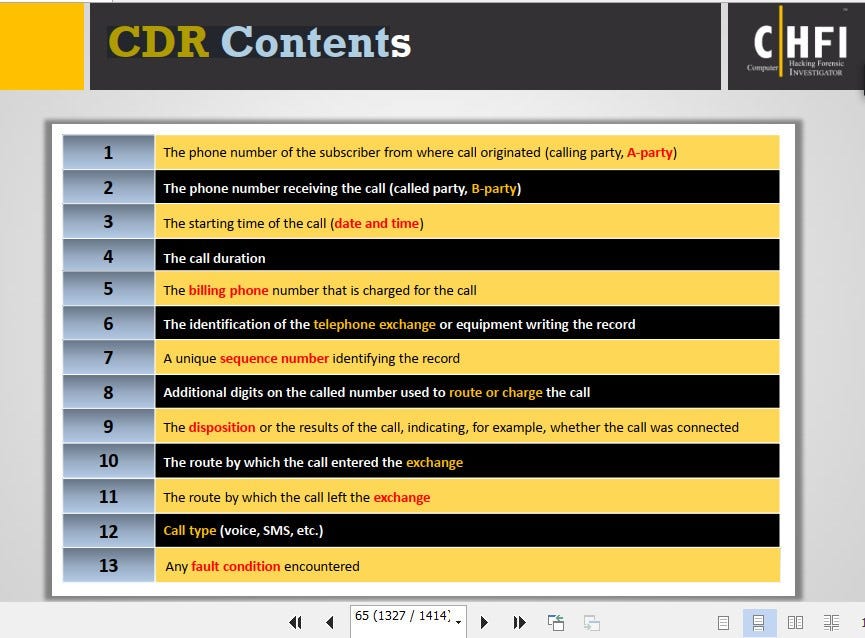
34. A call detail record (CDR) provides metadata about calls made over a phone service. From the following data fields, which one is not contained in a CDR.
The call duration
A unique sequence number identifying the record
Phone number receiving the call
The language of the call
Correct answer The language of the call is not typically contained in a Call Detail Record (CDR).
A Call Detail Record (CDR) is a data record that provides metadata about calls made over a phone service. CDRs are generated by telephone exchanges and other network elements and are used to track and bill for phone usage.
A typical CDR contains information such as the date and time of the call, the phone number of the calling party, the phone number of the called party, the call duration, and a unique sequence number that identifies the record. The information contained in a CDR is used for billing purposes, network planning, and to support network troubleshooting and analysis.
The language of the call is not typically contained in a CDR. CDRs are primarily focused on tracking and billing for the usage of the phone network, and do not typically include information about the content of the call, such as the language used. This information is not necessary for billing purposes and is typically not collected or stored by the phone network.
In conclusion, a CDR provides metadata about calls made over a phone service, including information such as the date and time of the call, the phone numbers involved, the call duration, and a unique sequence number. The language of the call is not typically contained in a CDR.
35. Frank, a cloud administrator in his company, needs to take backup of the OS disks of two Azure VMs that store business-critical data. Which type of Azure blob storage can he use for this purpose?
Page blob
Block blob
Medium blob
Append blob
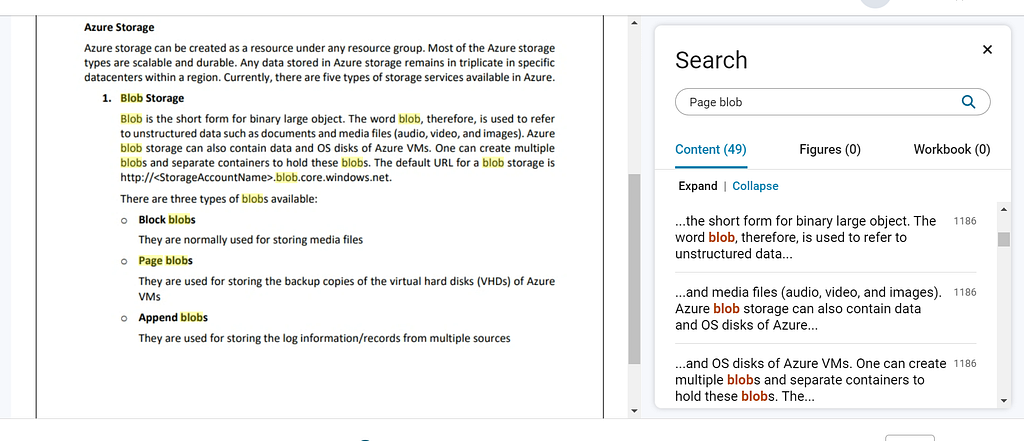
Correct answer is Page blobs, Page blobs used to backup virtual hard disks (VHDs) in Azure and can be used to store the operating system disks of Azure VMs. Page blobs are similar to block blobs but are optimized for random read/write operations and are used to store virtual hard disks (VHDs) in Azure. Because of their optimized random read/write capabilities, page blobs are often used for storage of data that requires frequent read/write access, such as virtual hard disks for Azure VMs.
In conclusion, either Block blobs or Page blobs can be used for backing up the operating system disks of Azure VMs, depending on the specific requirements of the backup and the data being stored.
Page blobs are a collection of 512-byte pages, which provide the ability to read/write arbitrary ranges of bytes. Hence, page blobs are ideal for storing index-based and sparse data structures like OS and data disks for Virtual Machines and Databases
36. William is examining a log entry that reads 192.168.0.1 — — [18/Jan/2020:12:42:29 +0000] “GET / HTTP/1.1” 200 1861. Which of the following logs does the log entry belong to?
The common log format of Apache access log
Apache error log
The combined log format of Apache access log
IIS log
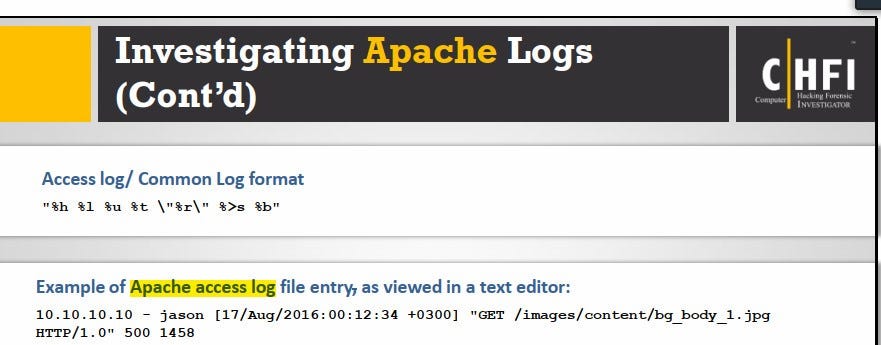
The log entry belongs to the common log format of Apache access log.
The common log format is a widely used standard for logging HTTP requests in Apache web servers. The common log format records information about each HTTP request processed by the server, including the IP address of the client, the date and time of the request, the requested URL, the HTTP status code returned by the server, and the size of the response in bytes.
The log entry in question contains information that matches the common log format, including the client IP address (192.168.0.1), the date and time of the request (18/Jan/2020:12:42:29 +0000), the requested URL (GET / HTTP/1.1), the HTTP status code (200), and the size of the response (1861 bytes).
In conclusion, the log entry belongs to the common log format of Apache access log, which is a widely used standard for logging HTTP requests in Apache web servers.
37. POP3 is an Internet protocol used to retrieve emails from a mail server. Through which port does an email client connect with a POP3 server?
25
143
993
110
37. An email client connects with a POP3 server through port 110.
POP3 (Post Office Protocol version 3) is a widely used Internet protocol for retrieving emails from a mail server. An email client, such as Microsoft Outlook, connects to a POP3 server using port 110, the standard port for POP3 communication.
38. Which tool allows dumping the contents of process memory without stopping the process?
pmdump.exe
pdump.exe
processdump.exe
psdump.exe
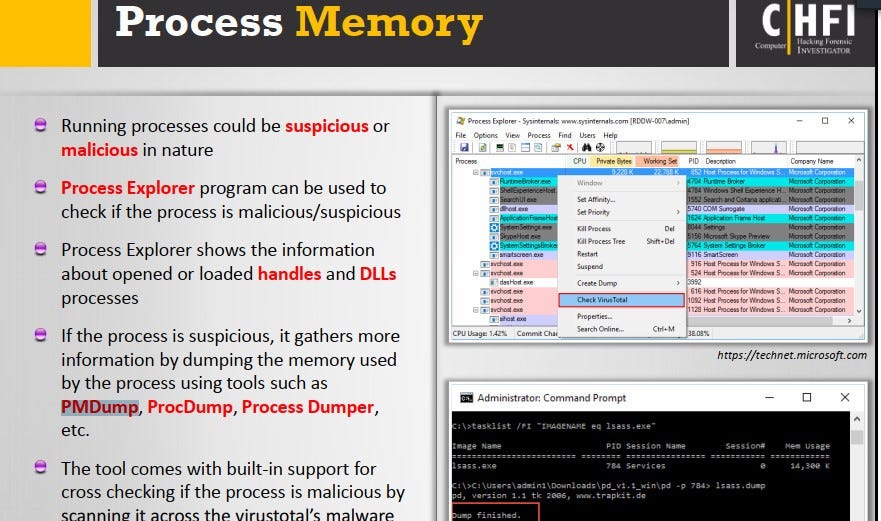
The tool that allows dumping the contents of process memory without stopping the process is psdump.exe.
PsDump is a tool that allows dumping the contents of process memory without stopping the process. It can be used to capture and analyze the memory of running processes, which can be useful in forensic investigations and incident response.
39. James, a hacker, identifies a vulnerability in a website. To exploit the vulnerability, he visits the login page and notes down the session ID that is created. He appends this session ID to the login URL and shares the link with a victim. Once the victim logs into the website using the shared URL, James reloads the web page (containing the URL with the session ID appended) and now, he can browse the active session of the victim. Which attack did James successfully execute?
Cross-site request forgery
Cookie tampering
Parameter tampering
Session fixation attack
39. James successfully executed a session fixation attack.
A session fixation attack is a type of web security vulnerability that allows an attacker to fixate or manipulate the session ID of a user. By doing so, the attacker can gain unauthorized access to the user’s session and sensitive information.
In the scenario described, James identified a vulnerability in a website, created a session ID, and shared the link with a victim. Once the victim logged in using the shared link, James reloaded the web page and now had access to the victim’s active session. This is an example of a session fixation attack, where the attacker manipulates the session ID to gain unauthorized access to the user’s session.
40. Consider that you are investigating a machine running a Windows OS released prior to Windows Vista. You are trying to gather information about the deleted files by examining the master database file named INFO2 located at C:Recycler<USER SID>. You read an entry named “Dd5.exe.” What does Dd5.exe mean?
D drive, fourth file restored, a .exe file
D drive, fourth file deleted, a .exe file
D drive, sixth file deleted, a .exe file
D drive, fifth file deleted, a .exe file

In Windows operating systems released prior to Windows Vista, when a file is deleted, it is stored in the Recycler folder, which is a hidden folder located in the root of each drive. The Recycler folder contains a subfolder for each user account on the machine, identified by the SID (Security Identifier) of the user. Each subfolder contains a master database file named INFO2, which records information about the deleted files in the form of binary data.
The INFO2 file is a binary file that stores information about the deleted files, including the file name, path, deletion time, and other metadata. The file name is recorded using a naming convention that starts with the letter “D” (indicating that the file has been deleted) followed by a number, indicating the order in which the file was deleted, starting from 0. The extension of the file is also recorded, in this case, “.exe” indicating that the file was an executable file.
So, in this case, the entry “Dd5.exe” would indicate that a file named “Dd5.exe” was the fifth file deleted from the D drive.
41. Which of the following event correlation approach is an advanced correlation method that assumes and predicts what an attacker can do next after the attack by studying the statistics and probability and uses only two variables?
Route correlation
Bayesian correlation
Vulnerability-based approach
Rule-based approach
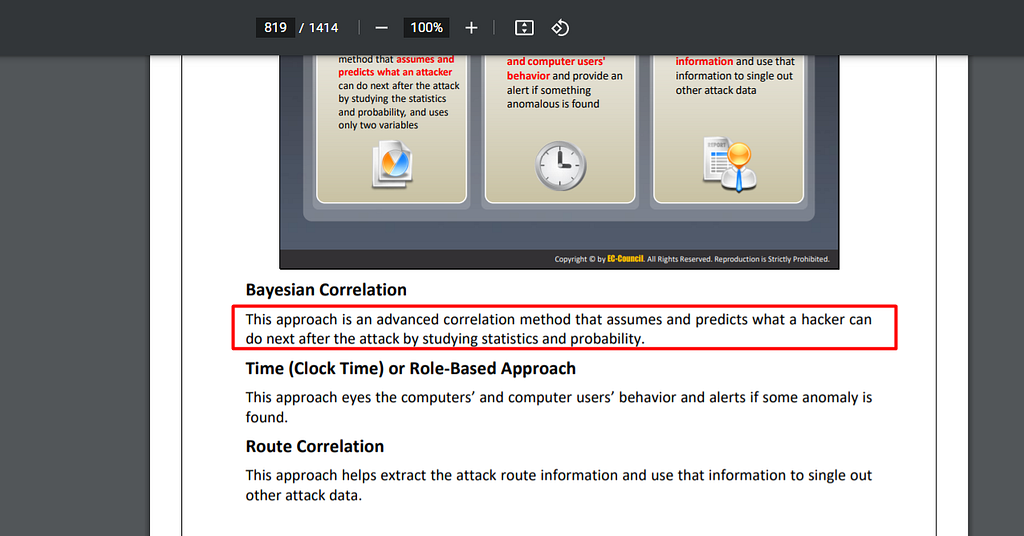
Bayesian correlation is an advanced event correlation approach that uses statistical and probabilistic methods to predict what an attacker may do next after an attack has been detected. Unlike the rule-based approach, which uses pre-defined rules to trigger an alert, Bayesian correlation takes into consideration multiple variables, including historical data and current events, to determine the likelihood of a security breach. This approach is considered more advanced because it allows for a more nuanced and dynamic response to potential threats.
Bayesian correlation is an advanced event correlation approach that involves using statistical and probabilistic methods to determine the likelihood of future events based on past events. This approach is based on Bayes’ theorem, which states that the probability of an event occurring can be calculated based on prior knowledge of similar events and the relationships between them.
In the context of security event correlation, Bayesian correlation can be used to predict what an attacker might do next after an initial attack. This is accomplished by analyzing the statistics and probabilities of past attacks, and then applying this knowledge to predict the likelihood of future attacks.
Bayesian correlation is considered an advanced method because it involves using complex mathematical models and algorithms to analyze large amounts of data and determine the likelihood of future events. This approach can be more accurate than other correlation methods, but it also requires a significant amount of computational resources and specialized knowledge to implement effectively.
42. Which Linux command displays kernel ring buffers or information about device drivers loaded into the kernel?
grep
dmesg
pgrep
fsck
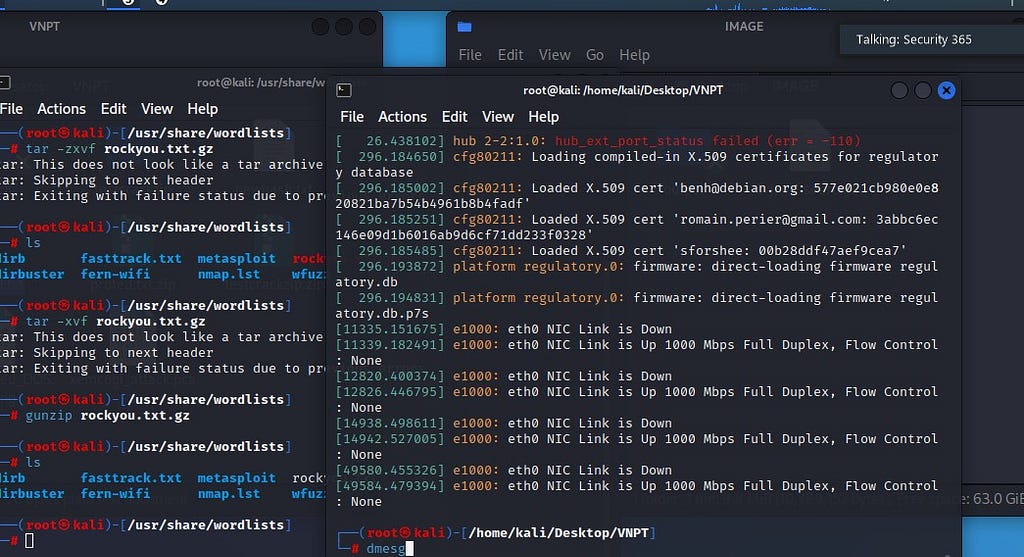
Correct answer is dmesg
The dmesg command in Linux is used to display the kernel ring buffer, which is a log of system messages and information about device drivers that have been loaded into the kernel. The output of the dmesg command includes information about system startup, system errors, and driver-related events, among other things. The dmesg command can be useful for debugging and troubleshooting issues with the kernel and device drivers.
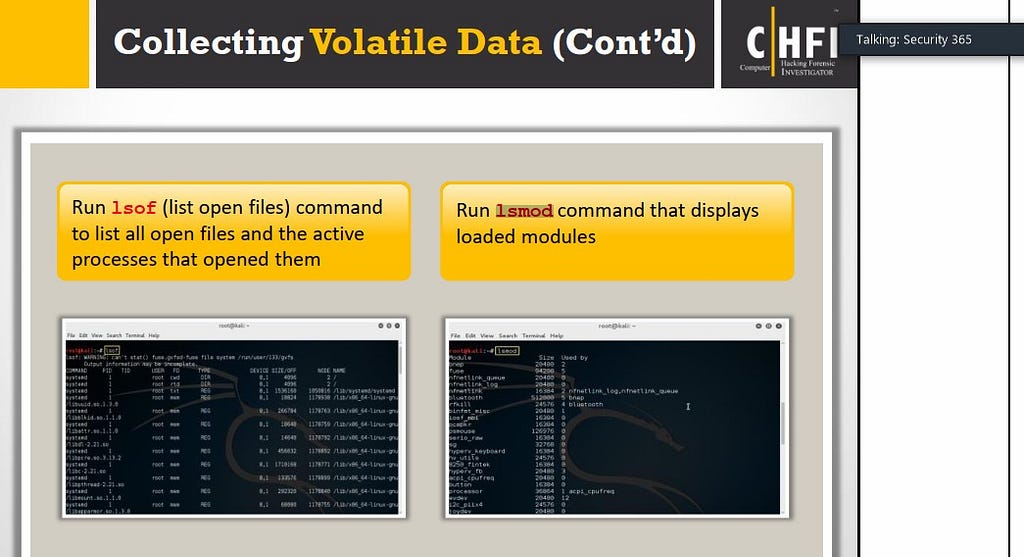
43. Which command can provide investigators with details of all the loaded modules on a Linux-based system?
lsof -m
list modules -a
plist mod -a
lsmod
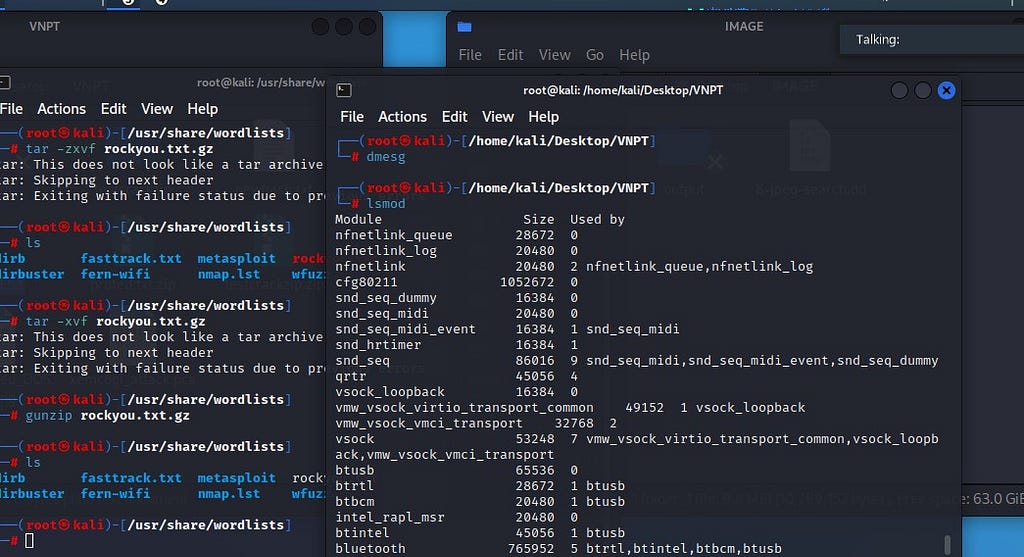
The correct command to provide investigators with details of all the loaded modules on a Linux-based system is lsmod. The lsmod command displays the status of all modules loaded into the Linux kernel. It provides information such as the module name, size, used by, and other details. The information displayed by lsmod can be useful for forensic investigations as it provides information about the device drivers and other modules that are currently loaded into the kernel.
44. Adam is thinking of establishing a hospital in the US and approaches John, a software developer to build a site and host it for him on one of the servers, which would be used to store patient health records. He has learned from his legal advisors that he needs to have the server’s log data reviewed and managed according to certain standards and regulations. Which of the following regulations are the legal advisors referring to?
Payment Card Industry Data Security Standard (PCI DSS)
Health Insurance Portability and Accountability Act of 1996 (HIPAA)
Electronic Communications Privacy Act
Data Protection Act of 2018
The legal advisors are referring to the Health Insurance Portability and Accountability Act of 1996 (HIPAA). HIPAA is a federal law in the United States that provides data privacy and security provisions for safeguarding medical information. It is mandatory for healthcare organizations to comply with HIPAA regulations and ensure that protected health information (PHI) is stored, processed, and transmitted securely.
CHFI v10 Practice Test (Full 600+ Questions)
https://www.udemy.com/course/chfi-v10-certmaster-exam-prep/?referralCode=79DFFB9D994A3B22461A
Article posted by: https://certmaster.me/chfi-v10-practice-exam-ecc-council-312-49-part-2-421212461aab?source=rss-d9e5f258a4e8——2
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com