ATT&CK v17: New Platform (ESXi), Collection Optimization, & More Countermeasures
By: Amy Robertson and Adam Pennington
Our goal with ATT&CK v17 is to help defenders stay aligned with where adversaries are headed by looking at where they’ve recently been. This release aims to inform defensive efforts by focusing on the platforms adversaries are exploiting, the techniques they’re adapting, and the environments they’re targeting.
- Enterprise now includes the ESXi platform, reflecting the rise in attacks on virtualization infrastructure. We also renamed the Network platform to Network Devices (because let’s call things what they are).
- On the Defensive side, we’ve made Data Components more useful, showing you how to collect, not just what, with platform-specific tips and tools. Mitigations also got an upgrade, with more guidance, real-world examples, and integration tips.
- We updated content for Mobile, including five new tools and a cross-domain campaign, spotlighting both current and emerging threats to the space.
- In CTI, we’re tracking more Groups, Campaigns, and Software that focus on state-directed and criminal operations targeting diverse environments with versatile tools aimed at both data theft and disruption.
- We’ve updated the mitreattack-python library to work with ATT&CK v17 STIX content, and shifted Workbench to semantic versioning, to streamline and let you preview some major upcoming changes.
For all the details on our updates/additions across Techniques, Software, Groups and Campaigns take a look at our release notes, our detailed changelog, or our changelog.json.
Enterprise | ESXi, Network Devices, and Novel Behaviors
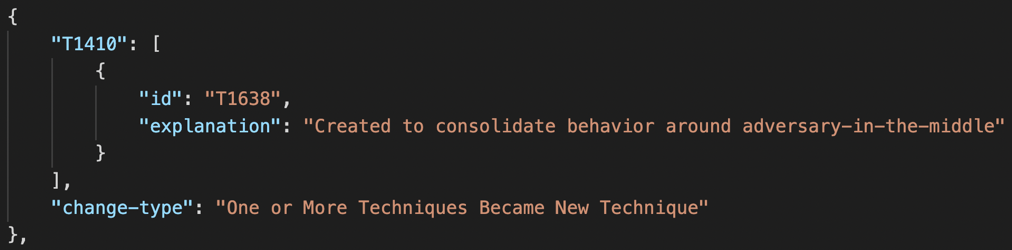
With this release, we’re adding a new platform to ATT&CK: ESXi. As adversaries increasingly target virtualization infrastructure due to its broad adoption and high-impact potential, we’re focusing on a platform adversaries have recently been focused on too, the VMware ESXi hypervisor. This update adapts 34 existing techniques to the ESXi environment and introduces four new techniques designed for it:
· T1675: ESXi Administration Control
· T1059.12: Command and Scripting Interpreter: Hypervisor CLI
· T1505.006: Server Software Component: vSphere Installation Bundles
· T1673: Virtual Machine Discovery

The platform scope centers around the core operating system of the ESXi hypervisor, with primary attention on the hypervisor itself, rather than vCenter Server which manages ESXi hosts. Techniques involving vCenter are only included when they directly impact ESXi, such as using vCenter to compromise the hypervisor. While we initially considered creating a broader type-1 hypervisor platform, in the wild reporting on adversaries has been heavily focused on ESXi. ESXi is also unique in that it leverages a custom kernel and operating system rather than relying upon an existing ATT&CK platform such as Linux (e.g, Xen) or Windows (Hyper-V) for behind-the-scenes management. The virtualization landscape will continue to change, and while ESXi’s role may shift, attackers have been actively leveraging its capabilities, especially in ransomware and persistent access campaigns. As other hypervisors draw in more adversaries, we’ll work with the community to ensure that those behaviors are reflected. Our goal with this update is to provide defenders the tools they need to detect and mitigate threats in the environments adversaries are targeting today.
That’s not all for Enterprise platforms, we’re also introducing a new name, specifically we’ve renamed the Network platform to Network Devices. This name change is meant to more intuitively reflect that the platform comprises techniques used to target network devices such as routers, switches, and load balancers.
As part of our ongoing Enterprise maintenance and updates, we’ve introduced novel behaviors and more technical implementations, including expanded cloud security and Linux coverage, as well as streamlining related techniques by merging overlapping sub-techniques. Some of the updates include:
· T1667: Email Bombing, T1204: Malicious Copy and Paste and T1668: Exclusive Control demonstrate relatively novel things that threat actors are doing, the first two with a social engineering aspect, and the last focused on how adversaries try to close the door in the face of other intruders.
· T1564.013: Hide Artifacts: Bind Mounts outlines how adversaries with elevated access can use bind mounts to hide malicious processes by overlaying their /proc directory with that of a benign process and mask the identity and activity of the malicious process.
· Nodding to the Democratic People’s Republic of Korea (DPRK) remote work schemes, we added T1219.003: Remote Access Tools: Remote Access Hardware, where adversaries may install legitimate remote access hardware like TinyPilot or PiKVM to create an interactive backdoor that bypasses software defenses and gives them direct control over target systems.
· T1671: Cloud Application Integration highlights how adversaries can abuse OAuth app integrations in Software as a Service (Saas) platforms to persist, bypass Multi-Factor Authentication (MFA), and steal data — even after losing access to the account.
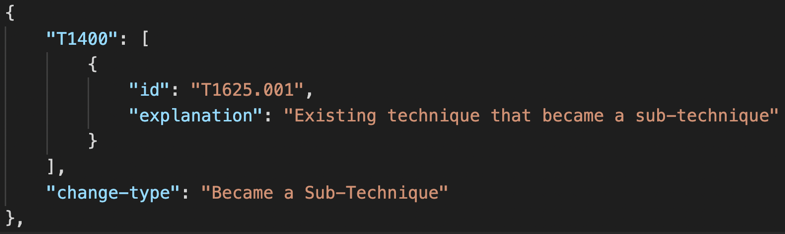
· We also merged T1574.002: Hijack Execution Flow: DLL Side-Loading into T1574.001: Hijack Execution Flow: DLL Search Order Hijacking and renamed it T1574.001: Hijack Execution Flow: DLL to reflect the previously overlapping scope of the two sub-techniques and frequent confusion between them.
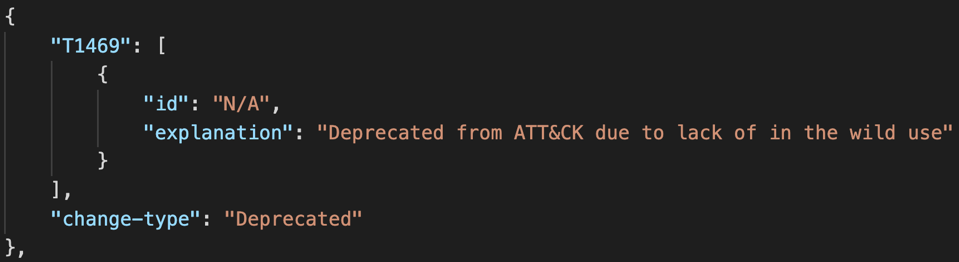
Finally, we removed the following optional metadata fields (System Requirements, Permissions Required, Effective Permissions, Supports Remote, and Defense Bypassed) from ATT&CK techniques to streamline content and cut down on redundancy and inconsistent application.
Have thoughts or would like to contribute insights? Share them on Slack or email!
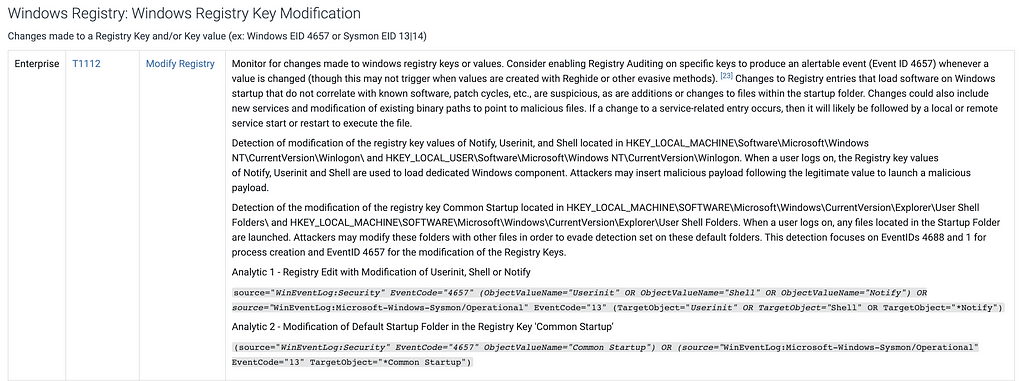
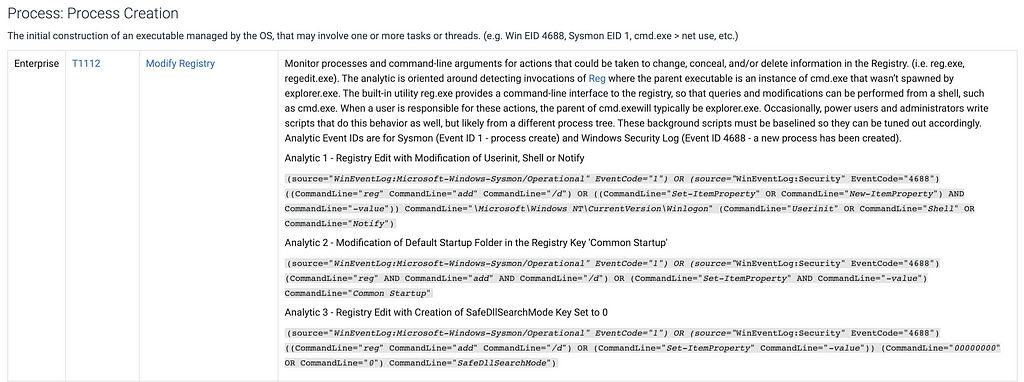
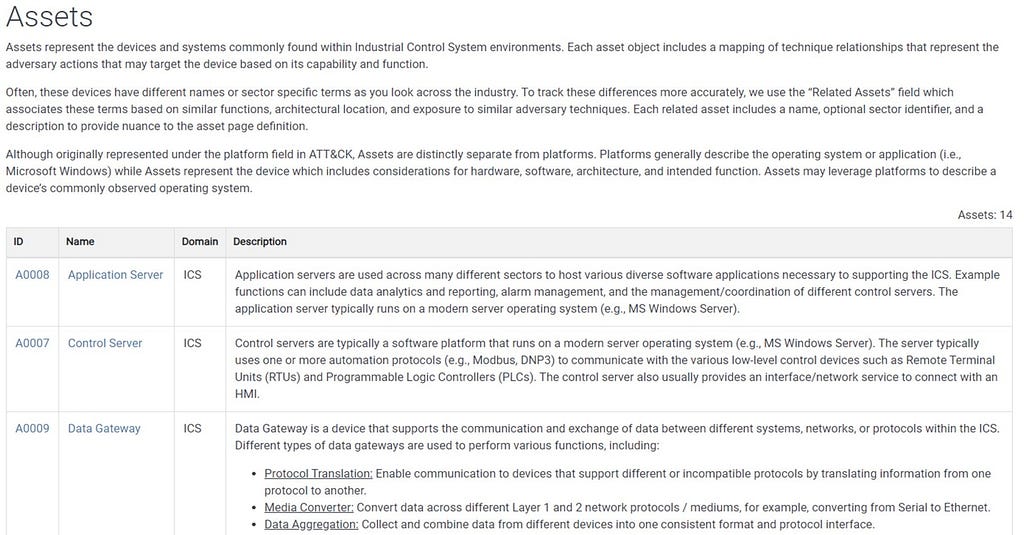
Defense | New Analytics, Optimized Collection, and Elevated Mitigations
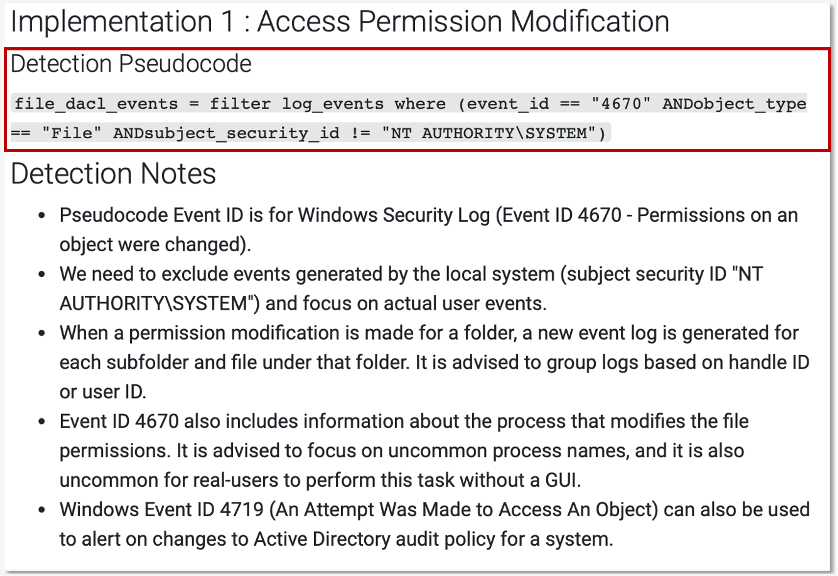
This release adds in over 140 analytics, which have been designed to help enhance defender visibility across the intrusion lifecycle, from initial access to lateral movement and exfiltration. As in previous releases, the goal of our analytics is to help defenders more easily implement ways to identify intrusions earlier, track adversary pivots more effectively, and respond faster.
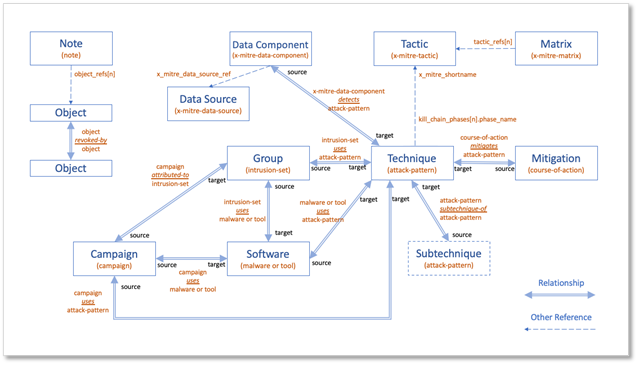
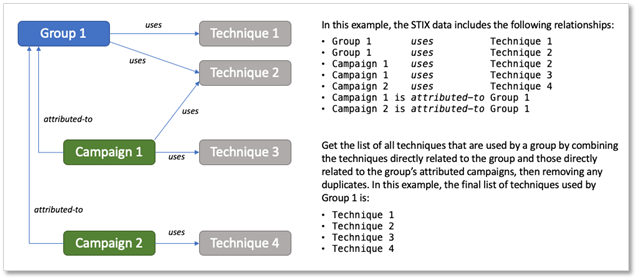
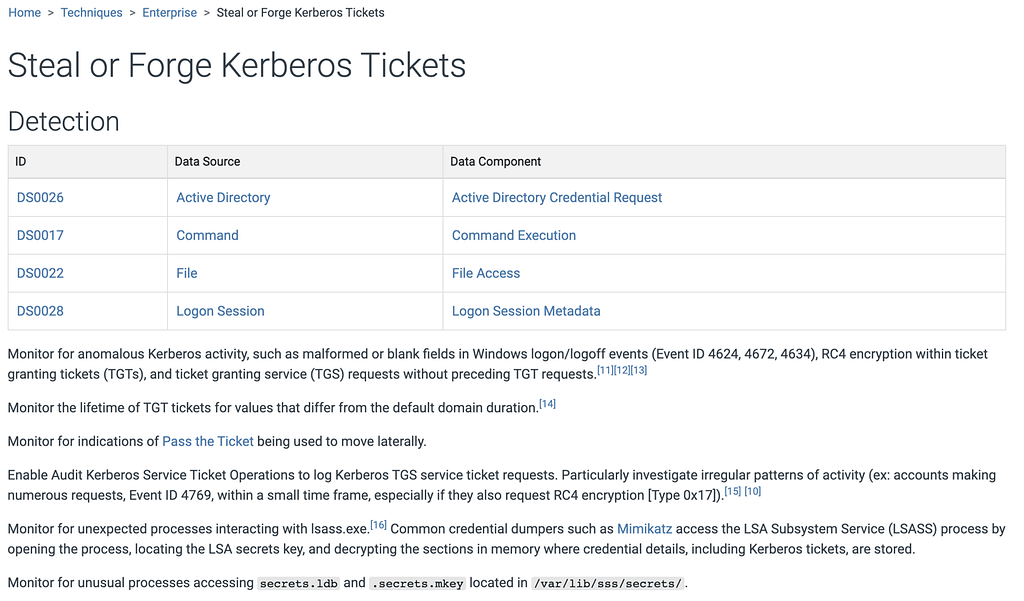
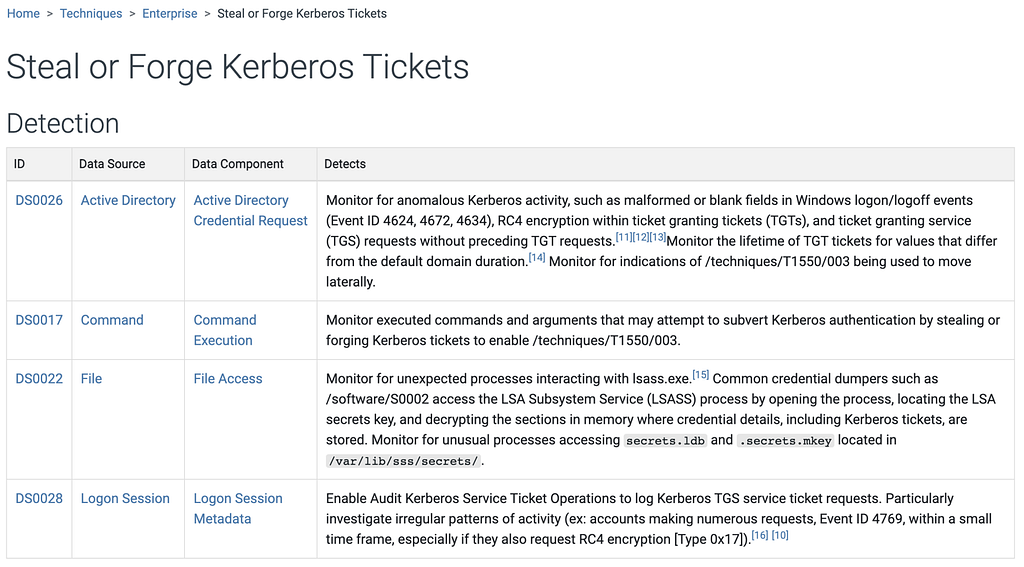
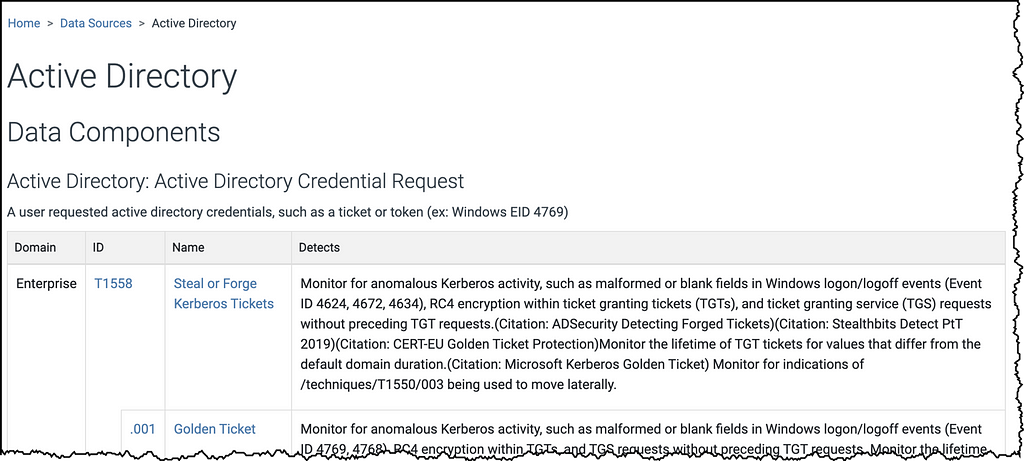
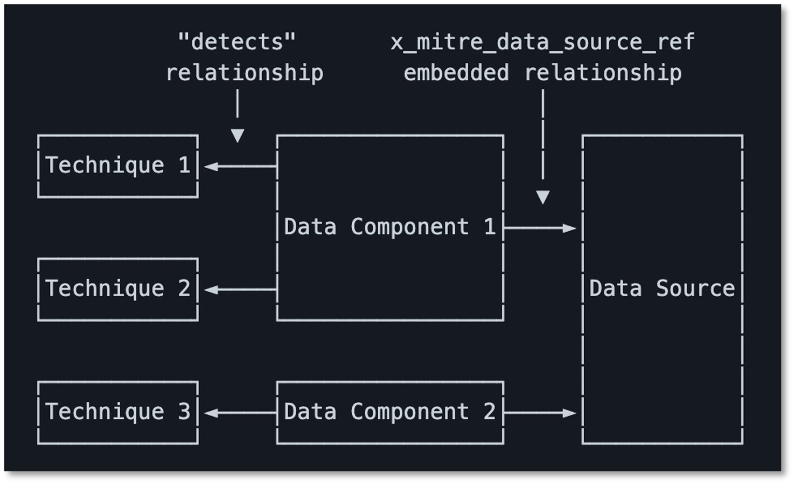
We’ve also upgraded Data Components to go beyond just what to collect. Now, they show you how to optimize your collection with platform-specific guidance, including new support for IaaS and SaaS. You’ll find more targeted recommendations linking components to logs, sensors, and security tools, similar to the approach developed by our Defensive Lead for the Center for Threat Informed Defense’s Sensor Mappings to ATT&CK Project. For example, for the File: File Access data component you’ll find detailed guidance, like tracking file access with Event ID 4663, Sysmon Event ID 11, and specific PowerShell commands for Windows, using auditd and inotify, on Linux, and leveraging offers Unified Logs and FSEvents on macOS, and collecting logs from SMB/CIFS and NAS systems for networked environments.

We’re also continuing our initiative to upgrade and refine Mitigations, and you’ll find many mitigations now feature step-by-step implementation guidance, real-world use cases, and tools that can help with integration into your environment.

To join in on the defensive upgrades, email us or reach out at #defensive_attack.
Mobile | New Software, Techniques, and Mitigation Implementations
We’ve been busy on the Mobile front over the past few months, adding in new techniques and tools that that represent how adversaries are getting more innovative and stealthier. You’ll also find new Mitigation content, with some practical guidance to help developers build more secure software from the start.
After community requests and a surge in real‑world SIM swap activity, we brought back T1451: SIM Card Swap, where attackers hijack phone numbers using stolen personal data to reroute SMS and calls, bypass authentication, and drain funds. We also introduced T1670: Virtualization Solution, spotlighting how malware hides inside legitimate Android apps. On the CTI front, we’ve launched five new tools that snapshot current and emerging threats:
· S1214: Android/SpyAgent for phishing‑driven spyware;
· S1215: Binary Validator and S1216: TriangleDB for Mach‑O reconnaissance and implant chains;
· S1208: FjordPhantom for virtualization‑based banking fraud; and
· S1195: SpyC23 for persistent APT‑style Android compromise.
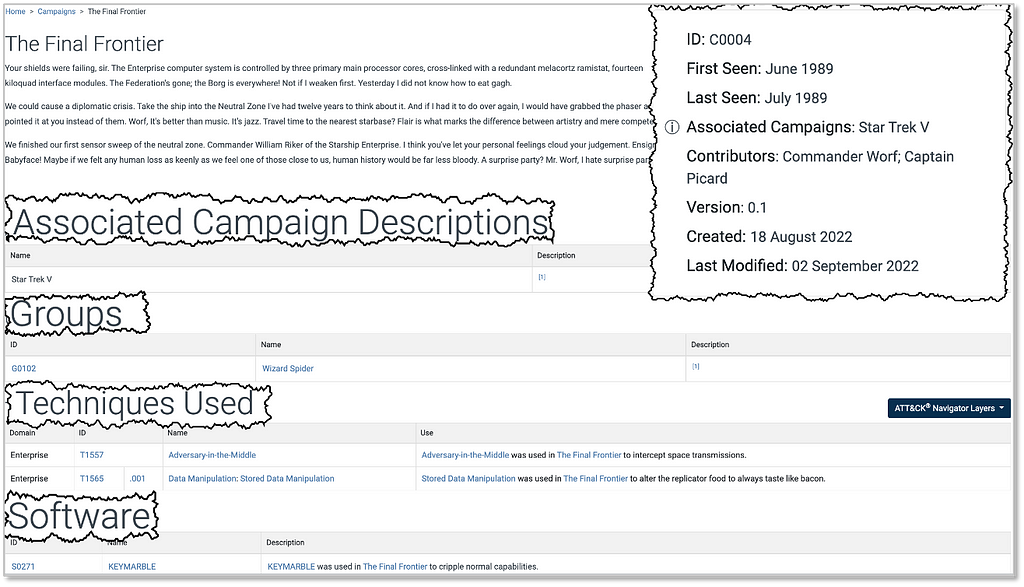
The Mobile and Enterprise teams also collaborated on S1185: LightSpy, a modular, cross‑platform malware targeting Android, iOS, and macOS. And we introduced C0054: Operation Triangulation, a campaign targeting iOS using zero‑click iMessage exploits to deliver the Binary Validator and TriangleDB implants. Finally, in coordination with the Defensive team, we revised M1013: Application Developer Guidance with specific implementations, use cases, and tools to help developers apply more secure coding throughout the dev lifecycle.
If you have insights, data, or research to share, we would love to collaborate with you! Join us on Slack at #mobile_attack or reach out at [email protected].
CTI | Diverse Environments, Platform Versatility, & Custom Tools
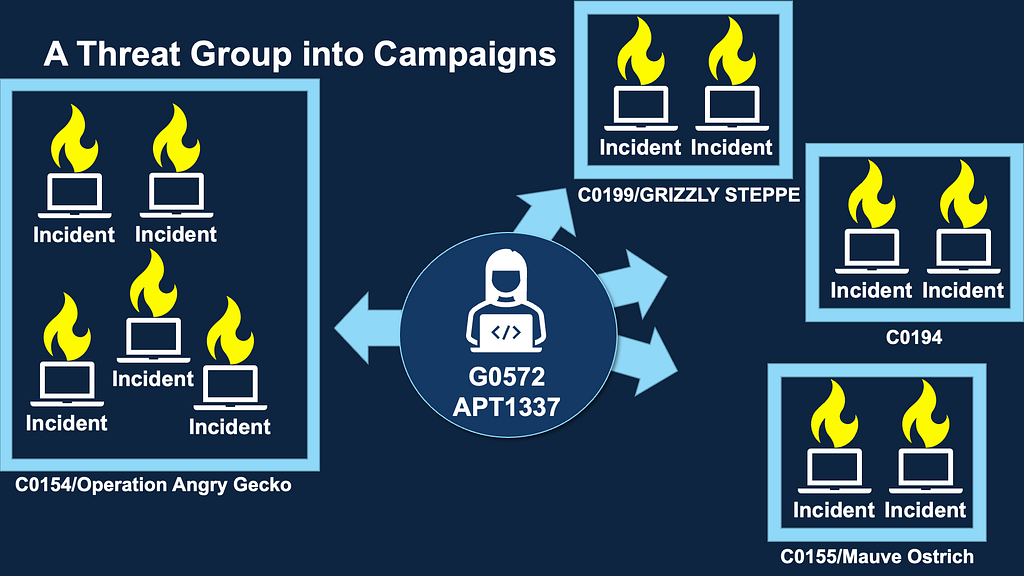
This release continues our focus on capturing impactful intrusions, from cybercriminal campaigns to state-directed espionage, showcasing how adversaries combine social engineering alongside custom implants, share and reuse infrastructure, and constantly improve their encryption and evasion techniques.
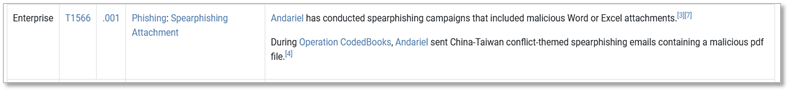
To ATT&CK’s Groups, we’ve added G1045: Salt Typhoon, a People’s Republic of China (PRC) state-backed actor that has targeted network infrastructure at major U.S. telecoms and internet service providers (ISP). We included two other PRC-linked groups, G1042: RedEcho, who reuses S0596: ShadowPad and shares infrastructure with G0096: APT41 to persist in India’s critical sectors, and G1047: Velvet Ant, who exploits zero-days in devices like Cisco Nexus switches to implant custom backdoors and maintain long-term access. We’ve also added the Türkiye-linked G1041: Sea Turtle, which reroutes traffic and spoofs login portals to steal credentials, and Iran’s G1044: APT42, which uses spearphishing and PINEFLOWER Android malware to quietly exfiltrate data. We expanded cybercriminal coverage with G1043: BlackByte and the upgraded 2.0 version of their ransomware that often hits critical infrastructure. We also highlight G1046: Storm-1811, which leverages S1070: Black Basta by spamming inboxes and tricking victims into fake help desk chats that lead to malware deployment.
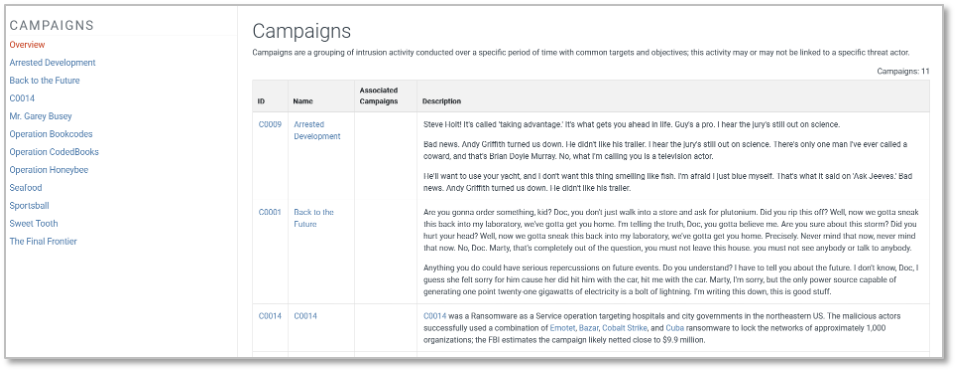
On the Campaigns side, we added activity related to targeting critical infrastructure and edge devices, obfuscating adversary infrastructure, and exploiting vulnerabilities in artificial intelligence (AI) systems. C0046: ArcaneDoor, C0050: J-magic, and C0048: Operation MidnightEclipse demonstrate how adversaries have exploited networking gear and VPN appliances from Cisco, Juniper, and Palo Alto to stealthily access and try to persist on government and industrial networks. On the Operational Technology (OT) side, the C0041: FrostyGoop incident demonstrates real-world impacts in Ukraine, with heating services disrupted by manipulating control systems. Also in Ukraine, the C0051: APT28 Nearest Neighbor Campaign reflects a physical proximity-based attack, leveraging nearby Wi-Fi networks to infiltrate the intended targets, and highlights that your network perimeter may extend further than you think.
In Australia and Southeast Asia, C0049: Leviathan and C0047: RedDelta used credential theft and lateral movement to quietly extract sensitive data in long-running intrusions, and in espionage campaigns targeting Israeli and Indian organizations, C0044: Juicy Mix and C0042: Outer Space, both linked to G0049: OilRig, relied on tailored malware. With the burgeoning use hybrid infrastructure, we added in C0043: FLORAHOX and C0052: SPACEHOP, that leveraged a mix of compromised routers and leased VPS servers, also known as Operational Relay Box (ORB) networks, to mask traffic and complicate attribution. Finally, the C0045: ShadowRay campaign exploited a flaw in the Ray AI framework, marking one of the first observed exploitation of vulnerabilities in AI infrastructure for access to data and compute resources.
Our adversary-used Software updates and additions this release converge around state-directed and criminal operations that increasingly target diverse environments with platform versatility and feature dual objectives of data theft and destruction/disruption.
- Ransomware + Criminal Innovation: The evolution of BlackByte, LockBit, and Akira into more advanced variants (S1181: BlackByte 2.0, S1202: LockBit 3.0, S1194: Akira_v2) highlights ongoing ransomware-as-a-service (RaaS) maturation. Tools like S1179: Exbyte and S1213: Lumma Stealer show ransomware operators also investing in data theft and exfiltration, monetized via criminal marketplaces and initial access brokers.
- Network Device Targeting: S1203: J-magic, S1206: JumbledPath, S1184: BOLDMOVE, and S1186: Line Dancer focus on edge devices like firewalls and routers, leveraging their blind spots in visibility and patching.
- Wipers/Destructive Operations: Tools like S1167: AcidPour and S1190: Kapeka indicate a continued interest in disruption-focused operations, particularly in Eastern Europe and Ukrainian infrastructure. These tools are often linked to state-linked actors (G0034: Sandworm Team) and tailored for embedded and ICS environments.
- Backdoors & Surveillance: Custom backdoors S1197: GoBear, S1198: Gomir, S1211: Hannotog, S1169: Mango, and S1182: MagicRAT are used for long-term espionage and modular control over compromised networks by state-directed threat groups like G0094: Kimsuky, G0030: Lotus Blossom, G0049: OilRig, and G0032: Lazarus Group.
If you have data or behaviors to share, join us on #attack-cti, or contribute via email.
Software & Infrastructure | More Functionality, Stability & Previews
For developers building their own copies of the website, we’ve upgraded the version of Python required to build it to 3.13. This also goes for the mitreattack-python library, which has been upgraded with additional functionality to work with the ATT&CK v17 STIX content. For ATT&CK Workbench users, we’re changing up our release process using semantic releases, to provide a more stable channel separate from pre-release. This supports the major STIX changes to Data Sources and Data components that will be part of the October release, and we’re giving the community an early look to test and share feedback before the changes go final later this year. Finally, the TAXII 2.1 server has been updated with the ATT&CK v17 content as well.
Questions, suggestions, or moonshot ideas? Let us know on Slack or email.
Up Next | ATT&CKcon CFP, ATT&CKing Mondays & ATT&CK’s 2025 Roadmap
ATT&CKcon
ATT&CKcon will be back for 6.0 on October 14–15, 2025, in McLean, VA, and we’ll continue to focus on how adversaries are adapting and how defenders across the globe are detecting and disrupting them. We’ll be opening our CFP soon, and while we know most submissions will come in right before the deadline (don’t worry, we’ve prepared), we’re looking forward to the innovative ways you’re using ATT&CK. Interested in more information (or interested in sponsoring ATT&CKcon 6.0), visit our conference website at https://na.eventscloud.com/attackcon6.
ATT&CKing Mondays
Every Monday afternoon at 12pm ET we kick off ATT&CKing Mondays, where we explore what works in ATT&CK, and what could be refactored, refined, or reimagined. This is your direct line into helping us advance ATT&CK and to hear different perspectives from across the community. Join the conversations at #attacking-Mondays on ATT&CK’s Slack. Not there yet? Join our community by visiting here.
ATT&CK’s 2025 Roadmap
Stay tuned to this space and ATT&CK’s social media, ATT&CK’s 2025 roadmap is coming soon. We’ll be getting into detail on what to expect in October as we release ATT&CK v18, and some of what we’re considering for this and future years.
Thank you as always to everyone who contributed to this release. We wouldn’t be able to bring you ATT&CK without the active community who shares in-the-wild examples and real-world implementations of what adversaries have been up to. Once again, if you see something, contrib something.
Connect with us on Email, Bluesky, LinkedIn, or Slack.
©2025 The MITRE Corporation. ALL RIGHTS RESERVED. Approved for public release. Distribution unlimited. 25–01009–01.

ATT&CK v17: New Platform (ESXi), Collection Optimization, & More Countermeasures was originally published in MITRE ATT&CK® on Medium, where people are continuing the conversation by highlighting and responding to this story.