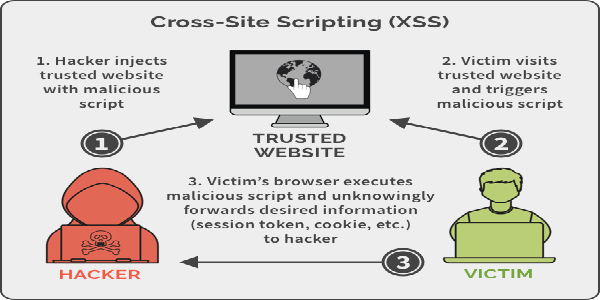
How to Stay Anonymous Completely [100% Perfect]
In today’s article we are going to discuss about how we can be anonymous on the internet, because we all love privacy. Sometimes we need to do some private jobs on the internet. So anonymity is important. We can say we can use Tor, VPN to be anonymous. But that’s totally not true.
The perfect say is “Privacy is a myth“. We can use the Tor, VPN, Proxychains etc to increase our privacy, but those methods are not totally bulletproof. But in this article we are going to discuss about some techniques that will be really helpful to be more anonymous on the internet. This is going to be another level of anonymity if we didn’t do any mistake from our side.
Before going further we need to have a clear idea about Tor and VPN like stuffs. After that we are good to go. As we know that Tor a very good way to be anonymous on internet, but some services detects that we are using Tor and restricts us to use the services. A good example is Google.
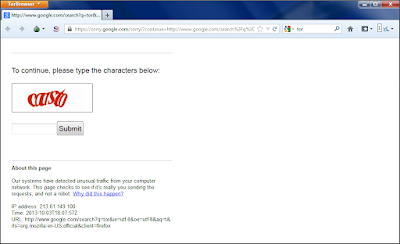 |
| Google catch Tor network |
Also the VPN providers may keep our activity logs on their database (Paid VPN providers told that, they don’t keep logs. But can we trust them? let us know in the comment section below). Then what to do?
Be Anonymous Online
So, in this article we are going to talk about a easy, fast and effective way to be anonymous online. By following this real IP address will be very very hard to detect by anyone on the world, we just need to finish the article totally to get the pro idea.
The idea is easy yet powerful. We are going to use Tor and Proxychains together. First we run Tor then we run our proxychains. By doing this services like Google TorCheck etc will get the IP address of our proxy servers and those proxyservers also don’t have our real IP address, they have the IP address of our Tor. Let’s practically do it. For the first time we need to do some proxychains configurations and need to learn basics of it.
Configuring ProxyChains
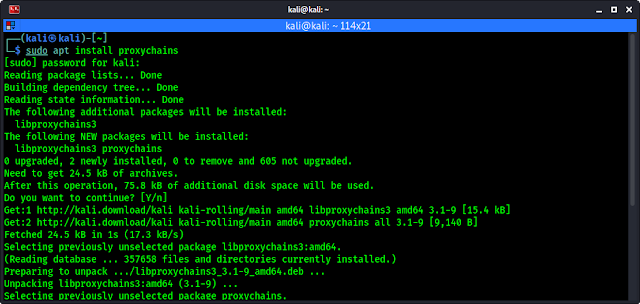
Proxychains comes pre-installed with Kali Linux, also we can install it using following command:
After that we need to configure it as we want to use. Let we open the configuration file by using following command:
The above command will open the proxychains configuration file as we can see in the following screenshot:
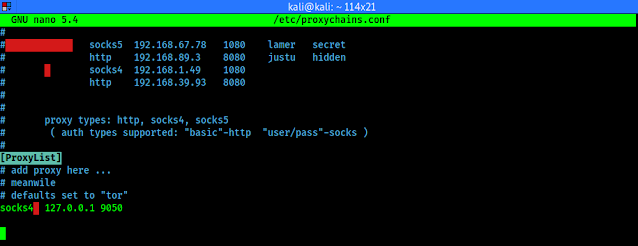
If we scroll down to the end of the file we can see the list of proxies.
We can add our proxy servers here. First is proxy type then IP address then port number. We also can add username and password of the proxy server (If required). Everything is shown in the following screenshot:
 |
| Proxy list explained |
Now we can add proxies list here.
Just not only proxies list we can configure many more things here, like if the proxy server is taking to much time then we can set timeout for them.
 |
| Proxy timeout settings |
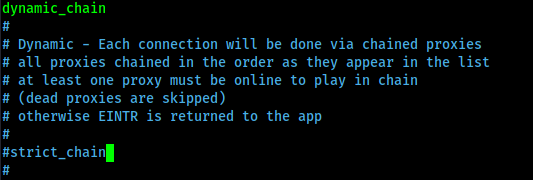
We also can configure various type of chains (proxychains) here, like dynamic chain, random chain, strict chain. The works of the chains is well written here.
But in easy language we can explain them as following. Suppose we have a list of proxies in this configuration file.
- Dynamic Chain:- In this chain our proxy server’s list will maintain the order we have set, but if one or more proxy server is not working it will skip it to get the connection.
- Strict Chain:- In this type of chain our proxy server’s order will maintained and also every proxy server must need to work otherwise it will not make the connection.
- Random Chain:- In this type it will use random proxies from our proxy server’s list. It will not maintain any order.
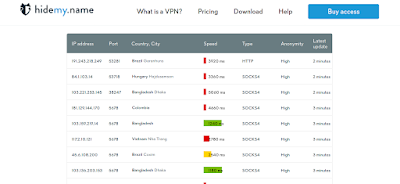
Here we are going to set multiple proxy servers in our proxy list. Where to get free proxies? well there are some websites that provides us free and paid proxies. HidemyName, Genode and Proxy-List etc.We can Google “free proxy server” for more.
We can see the IP address and port of proxy servers, also we can see country/city, speed, type, anonymity etc in the list. We just need the Type, IP and port to add them on our proxychains.conf file. Here we had add two proxies on the configuration file.
Here for example we are going to use dynamic proxy chains. So we remove the ‘#’ before the dynamic chain and put a ‘#’ before the strict chain to disable it. Shown in the following screenshot:
Now we can save and close the proxy chains configuration file by pressing CTRL+X then Y, Then Enter ⤶.
Using Tor with Proxychains
We can install Tor services on our Kali Linux system by using following command:
In the following screenshot we can see that tor is installing on our system:
 |
| Installing Tor on Kali Linux |
After the installation is complete we can start the Tor services by using following command:
Then our Tor services will start, we can check the status of the services by using following command:
Yes, our Tor services is running successfully, we can see it in the following screenshot:
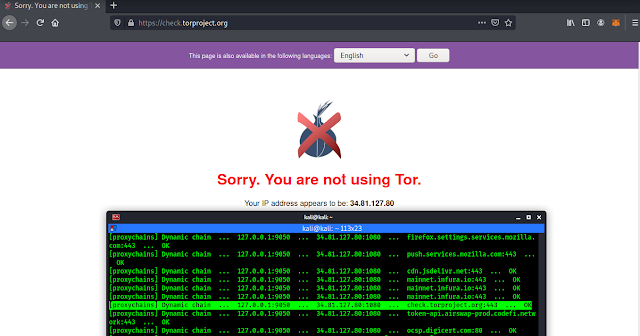
Now we can check this on our browser. We open our browser and navigate to torchecker. In the following screenshot we can see that we are using Tor and it detects it. Now all websites or services on the internet can catch us that we are using Tor network. Here we runs our proxychains.
If we want to run proxychains with our browser we need to type following command on our terminal:
Now our firefox browser will open in front of us. Lets have a look at TorChecker.
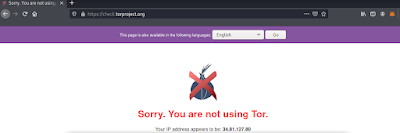 |
| It detects the IP of Proxyservers |
As the above screenshot we can see that it can’t detect us that we are using Tor. But Tor services is running. Then why it can’t detect it? Our connection is going through the Tor nodes to the proxy servers by doing proxy servers didn’t getting our real IP. If they keep logs they can, but our real IP will remain hidden for Tor. We can see it on the following screenshot:
Here we can directly use Tor Tor is good for anonymity but as we told some websites and services didn’t allow Tor network IP’s. Now they can’t detect us and we can do all the things online remain anonymous.
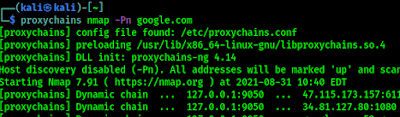
By using this method not only web surfing we can do almost every task. Like by using the following command we can use it for nmap scanning:
Now in the above screenshot we can see that we are scanning using Nmap with the help of Tor and Proxychains.
Things We Should Aware
- We need to remember that after sometimes we need to check if our tor services are running properly by using sudo service tor status command.
- Here we had used dynamic chain for an example but in this dynamic chain if we got any issue with one proxy sever it will skip it. So if we want a better result we need to use strict chain.
- Here for an example we have used only two proxy servers but for better anonymity we need to use as much as proxy server we can. But one thing, increasing amount of proxy servers will decrease the internet speed.
- We need to check if the proxy we got for free is working or not. In real life scenario they mostly found dead. We can use some proxy checker tools to check if they are working or not. It the proxy is not working then we might get “socket error or timeout!” error.
- Proxychains configuration file uses Tor because of it’s default Tor proxychains configuration. We shouldn’t remove Tor’s proxy from here. If we removed Tor’s proxy from here then proxychain will not work with Tor.
 |
| Default proxy for Tor Should not remove |
This is all about smart way to be anonymous in the internet world. Here we had used Tor, but Tor checkers didn’t catch us. Internet will got our Proxy server’s IP and the Proxy server will get our Tor network’s IP. By that way we can browse the Internet anonymously.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.
![How to Stay Anonymous Completely [100% Perfect] How to Stay Anonymous Completely [100% Perfect]](https://infocerts.com/wp-content/uploads/2021/09/How-to-Stay-Anonymous-Completely-100-Perfect-infocerts.jpg)