What is Ngrok ?
Ngrok is a multi-platform application that provides us to forward our local development server to the internet without port forwarding. Ngrok hosts our locally hosted web server in to a subdomain of ngrok.com. That means we can easily show our localhost in the internet without owning domain names/static IP or port forwarding.
Ngrok is a very good tool for the developers to check and show the projects to the clients before launching the project. But as everything it also be misused by the bad guys. They always trying to host their localhost phishing page on Ngrok to capture victims on the internet. So as a cybersecurity expert we need to look up on this Ngrok.
Warning:- Learning is the most beneficial way to protect everyone in the cybersecurity field, so our this article will focus on educational things. Ngrok is like a knife, knife is created for helping people to cut vegetables, but bad guys misuse it. Same for Ngrok also, it is created to help developers but bad guys misuse it. So don’t try to misuse it against anyone. We will not responsible for that.
Download & Configure Ngrok on Kali Linux
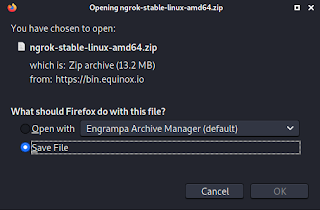
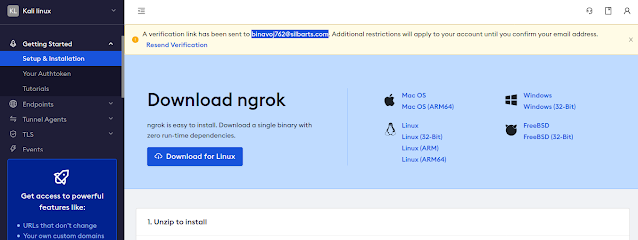
To install Ngrok on our Kali Linux system we need to open our browser and navigate to the official Ngrok’s download page. Then we can see the webpage like the following screenshot:
Here we need to click on “Download for Linux”, because we are using Linux. For other OS we can go on the “More Options”. After clicking on download we can see that download is started.
After download the starting it may not take much time with decent internet. The ZIP file will be downloaded on our “Downloads” directory. We need to go to the “Downloads” directory and decompress the compressed file.
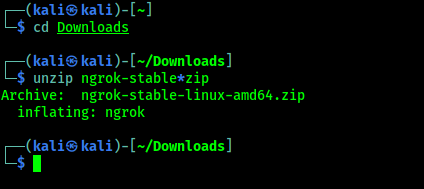
We open the terminal and use following command to go to our “Downloads” directory.
cd Downloads
Then we unzip the downloaded ZIP file by using following command:
unzip ngrok-stable*zip
In the following screenshot we can see that our zip compressed file is extracted.
Now our ngrok file is decompressed. Before running it we need to give it executable permission by using following command:
chmod +x ngrok
Now we are all set to run. But wait, we need to setup Ngrok before running. We need to set authentication with Ngrok API token. Where I can get my token? Well for that we need to sign up on Ngrok website. Lets navigate to Ngrok signup page on our browser.
Here we need to fill up our name and email and choose a password. If we want we can use disposable mail address to login and verify our mail address we don’t need to give our own mail address.
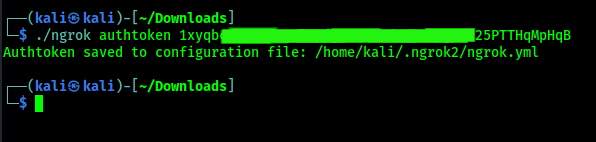
After verifying our mail address we can get the API token on the “Your Authentication” area on the sidebar, as we can see in the following screenshot:
In the above screenshot we can see our Ngrok authentication API key and the command to set it up. For security we had hided a part of our API keys. So we run the command with API key to set up the Ngrok.
./ngrok authtoken 1xyqb*****************25PTTHqMpHqB
In the above command again we hided our the same API key with *. In the following screenshot we can see the output of the command:
Now we are all set to run Ngrok. For an example we forward a locally hosted demo website to the internet.
Using Ngrok on Kali Linux
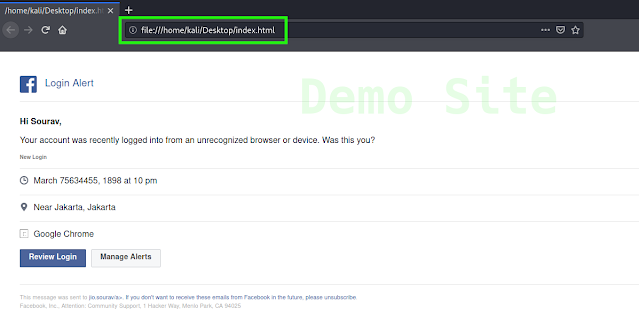
Ngrok’s work is simple it just host our local website to internet. So first we need a local website. Here we have a demo html page on our desktop, and we had opened it on Firefox browser.
But it is just a html page we need to host it locally. For that, we need to run a localhost server on our desktop. We open another terminal and go to the directory where our html page is stored. Then run python localhost server there to host the html page on our localhost by using following command:
sudo python3 -m http.server 80
In the following screenshot we can see that our local web server is started:
Now we can check it by opening our localhost IP on our browser 127.0.0.1. In the following screenshot we can see that page is now accessible by using our local host IP (127.0.0.1).
Now this is accessible from our computer by using localhost IP (127.0.0.1), and from devices on the same network by using our Local IP (IP assigned by router for our Kali Linux system). But it isn’t available for other network, because this web server isn’t hosted on internet.
Now we leave our web host terminal as it is, and back to our previous terminal window (where we setup Ngrok), and run the following command to run Ngrok:
./ngrok http 80
Here we run the Ngrok script on http with port number 80, because our localhost server is running on port 80. (If we can’t use the localhost port 80 then we can use other ports like 8080 or 8888, in that case we need to specify our that port on Ngrok).
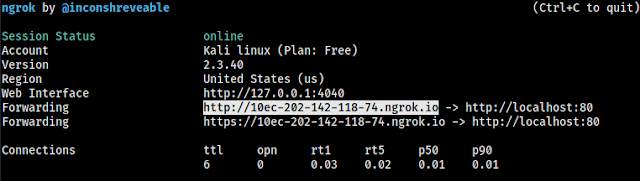
After that we can see our Ngrok is started as we can see in the following screenshot:
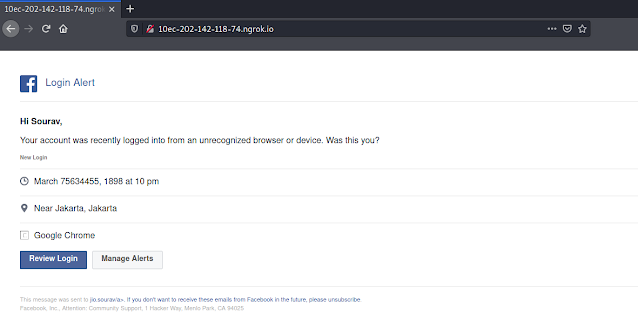
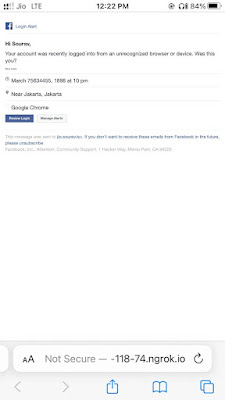
In the above screenshot we can see our forwarding link. Using that forwarding link (in actual links both http and https) we can see our that page from our browser.
Not only from our browser we can access it from anywhere on the internet by the link provided by Ngrok.
We can see that page on our mobile which is connected to mobile data (not in our WiFi network). This link will be active until we don’t close the Ngrok tunnel, but in real life uses Ngrok can’t run this for a long time in their free plan. It can be a temporary solution.
This is how we can use Ngrok on Kali Linux, this is the solution for hosting our local website or web server on the internet. Here we don’t need a static IP address neither requires port forwarding.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.
 EC-Council and Vinca Cyber form an alliance to support businesses and cybersecurity leaders in India by providing optimum managed services solutions, a combination of phishing simulations with ready-to-use training modules and anti-phishing preventive controls that give organizations and individuals the necessary tools to be secure in a virtually connected world. India, October 1, 2021 – As businesses all over the […]
EC-Council and Vinca Cyber form an alliance to support businesses and cybersecurity leaders in India by providing optimum managed services solutions, a combination of phishing simulations with ready-to-use training modules and anti-phishing preventive controls that give organizations and individuals the necessary tools to be secure in a virtually connected world. India, October 1, 2021 – As businesses all over the […]

 EC-Council, a global leader in cybersecurity certifications, appoints Aljhood as an authorized training center in the Middle East. Aljhood is a leading training and consulting company specializing in business, organizational, and operational excellence solutions to support the development of security-aware culture. It offers professionals innovative and practical approaches to cybersecurity training and education, supporting regional workforce development. Middle East, September […]
EC-Council, a global leader in cybersecurity certifications, appoints Aljhood as an authorized training center in the Middle East. Aljhood is a leading training and consulting company specializing in business, organizational, and operational excellence solutions to support the development of security-aware culture. It offers professionals innovative and practical approaches to cybersecurity training and education, supporting regional workforce development. Middle East, September […]
 EC-Council welcomes Constantino, an experienced leader who will drive content strategy by ensuring high standards of excellence and accuracy in digital communications. She brings 15 years of experience in the cybersecurity, education, and literary industries to the newly created role. Tampa, FL (October 15, 2021) Cynthia Constantino, a well-respected editor of cybersecurity courses and programs, joins EC-Council to lead content […]
EC-Council welcomes Constantino, an experienced leader who will drive content strategy by ensuring high standards of excellence and accuracy in digital communications. She brings 15 years of experience in the cybersecurity, education, and literary industries to the newly created role. Tampa, FL (October 15, 2021) Cynthia Constantino, a well-respected editor of cybersecurity courses and programs, joins EC-Council to lead content […]
 Vietnam, October 9, 2021 – EC-Council co-sponsors the awards for the winners of ASEAN Student Contest on Information Security (ASCIS) along with Wissen. The contest is an integral activity of the annual event, “Vietnam Information Security Day” organized by VNISA under the sponsorship of the Ministry of Information and Communications (MIC) and the Ministry of Education and Training (MoET) of Vietnam. ASCIS is a Capture the Flag contest for students from institutes of higher education in ASEAN. The warm-up round of […]
Vietnam, October 9, 2021 – EC-Council co-sponsors the awards for the winners of ASEAN Student Contest on Information Security (ASCIS) along with Wissen. The contest is an integral activity of the annual event, “Vietnam Information Security Day” organized by VNISA under the sponsorship of the Ministry of Information and Communications (MIC) and the Ministry of Education and Training (MoET) of Vietnam. ASCIS is a Capture the Flag contest for students from institutes of higher education in ASEAN. The warm-up round of […]








 September 29th 2021, Kingdom of Saudi Arabia – Security awareness is a significant cause for concern for organizations, and never more so than when users are working remotely. The use of cloud-based collaboration tools to facilitate remote work has increased the amount of sensitive data accessed by end-users. As a result, organizations are more prone to security vulnerabilities and insider […]
September 29th 2021, Kingdom of Saudi Arabia – Security awareness is a significant cause for concern for organizations, and never more so than when users are working remotely. The use of cloud-based collaboration tools to facilitate remote work has increased the amount of sensitive data accessed by end-users. As a result, organizations are more prone to security vulnerabilities and insider […]







 September 27th 2021 EQT Private Equity adds to its cybersecurity investments with a significant equity stake in EC-Council EC-Council contributes to narrowing the global cybersecurity talent gap and confronting the increasingly complex nature of cybersecurity incidents EQT will support EC-Council and its management team in its next phase of growth and innovation by leveraging EQT’s cybersecurity sector expertise, global platform […]
September 27th 2021 EQT Private Equity adds to its cybersecurity investments with a significant equity stake in EC-Council EC-Council contributes to narrowing the global cybersecurity talent gap and confronting the increasingly complex nature of cybersecurity incidents EQT will support EC-Council and its management team in its next phase of growth and innovation by leveraging EQT’s cybersecurity sector expertise, global platform […]