EyeWitness is a tool that is designed for Kali Linux and allows a penetration tester to capture screenshots of a website without leaving the Terminal. It also provide some server header info, and identify default credentials if known.
EyeWitness does all of the work in the background. Imagine having to visually profile multiple websites, open Virtual Network Computing (VNC) servers, and use Remote Desktop Protocols (RDPs). This can be a time-consuming task. EyeWitness takes the screenshots, stores them offline, and generates HTML reports.
EyeWitness comes with Kali Linux repository. We can install it using apt-get install but if we want we also can clone it from GitHub, but here we Kali users download it by using following command:
sudo apt-get install eyewitness
After providing our root superuser password it will start downloading, as we can see in the following screenshot.
Now we can check the help options of this eyewitness tool by using following command:
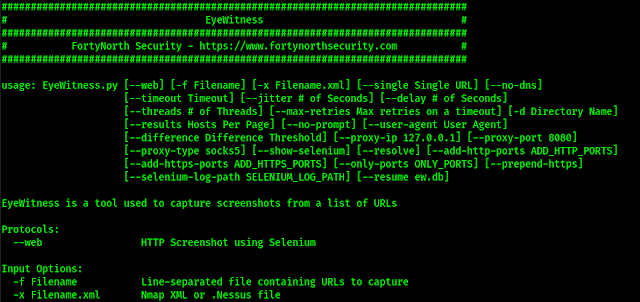
eyewitness -h
Above command will lead us to the help section of eyewitness tool, as shown in the following screenshot:
Let it run against our own website as a single target. So we need to use following command:
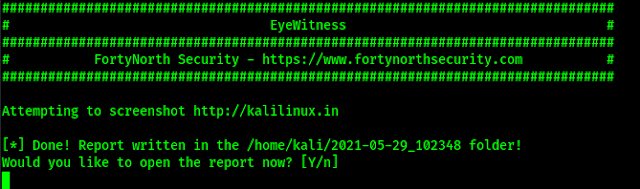
eyewitness --web --timeout 20 --single kalilinux.in
Here we have set –web flag because our target runs on web protocol, we have set the –timeout on 20 seconds (this is optional default is 7 seconds) because we know our website and internet connection both are slow ?. Then we put a –single target.
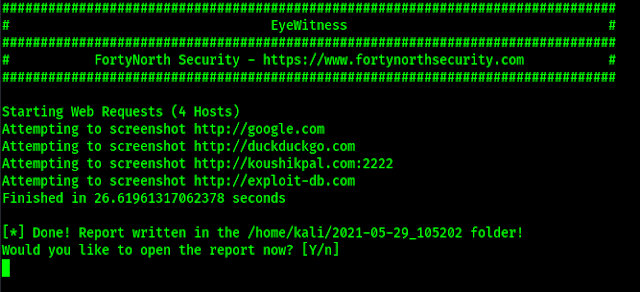
On the following screenshot we can see the output generated by eyewitness.
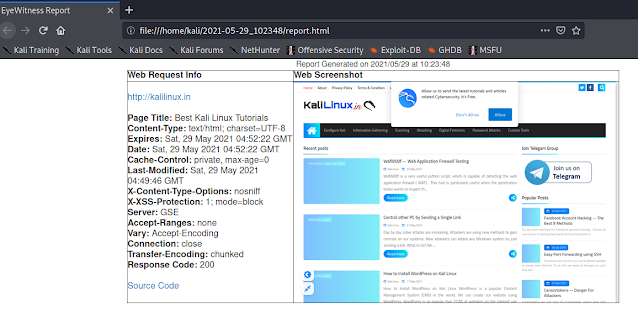
This output is saved on home/kali/2021-5-29_102348 (Path will be different for everyone, but mentioned here) as we can see on the above screenshot. It also prompts for opening the report now. Here we press Y and Enter. Then the HTML report will open in front of us on our default browser, as we can see on the following screenshot:
This is for taking screenshot of a single website without visiting it, the left-hand column contains information about the web request, while the right-hand column contains the screenshots.
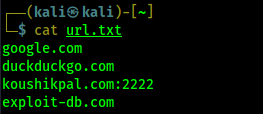
Now If we have to visually profile multiple websites, open Virtual Network Computing (VNC) servers, and use Remote Desktop Protocols (RDPs) then we need to have a list of all URLs. Here we have one list of URLs separated by new line.
Now we use following command to take screenshot of every URLs on the url.txt file by using following command:
eyewitness -f url.txt --web
Here -f flag used to import targets from a file. If we want to import target from Nmap XML or .Nessus file then we need to use -x flag in the place of -f flag. The output is showing on the following screenshot:
After opening the report we can see is on our browser.
This tool is very handy when profiling multiple services and websites at once. Now that we have completed this article, and we are able to perform web enumeration using the EyeWitness tool on our Kali Linux system.
Love our articles? Make sure to follow us to get all our articles directly on inbox. We are also available on Twitter and GitHub, we post article updates there. To join our family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.