SubFinder — Discover Hidden Sub-Domains
During web penetration testing we need to collect a lot of information related to our target website/webapp. There are lot of things to to in our some previous articles we mention them. Sub-domain finding is one of them. There are many subdomains may contains some valuable/juicy information for us.
In our some previous articles we already discussed about some subdomain discovery tools, but in this article are going to use an faster sub-domain finder tool named SubFinder. SubFinder is a subdomain discovery tool that discovers valid subdomains for websites by using passive online sources. It has a simple modular architecture and is optimized for speed. SubFinder is built for doing one thing only – passive subdomain enumeration, and it does that very well.
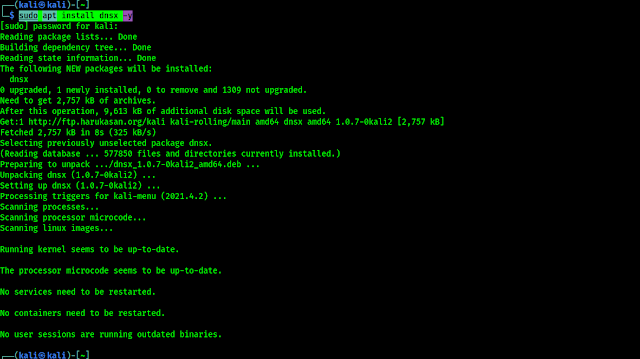
SubFinder is written in Go Language and comes with Kali Linux repository. We can easily install it by using following command:
The above command may prompt for sudo password, after providing our sudo password it will start downloading SubFinder. The tool is not large can be installed in some seconds with a decent internet connection, as we can see in the following screenshot:
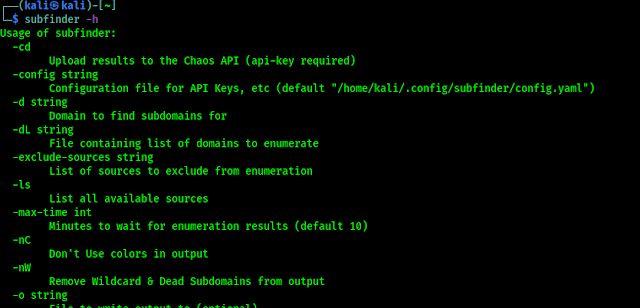
In the above screenshot we can see our required tool SubFinder is installed successfully. Let we check it’s helps by simply using following command:
In the following screenshot we can see the help options of SubFinder.
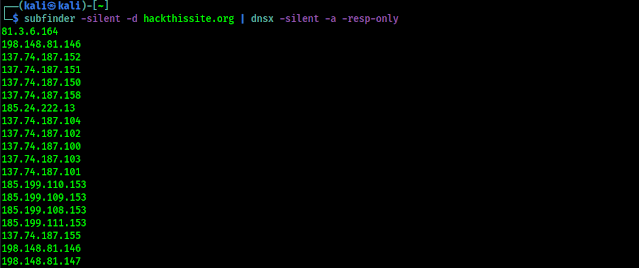
We can start discovering subdomains of our target website by using SubFinder. For an example we are going to check the subdomains of hackerone.com, so we will use the following command:
In the following screenshot we can see that SubFinder is collecting subdomains of hackerone.com.
There are lots of options in the SubFinder tool, as we have seen on the help option. To save the output on a file we can use -o flag.
The above command will save our list of discovered subdomains on our mentioned file, as we can see in the following screenshot:
We can also use –all flag to use all sources, but it will be slow for enumeration.
This is very helpful for cybersecurity researchers because sometimes the website developers just not show the older and not using subdomains, as we know older things have a good chance to be vulnerable.
This is how we can discover hidden subdomains of a website using SubFinder on our Kali Linux system.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.