December 14, 2021
In our recent articles we learned how we can find subdomains and what is subdomain takeover vulnerability. In our this article we are going to learn how we can find potential subdomain takeover vulnerability. Subdomain takeover vulnerability is a very serious issue in cybersecurity and may lead to a good bounty to bug bounty hunters.
In today’s article we are going to discuss about an automated tool which will help us to discover potential subdomain that we can takeover. The tool is named Sub404. Sub404 is a tool created with Python3 and it is very fast as it is asynchronous.
After information gathering, during recon process we may found a lot of subdomains(for an example more than 10k ?). It is not possible to test each manually or with traditional requests or urllib method, because it is very slow. Using Sub 404 we can automate this task in much faster way. Sub 404 uses aiohttp/asyncio which makes this tool asynchronous and faster.
How Sub404 Works?
Sub404 uses subdomains list from text file (check our this article) and checks for URL of 404 Not Found status code and in addition it fetches CNAME (Canonical name) and removes those URL which have target domain name in CNAME. It also combines result from SubFinder and Sublist3r (subdomain discovery tool). If we don’t have target subdomains as two is better than one. But for this sublist3r and SubFinder tools must be installed in your system. Sub404 is very fast as we told, the creator of this tool claims that it is able to check 7K subdomains in less than 5 minutes.
Key Features of Sub404
- Fast (as it is asynchronous).
- Uses two more tools to increase efficiency.
- Saves result in a text file for future reference.
Install & Use Sub404 on Kali Linux
To install Sub404 on our Kali Linux system we need to clone it from it’s GitHub repository by using following command:
After applying the above command Sub404 will be downloaded on our current working directory. As we can see in the following screenshot:
Now we need to install two other tool on our Kali Linux system, because as we said Sub404 didn’t like to work alone. It requires two more subdomain discovery tools with it to increase efficiency. They are SubFinder and Sublist3r. In our recent article we talked about SubFinder. Anyways, we need to install both of these tools by simply using following command:
In the following screenshot we can see that both tools are successfully installed on our system.
Now we need to navigate inside the sub404 directory which we cloned by using following command:
Now we need to install requirements for Sub404 by applying following command:
The following screenshot shows the output of the above command:
Now we are ready to run. In our this (sub404) directory we got a python script named sub404.py, we need to use this script to run this tool. Let we check the help options for Sub404 by applying following command:
In the following screenshot we can see the help options of Sub404:
We can directly provide Sub404 a domain to scan all the subdomains then check for subdomain takeover vulnerabilities on those subdomains automatically by using -d flag. Or we can provide Sub404 a list of subdomains (in txt format) to analyze them for subdomain takeover vulnerabilities by using -f flag. By using -p flag we can specify the protocol (HTTP or HTTPS), the default protocol s HTTPS.
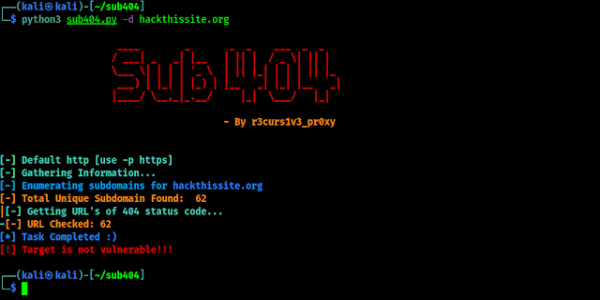
Lets run it against a live website (everyone have the permission to hack this site) i.e hackthissite.org. To test on a domain we need to use following command:
Then Sub404 will start scanning on it and find the subdomains then check for 404 status. Then check the CNAME of 404 subdomains. Is they are pointing to any 3rd party services. Then show us the results as we can see in the following screenshot:
As we can see in the screenshot that our target isn’t vulnerable. That’s fine. This was our example target.
Now if we already have a list of subdomains (as we did in our SubFinder article), we can check on them also by applying following command:
In the following screenshot we can see the output of the above command:
Seems we got no luck, this is also not vulnerable ??.
This is how we can check for subdomain takeover vulnerability on any website. But before that:
Waring: This tutorial is for educational and research purposes only. Hacking a subdomain without proper permission is a serious crime. If anyone does any illegal activity then we are not responsible for that.
That is all for today. Today we learnt how we can find subdomain takeover vulnerability very easily using Sub404 tool on our Kali Linux system. Also we learnt to not harm anyone using our super powers, “With great power comes great responsibility“.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.
Article posted by: https://www.kalilinux.in/2021/10/sub404-easily-find-sub-domain-takeover-vulnerability.html
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com
This is the article generated by feed coming from KaliLinux.in and Infocerts is only displaying the content.