March 7, 2024
What Is Network Security?
Network security covers many technologies, devices, and processes. It refers to a set of rules and configurations designed to protect the integrity, confidentiality, and accessibility of computer networks and data.
Sound network security controls are recommended for organizations to reduce the risk of an attack or data breach. These measures also enable the safe operation of IT systems. Network security consists of hardware and software technologies and are ideally composed of layers that include applications, antivirus, access management, servers, firewalls, physical access, and policies.
Forcepoint
Why Is Network Security Important?
Read More
What are Network Threats?
Types of Network Security Attacks
Network security attacks are categorized on the basis of the end goals and are known as active and passive.
Passive: The purpose here is to monitor/screen sensitive information. Here, the security of enterprises and their customers is compromised. Examples of passive threats:
-
Release of message content
-
Traffic analysis
-
Masquerade
-
Replay
-
Modification of message content
-
Denial of Service

Read More
Network Security Vulnerability
Different Types of Vulnerabilities
-
Missing data encryption -
Old command injection -
SQL injection -
Missing authentication for critical function -
Missing authorization -
Unrestricted upload of dangerous file types -
Reliance on untrusted inputs in a security decision -
Weak password -
Cross-site scripting and forgery -
Download of codes without integrity checks -
Use of broken algorithms -
URL redirection to untrusted sites -
Path traversal -
Bugs
How Enterprises Achieve Network Security
Network Security Policy
Some of the benefits of a well-structured network security policy are:
-
Blueprint for security implementations. -
Budget any security components that need to be purchased. -
Defines the technologies to be used and the ones that cannot be used. -
Defines clear access to the network with passwords and credential levels. -
Creates a legal framework.
An effective network security policy also defines certain tools that offer better protection. These tools are known as network security controls.
What Are Network Security Controls?
How Do You Implement Security Controls?
Network Protocols
Components of network protocols:
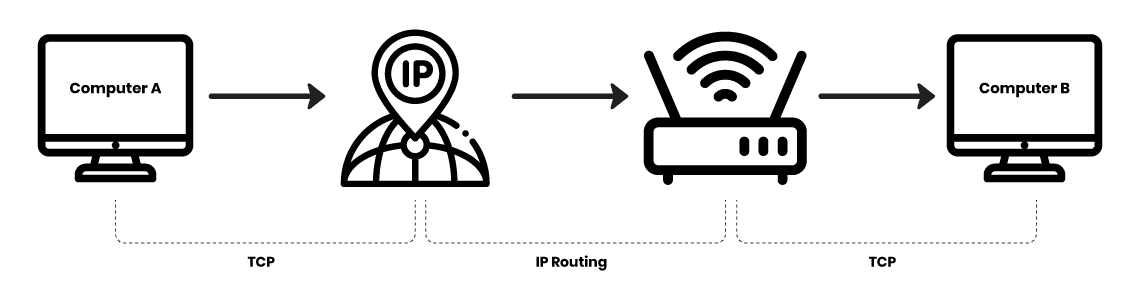
Internet Protocol (IP): It is the address system of the internet with the core function of delivering information packets. IP is a primary key to network connections.
Transmission Control Protocol (TCP): TCP works with IP for exchanging data packets. TCP organizes data to ensure secure transmission between the client and the server.
Wireless Network Protocols: These protocols work on wireless networks, e.g., Wi-Fi, Bluetooth, and LTE. It proves useful for mobile and electronic devices that are not directly connected with a wire.
Wireless Network Protocols: These protocols work on wireless networks, e.g., Wi-Fi, Bluetooth, and LTE. It proves useful for mobile and electronic devices that are not directly connected with a wire.
Network Firewalls
A firewall refers to a hardware or a software program designed to enhance network security. Its purpose is to block all unwanted incoming traffic while allowing authorized communications to flow freely.
A traditional network security firewall can only protect the internal network against incoming traffic. Despite this, firewalls have played an important role for the last three decades. Modern firewalls are modified as NGFW and target focused NGFW to block emerging cyber threats.
Types of Firewalls
Proxy firewall: A proxy firewall protects a private network’s resources by filtering out flagged messages at the application layer.
Stateful inspection firewall: This type of firewall blocks incoming traffic based on state, port, and protocol.
Next-generation firewall (NGFW): Next-generation firewalls can block modern-day cyber threats, such as advanced malware and application-layer attacks.
Unified threat management (UTM) firewall: UTM firewalls offers a single security solution that provides multiple security functions.
Threat-focused NGFW: Threat-focused NGFWs offers advanced threat detection and remediation.
Network Traffic Monitoring
Network security is monitored to ensure the safety of the internal systems and the data that is generated during the process. This data is helpful in various IT operations and case studies.
Network traffic monitoring tools are broadly classified into two types. There are deep packet inspection tools and flow-based tools. These tools are gaining popularity in the cybersecurity community as companies are relying on mechanics like cloud and VOIP. Network monitoring software are helpful in monitoring network traffic whenever the stress on the network increases.
Analyzing Network Traffic
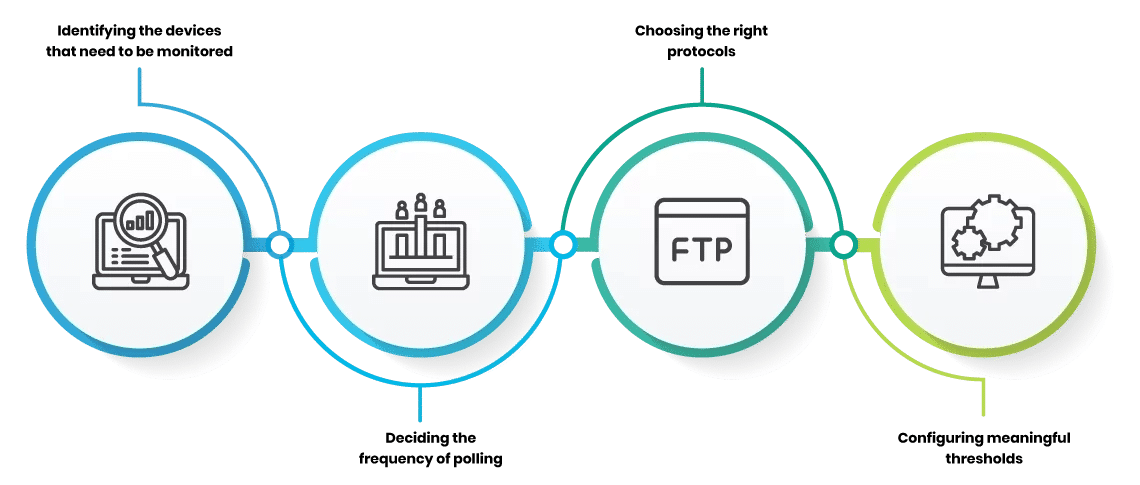
-
Monitoring internal network visibility. -
Learning departmental bandwidth usage. -
Learning departmental bandwidth usage. -
Detecting spyware and other hacks. -
Identifying the performance of slow applications. -
Observing the flow of personal information to outsiders.
Network Security Techniques
No network is safe in an environment where hackers continuously find ways to exploit the system. A threat can cause problems at any moment. A foolproof network security system will ensure these problems won’t occur.
Here are some of the must-have network security tools that help you protect your internal systems from intrusions.

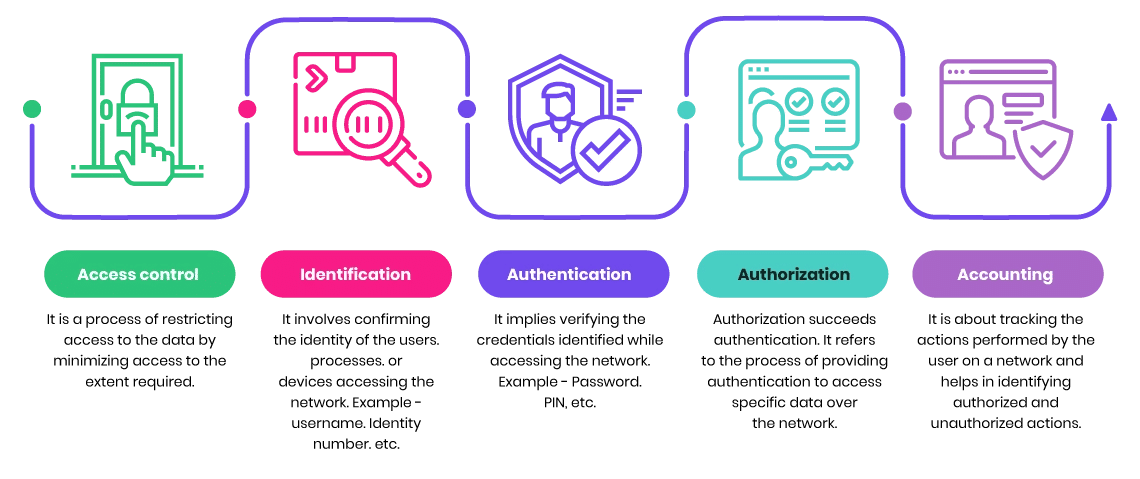
Access Control

Anti-Malware
Anti-malware is one of the security essentials that identifies viruses, worms, Trojans, etc., and prevents them from infecting the network.

Behavioral Analytics
Security personnel establish guidelines for what is considered as normal behavior for customers as well as users. Behavioral analytics software keeps an eye on any suspected activity to identify abnormal behavior.

Application Security
Application security helps establish security guidelines for applications that are relevant to network security. This process blocks any suspicious application from entering the system as well as for closing gaps in security coverage.

Data Loss Prevention
Humans are considered the weakest security link. Data loss prevention (DLP) technologies protect staff and anyone who uses the network from misusing and possibly compromising sensitive data.

Firewalls
Firewalls are an important part of the network security system as they act as a barrier between the network trusted zone and everything beyond it.

Email Security
Phishing allows intruders to access an insecure network illegally. Email security blocks phishing attempts and outbound messages carrying sensitive data.

Mobile and Wireless Security
Mobile and wireless devices are vulnerable to possible network breaches and therefore require extra scrutiny.

Intrusion Detection and Prevention
Intrusion detection and prevention systems AKA intrusion detection system analyze network traffic/packets to identify different types of attacks and respond quickly. Intrusion detection systems create a database of known attack methods to identify patterns and thwart any similar incidents in the future.

Security Information and Event Management (SIEM)
SIEM collects data from various network tools. This information helps in identifying and responding to threats accordingly.

VPN
A virtual private network authenticates safer communication between a network and a device.
Network Security in Cloud Computing
Due to huge data exchanges, businesses are transferring from internal networks to a bigger and secure platform. The cloud infrastructure is a self-contained network in both physical and virtual mediums. Physical infrastructure refers to multiple cloud servers working together. Virtual stands for instances of clouds networking with each other on a single physical server.
Cloud security offers many benefits, including:
Centralized security: Cloud security centralizes protection and makes it easier to deal with BYOD, IoT, or Shadow IT. Disaster recovery plans can also be implemented quickly when the need arises
Reduced costs: The cost of cloud security is cheaper than many traditional network security With cloud, the task of multiple departments spending long hours searching for security risks can be avoided.
Reliability: With the right security solutions in place, users can safely access data within cloud irrespective of location or device.
Ideal for Internet of Things: Cloud security proves extra useful for IoT devices as they need a lot of storage space to share information. Cloud storage offers that storage space with the guarantee of safety and security. IoT devices produce huge amounts of data that stays safe and secure on a cloud storage platform.
Cloud vendors create security control policies on their platforms which often don’t match the internal policies of their client. This results in excess load and mismatches due to multiple security policies. In such cases, a certified network defender would come up with viable solutions to resolve these complexities.
Applications of Network Security
Network Security in Healthcare
Network Security in Law Firms
Law firms have a lot of information to protect. A network breach will not only damage the reputation of the said entity but will also expose their clients to blackmailing and identity theft. Since the beginning of 2020, many law firms have started online consultations, increasing these risks. Impenetrable network security measures will establish a better business-client relationship with a higher degree of privacy and confidentiality.
Network Security in Media
Network security measures are always recommended for film, music, and the publishing industry. Proper defensive measures in place will reduce the risk of theft of intellectual property and massive damages.
Network Security in Food and Hospitality
The food and hospitality industries handle sensitive private information including bank account and credit card details. These companies should have a proper network defense infrastructure to keep the information private and ensure a higher level of trust.
Any entity that holds confidential information like personal records, card details, and even CCTV footage should consider implementing network security solutions.
Network Security in BFSI
The BFSI sector is fueled by fast-paced technology adoptions leveraging AI, blockchain, cloud computing, etc. These innovations, integrated with a massive growth in fintech, are spearheading the rise of the cashless economy around the world.
This switch to a cashless mindset and popularity of payments through apps, cards, and other similar mediums, has resulted in the sector becoming a target for cyber criminals. Vizom, the malware that used remote overlay attacks to strike Brazilian bank account holders, is a cautionary tale. The BFSI sector needs to improve its network security infrastructure to protect customer data, credit and debit card information, and confidential information that can cause a lot of damage if leaked.
Protect, Detect, Respond, and Predict Approach
Network security is not a destination but a journey. It is a process that strengthens the internal systems with the help of various strategies and activities. These can be grouped into four phases — protect, detect, respond, and predict. Every phase of network security control requires strategies that move the process to the next phase. Any modification in one phase affects the overall process. An experienced network security official would take a proactive approach in the prevention phase to enable the other three approaches to be successful.

What Is a Blue Team in Cybersecurity?
A Blue Team is a team of defenders that keep an eye on any possible attack on the network. Organizations hire individuals who have a deep understanding of and training in network defense to stay safe from any attacks. Network administrators who aspire to progress further in their career choose blue team cybersecurity certifications for better opportunities in their career. There are multiple certifications depending on their skill sets and understanding of tools and techniques.
Network Security Jobs
There is a clear gap between demand for network security professionals and the vacancies, where the latter is way higher. According to LinkedIn, more than 50,000+ network security jobs are lying vacant because of lack of talent and expertise. A network security certification will open unlimited opportunities to pursue these jobs in the most reputed companies around the world.
Network Security Engineer Salary
According to PayScale, network security engineers earn between $57,000 and $128,000 on a yearly basis.

Are You a CCNA Administrator Looking to Upgrade?
The CCNA certification authenticates the ability to install, configure, operate, and troubleshoot routed & switched systems, and typically leads to Network Technician/Administrator jobs. The primary responsibility across these roles is to handle the networking equipment crucial for seamless data flow within the IT infrastructure.
The certification has its limits though, as it doesn’t provide knowledge of network defense or security. CND v2 focuses on key knowledge areas to develop superior network defense skills. A Network Administrator who understands networking tools and technologies will absorb knowledge about network security faster than their peers.
A Network Technician/Administrator with network security training will find careers in the most reputed organizations around the world.
Are You a MCSE Administrator Looking to Upgrade?
MCSE certified technicians have knowledge of networking fundamentals and experience in configuring tasks related to administration and security. Their responsibilities include installing, configuring, testing, and maintaining operating systems, system management tools, and application software for clients. They monitor the security, backup, and sluggish approaches of clients.
However, this certification has its limits as it doesn’t cover network security. Professionals in this domain should consider network defense to reach the next stage of their career. A Network Administrator with prior understanding of networking tools and technologies will absorb knowledge about network security faster than their peers.
Technicians with network security training go on to find careers in sought-after companies around the world. CND v2 is a vendor-neutral certification that allows individuals to work on different tools without any restrictions. Those who complete EC-Council’s Certified Network Defense (CND) training and certification qualify for job roles such as entry-level Network Administrators, entry-level Network Security Administrators, Data Security Analyst, Junior Network Security Engineer, Junior Network Defense Technician, Security Analyst, Security Operator, among many others.
EC-Council’s Network Security Training Program
Network security opens new career paths. When it comes to pursuing a thoroughly designed network security program, EC-Council is a preferred name among professionals as well as employers. The programs offer a vendor-neutral experience of threats that a professional may face on the job.
Network security training is for everyone and is not just limited to IT professionals. Students have the freedom to choose the best program according to their knowledge base, ranging between basic, intermediate, and advanced.
Network Security Learning Path
Basic
Linux: Understanding Linux is important to understand the operating system that powers much of the internet. The Basic Linux learning program teaches Linux fundamentals, Ubuntu Server, configuring remote access with Secure Shell (SSH), remote access overview, managing and securing a server, creating a web server with Ngnix, and securing Ngnix.
Intermediate
Linux Server Administration: Linux Server Administration is for students who have a basic understanding of Linux and want to learn further. The program teaches the basic skills of installing and configuring Linux Fedora Workstation and Server.
Identity and Access Management: Identity and Access Management is designed to get acquainted with IAM standards like ISO 27001 and NIST. The program teaches IAM governance and how to implement IAM architecture solutions.
Advanced
Network Defense
Network Defense is the way to go for professionals who have a thorough understanding of Linux Administration and IAM. Under the Network Defense umbrella, you’ll find the following courses ideal to expand your knowledge base:
Certified Network Defender (CND v2): Certified Network Defender (CND v2) focuses on developing network defense skills among network administrators. This skill-based, 50% lab-intensive network security program takes students through the depths of network security tools and techniques.
Identity and Access Management: Identity and Access Management is designed to get acquainted with IAM standards like ISO 27001 and NIST. The program teaches IAM governance and how to implement IAM architecture solutions.
Other benefits of the program include:
-
Mapped to NICE 2.0 Framework -
Accredited by ANSI, NICF, GCHQ, DoD etc. -
Comprehensive Learning -
Exam Based on Practical Challenges
CND v2 is a network security program that focuses on the protect, detect, respond, and predict approach to security. Beginners with limited knowledge can also consider Network Security Fundamentals (NSF) before diving into the important aspects of the Certified Network Defender program.
The answer depends on your expertise and understanding of the techniques. If you are a working professional, then certification training is a better option because of its short duration. Students or anyone who has the time to invest should always consider a dedicated program with a duration of a year or more. For them, a degree in cybersecurity specializing in network security will be more fruitful.
CND v2 is a good option for online courses for anyone who wishes to pursue network security courses online. The program has the facilities of online self-paced and online live instructor-led training options with live proctored exams.
Network programs touch upon topics like network fundamentals, network access, IP connectivity, IP services, security fundamentals, automation, and programmability. From here, one can go on to learn how to secure or defend the network from attacks and threats with the protect, detect, respond and predict approach given in the Certified Network Defender v2 program.
The certification is proof of your credibility upon which your employer will consider hiring you. For example, if you are applying for networking or a network security job, the employer would want to know if you have network certification or knowledge of network security + certification. A certification will increase your chances of landing a job with ease.
Many share their interview experiences in different cybersecurity communities. Additionally, you can also refer to the free learning resources by EC-Council.
With EC-Council’s network security program, you’ll have the freedom to choose the level from where you wish to start learning. For someone with very little cyber knowledge, the program starts with Linux and climbs upwards as you gain more experience.
Network security is a process that is designed to protect the integrity of a device from external attacks. Network security involves both hardware and software technologies that come together to protect their organization from malicious actors.
Network security tools can be both hardware and software- based. These tools come together to form a protective layer with the sole purpose of protecting confidential data, customer info, bank details and other valuable information.
The post What is Network Security appeared first on Cybersecurity Exchange.
Article posted by: https://www.eccouncil.org/cybersecurity-exchange/network-security/what-is-network-security/
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com
This is the article generated by feed coming from KaliLinux.in and Infocerts is only displaying the content.

