What is Risk Assessment?
- NIST SP 800-30
Risk Assessment is the analysis of threats in conjunction with vulnerabilities and existing controls.
- OCTAVE
A risk Assessment will provide information needed to make risk management decision regarding the degree of security remediation.
- ISO 27005
Risk Assessment = Identification, Estimation and Evaluation
Why Risk Assessment?
Regulatory Compliance
| Compliance Standard | Risk Assessment Requirement |
| PCI DSS Requirement 12 1 2 | Formal and structured risk assessment based on methodologies like ISO 27005, NIST SP 800‐30, OCTAVE, etc |
| HIPAA Section 164.308(a)(1) | Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected protected health information information held by the covered covered entity. |
| FISMA 3544 | Periodic testing and evaluation of the effectiveness of information security policies, procedures, and practices, to be performed at least annually. |
| ISO 27001 Clause 4.1 | Risk assessments should identify risks against risk acceptance criteria and organizational objectives. Risk assessments should also be performed periodically to address changes in the security requirements and in the risk situation. |
| GLBA, SOX, FISMA, Data Protection Act, IT Act Amendment 2008, Privacy Act, HITRUST…… |
Why Risk Assessment?
Business Rationale
| Function | Explanation |
| Return on Investment | Structured RA Methodology follows a systematic and pre‐defined approach, minimizes the scope of human error, and emphasizes process process driven, rather than human driven activities activities. |
| Budget Allocation | Assists in controls cost planning and justification |
| Controls | Cost and effort optimization by optimizing controls selection and implementation |
| Efficient utilization of resources | Resource optimization by appropriate delegation of actions related to utilization of controls implementation resources controls implementation. |
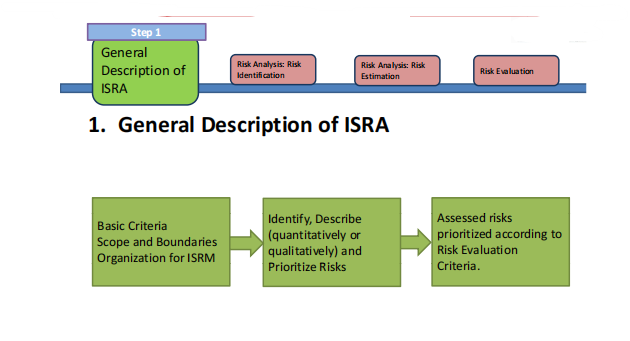
What is IS-RA?
Risk assessment is the cornerstone of any information security program, and it is the fastest way to gain a complete understanding of an organization’s security profile profile – its strengths strengths and weaknesses weaknesses, its vulnerabilities vulnerabilities and exposures.

…YOU CAN’T MANAGE IT!”
Reality Check
• ISRA– a need more than a want
• Each organization organization has their own ISRA
• ISRA learning curve
• Cumbersome – 1000 assets, 20 worksheets
• Two months efforts
• Complicated report
Exercise
• Threat Scenarios
• Threat Profiles Profiles to be filled. filled.
Risk Assessment reference points
• OCTAVE
• NIST SP 800‐30
• ISO 27005
• COSO
• Risk IT
• ISO 31000
• AS/NZS 4360
• FRAP
• FTA
• MEHARI
ISO 27005 Introduction
ISO 27005 is an Information Security Risks Management guide line.
• Lays emphasis on the ISMS concept of ISO 27001: 2005.
• Drafted and published by the International Organization for Standardization Standardization (ISO) and the International International Electrotechnical Electrotechnical Commission (IEC)
• Provides Provides a RA guideline guideline and does not recommend recommend any RA methodologies.
• Applicable to organizations of all types.
ISO 27005 Workflow
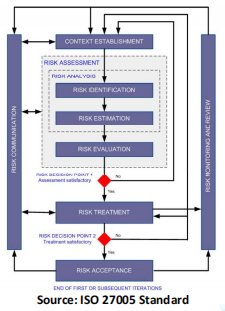
• Advocates an iterative approach
to risk assessment
• Aims at balancing balancing time and
effort with controls efficiency in
mitigating high risks
• Proposes the Plan‐Do‐Check‐Act
cycle.
ISO 27005 Risk Assessment Assessment
Information Security Risk Assessment = Risk Analysis + Risk Evaluation
Risk Analysis:
Risk Analysis = Risk Identification + Risk Estimation
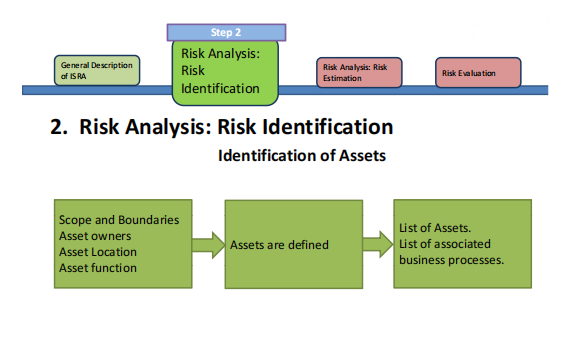
- Risk Identification
Risk characterized characterized in terms of organizational organizational conditions conditions
• Identification of Assets: Assets within the defined scope
• Identification of Threats: Based on Incident Reviewing, Asset Owners, Asset Users, External threats, etc.
ISO 27005 Risk Assessment Assessment Contd.
- Identification of Existing Controls: Also check if the controls controls are working working correctly.
- Identification of Vulnerabilities: Vulnerabilities are shortlisted in organizational processes, IT, personnel, etc.
- Identification of Consequences: The impact of loss of CIA of assets.
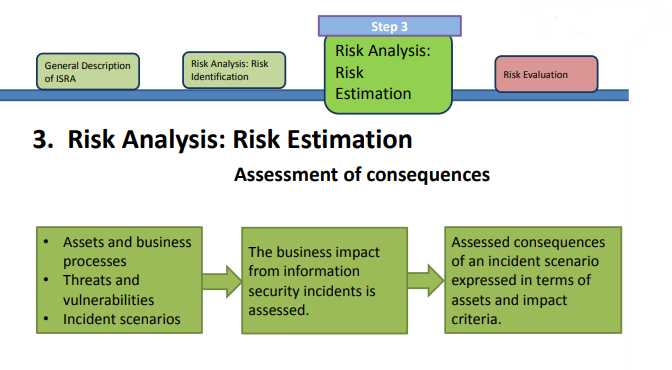
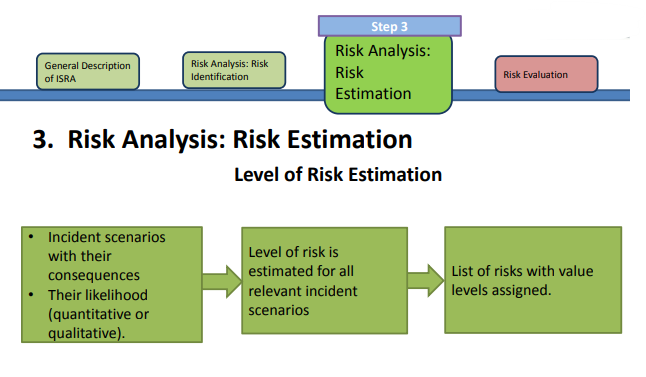
Risk Estimation
– Specifies the measure of risk.
• Qualitative Estimation
• Quantitative Estimation
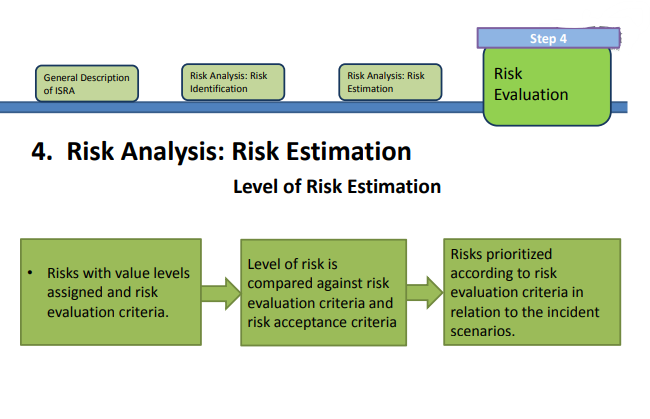
Risk Evaluation:
• Compares and prioritizes Risk Level based on Risk Evaluation Criteria and Risk Acceptance Criteria.
ISO 27005 RA Workflow
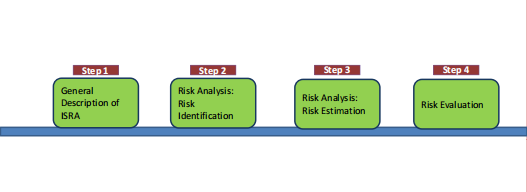
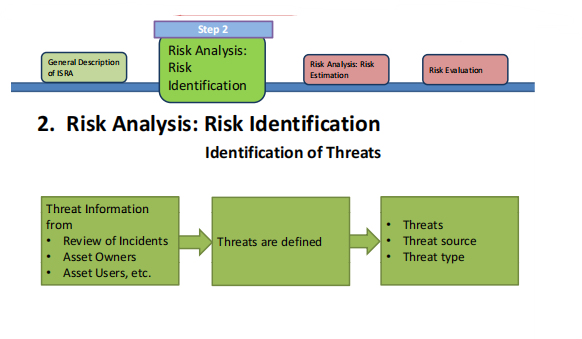
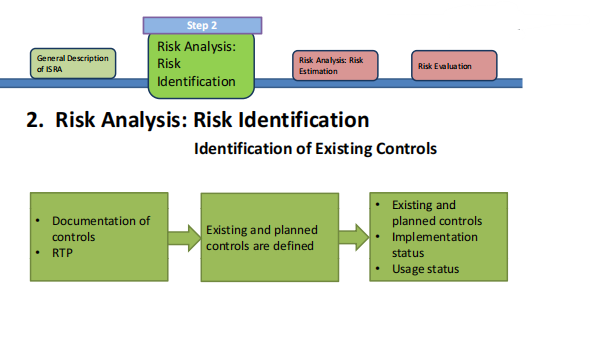
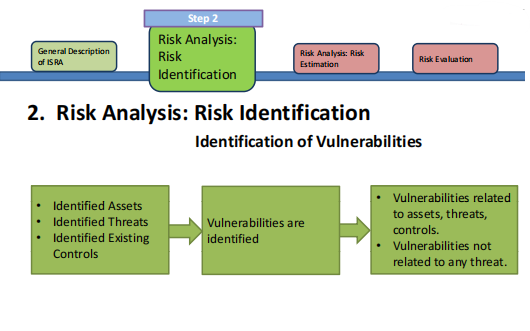
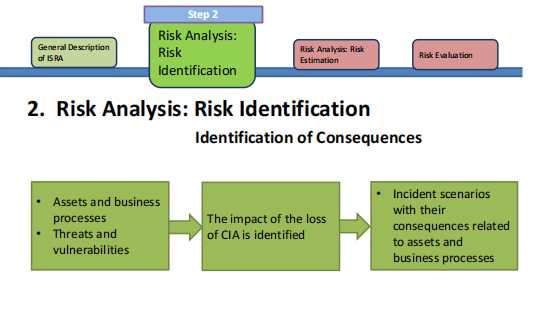
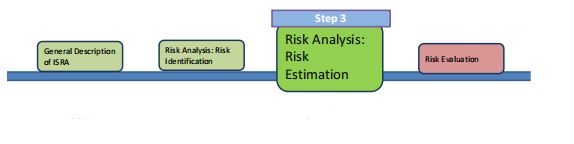
- Risk Analysis: Risk Estimation
Risk Estimation Methodologies
(a) Qualitative Estimation : High, Medium, Low
(b) Quantitative Estimation : $,hours, etc.
Summary
• Keep it Simple and Systematic
• Comprehensive
• Risk sensitive culture in the organization.
• Drive security from a risk management perspective, rather only a compliance perspective.
• Help RA to help you……
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com

