August 25, 2021
Ping Pong! No we are not in wrong article. In this article we are going do discuss about the ping tool. Ping is the most famous tool that is used to check whether a particular host is available or not. tool works by sending an Internet Control Message Protocol (ICMP) echo request packet to the target host. If the target host is available and the firewall is not blocking the ICMP echo request packet, it will reply with the ICMP echo reply packet.
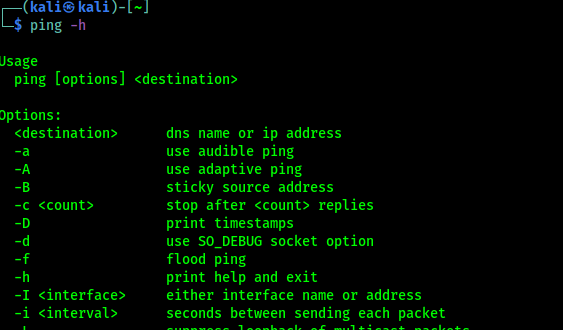
Although we can’t find the ping tool in Kali Linux application menu but in our terminal we can ping -h command to see the help section of the ping tool.
In the following screenshot we can see the help of ping.
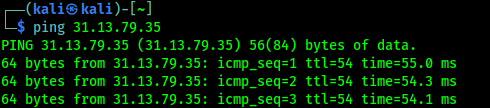
Now we run the ping with a destination address. For an example we use IP address of Facebook. We use following command:
In the following screenshot we can see the output of the above command.
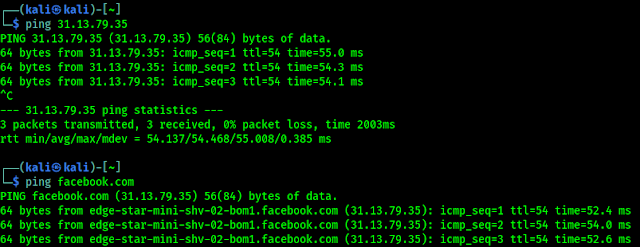
By default, ping will run continuously until we press Ctrl + C and stop it.
We also can use a domain name to ping. Ping will automatically fetch the IP, if the target not behind a firewall.
In the following screenshot we can see that ping is started and it’s automatically find facebook’s IP address.
This was the basic example, ping toll has lot of options inside it, but few of them are widely used. Those are following:
- -c count: This is the number of echo request packets to be sent.
- -I interface address: This is the network interface of the source address. The argument may be a numeric IP address (such as 192.168.0.108) or the name of the device (like eth0, wlan0). This option is required if we want to ping the IPv6 link-local address.
- -s packet size: This specifies the number of data bytes to be sent. The default is 56 bytes, which translates into 64 ICMP data bytes when combined with the 8 bytes of the ICMP header data.
We will discuss about these with example.
Assume that we are starting with internal penetration testing work. The customer gave us access to their network using a LAN cable. And, they also gave us the list of target servers’ IP addresses.
The first thing we would want to do before launching a full penetration testing arsenal is to check whether these servers are accessible from our machine. We can use ping for this task.
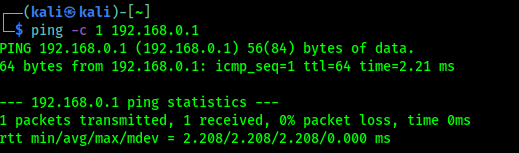
Our target server is located at 192.168.0.1, while our machine has an IP address of 192.168.0.108. To check the target server availability, we can give the following command:
In the following screenshot is the result of the preceding ping command:
From the above screenshot, we know that there is one ICMP echo request packet sent to the destination (IP address: 192.168.0.1). Also, the sending host (IP address: 192.168.0.108) received one ICMP echo reply packet. The round-trip time required is 2.208 ms (millisecond), and there is no packet loss during the process.
Let’s see the network packets that are transmitted and received by our machine. We are going to use Wireshark, a network protocol analyzer, on our machine to capture these packets, as shown in the following screenshot:
From the above screenshot, we can see that our host (192.168.0.1) sent one ICMP echo request packet to the destination host (192.168.0.108). Since the destination is alive and allows the ICMP echo request packet, it will send the ICMP echo reply packet back to our machine.
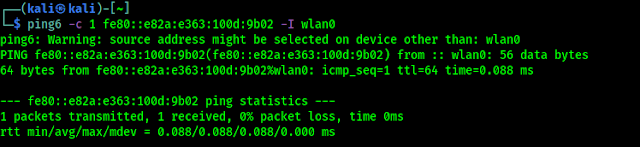
If our target is using an IPv6 address, such as fe80::e82a:e363:100d:9b02, we can use the ping6 tool to check its availability. We need to give the -I option for the command to work against the link-local address:
The following screenshot shows the packets sent to complete the ping6 request:
Here ping6 is using the ICMPv6 request and reply.
To block the ping request, our firewall can be configured to only allow the ICMP echo request packet from a specific host and drop the packets sent from other hosts. This is how we can use ping and know things about our host. This is the primary thing for penetration testers.
That’s for today. Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.
Article posted by: https://www.kalilinux.in/2021/08/ping.html
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com
This is the article generated by feed coming from KaliLinux.in and Infocerts is only displaying the content.