10 Cyber Security Tools to Watch Out for in 2021

With an immense number of companies and entities climbing onto the digital bandwagon, cybersecurity considerations have come up as limelight. Besides, new technologies such as Big Data, IoT, and Artificial Intelligence/Machine Learning are gradually more making inroads into our everyday lives, the threats related to cybercrime are mounting as well. Additionally, the usage of mobile and web apps in transacting financial information has put the complete digital stuff exposed to cybersecurity breaches.
The inherent risks and vulnerabilities found in such apps can be exploited by attackers or cybercriminals to draw off crucial information data counting money. Internationally, cyber-security breaches have caused a yearly loss of USD 20.38 million in 2019 (Source: Statista). Plus, cybercrime has led to a 0.80 percent loss of the entire world’s Gross domestic product, which sums up to approx. USD 2.1 trillion in the year 2019 alone (Source: Cybriant.com).
Statista Report 2018 “Security Threats at All-Time High”. The no. of security threats or vulnerabilities in all kinds of Information Technology software is at an all-time high.
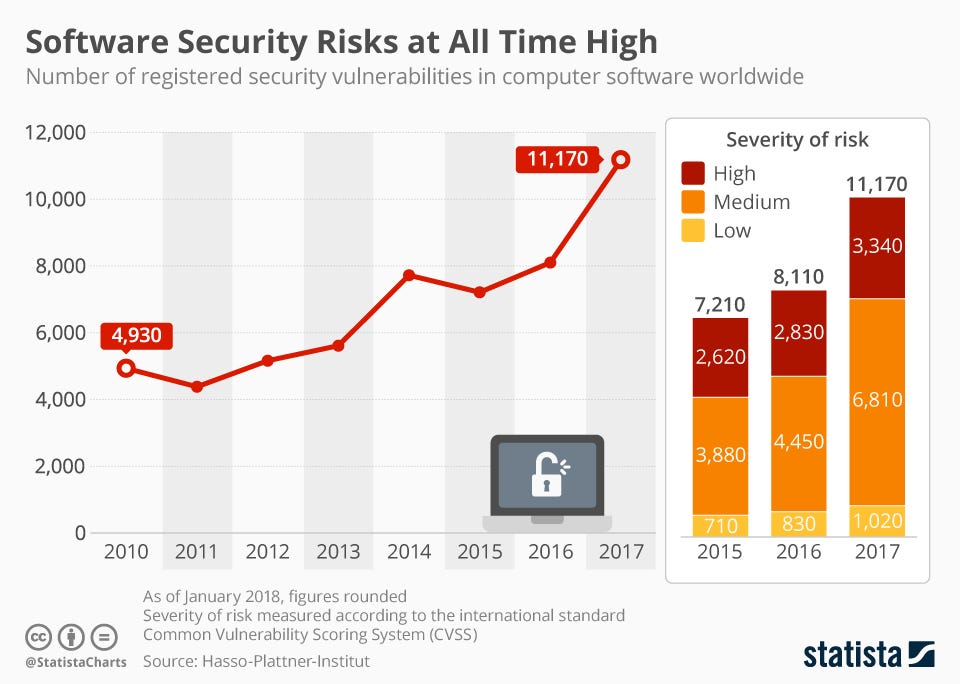
Even the spiraling pandemic has introduced a distressing impact on several enterprises and companies worldwide, the majority of companies arbitrarily attempted or moved their business sections to the untouched or unaffected digital space. Most security funds were, yet, also battered as a collateral outcome of the complete economic downturn. The shrinking budgets mainly exacerbated traumatic digital transformation by gross disregard of privacy and cybersecurity components of the subtle process.
To stem the rot and preempt adverse penalties of cyberthreat or crime, like losing client trust and brand repute, cybersecurity testing should be made compulsory. Cybersecurity expense is nonetheless forecasted to rebound and hit again in the year 2021, giving relief for exhausted CISOs, and their shattered IT, cybersecurity teams. Meanwhile, I would like to acquaint you with a series of best cybersecurity tools that can make a palpable divergence for your overall security program and 2021 budget plans.
What Is Penetration Testing?
The penetration test is a kind of Security testing that is carried out to assess the security of the system (software, hardware, information system, or networks environment). The main objective of this type of testing is to scrutinize all the security risks or vulnerabilities that are found in an app by assessing the system’s security with malevolent techniques and to safeguard the data from the hackers and manage the system’s functionality. Penetration testing is a kind of Non-functional test which intends to make official attempts to breach the system’s security. It is also called a Pen Test or Pen Testing and the QA engineer or tester who performs this testing is considered as a pen tester aka ethical hacker.
What Are the Best Cyber Security Tools for 2021?
Any app security testing method shall require the conduct of a functional test. This way, several security issues, and vulnerabilities can be detected, which if not rectified in time can result in hacking. There are a plethora of paid and open source testing tools available in the market. Let’s discuss the top 10 cybersecurity testing tools to look out for in 2021:
1. NMap

NMap is a short form of Network Mapper. NMap is an open-source and free security scanning tool for security auditing and network exploration. It works on Windows, Linux, HP-UX, Solaris, BSD variants (comprising Mac OS), AmigaOS. NMap is used to detect what hosts are accessible on the network, what versions and OSs they are running, what services those hosts are providing, what kind of firewalls/ packet filters are in use etc., Several network and systems administrators find it beneficial for regular jobs like check for open ports, maintaining service upgrade schedules, network inventory, and monitoring service or host uptime. It comes with both GUI interfaces and command line
Core Features:
- Determines hosts on a network
- It is used to determine network inventory, network mapping, maintenance, and asset management
- Produces traffic to hosts on a network, response time measurement, and response analysis
- Used to recognizes open ports on target hosts in the arrangement for auditing
- To search and exploit risks as well as vulnerabilities in a network
Download: NMap
2. Wireshark

It is one of the best tools and freely accessible open-source pen-testing tools. Generally, it is one of the network protocol analyzers, it allows you to capture and coordinatively browse the traffic running on a system network. It runs on Linux, Windows, Unix, Solaris, Mac OS, NetBSD, FreeBSD, and several others. Wireshark can be extensively used by educators, security experts, network professionals, and developers. The information that is recovered through the Wireshark software testing tool can be viewed through a Graphical User Interface or the TTY-mode TShark utility.
Core Features:
- Rich VoIP analysis
- Live capture and offline scrutiny
- In-depth examination of hundreds of protocols
- Runs on UNIX, Linux, Windows, Solaris, macOS, NetBSD, FreeBSD, & various others
- Captured system or network data can be browsed through a GUI, or through the TTY-mode TShark utility
- Read/write several variant capture file formats
- Captured files compressed via gzip can be de-compressed concurrently
- Coloring rules can be applied to the packet list for intuitive and rapid analysis
- Live data can be read from Blue-tooth, PPP/HDLC, internet, ATM, Token Ring, USB, etc.,
- Outcome can be exported to PostScript, CSV, XML, or plain text
Download: Wireshark
3. Metasploit

It is a computer security project that offers the user vital information about security risks or vulnerabilities. This framework is an open-source pen test and development platform that offers you access to the recent exploit code for several apps, platforms, and operating systems. Some of the jobs that can be attained in Metasploit from a pen test perspective comprise vulnerability scanning, listening, and exploiting known vulnerabilities, project reporting, and evidence collection. It has a command-line and Graphical User Interface clickable interface that works on Linux, Windows, as well as Apple Mac OS. Metasploit is a commercial tool but it comes with an open-source limited trial.
Core Features:
- Network discovery
- It has a command-line and GUI interface
- Works on Windows, Linux, & Mac OS X
- Module browser
- Basic exploitation
- Manual exploitation
- Vulnerability scanner import
- Metasploit community edition is offered to the InfoSec community without charge
Download: Metasploit
4. Netsparker
This commercial security test tool is a web app security scanner. Netsparker is a deadly accurate, automatic, and simple to use web app security scanner. This amazing tool is mainly used to identify security risks automatically like Cross-Site Scripting (XSS) and SQL injection in web services, web apps, and websites. Its proof-based Scanning technology does not simply report risks; it also generates a Proof of Concept to confirm they aren’t false positives. Therefore, there is no point in wasting your time by verifying the detect vulnerabilities manually after a scan is ended.
Core Features:
- Advanced web scanning
- Vulnerability assessment
- HTTP request builder
- Web services scanning
- Proof-centric scanning technology for dead-accurate threats finding and scan outcomes
- Full HTML5 support
- SDLC integration
- Exploitation
- Reporting
- Manual tests
- Automated identification of custom 404 error pages
- Anti-Cross-site Request Forgery (CSRF) token support
- Anti-CSRF token support
- REST API support
Download: Netsparker
5. Acunetix

It is a completely automatic web vulnerability scanner that identifies and reports on over 4500 web app vulnerabilities counting all variants of XSS XXE, SSRF, Host Header Injection, and SQL Injection. Acunetix smartly detects around 4500 web vulnerabilities. Acunetix is a commercial tool. Its DeepScan Crawler scans AJAX-heavy client-side SPAs and HTML5 websites. It enables users to export detected vulnerabilities to problem trackers like GitHub, Atlassian JIRA, Microsoft TFS (Team Foundation Server). It is obtainable on Linux, Windows, and Online.
Core Features:
- A high detection rate of risks and vulnerabilities with lower false positives
- Integrated vulnerability management — organize and control risks
- Deeply crawl and scrutinize — automatic scans all websites
- Integration with popular WAFs and Issue trackers like GitHub, JIRA, TFS
- Open-source network security scanning and Manual test tools
- Run on Linux, Windows, and online
Download: Acunetix
6. Nessus

It is a vulnerability assessment solution for security practitioners and it is formed and maintained by a company called Tenable Network Security. Nessus aids in detecting and fixing vulnerabilities like software flaws, malware, missing patches, and misconfigurations across a variety of OSs, apps, and devices. It supports Windows, Linux, Mac, Solaris, etc. It specializes in IPs scan, website scanning, compliance checks, Sensitive data searches, etc., and assists to detect the ‘weak-spots’.
Core Features:
- Configuration audits
- Mobile device audits
- Reports can be simply tailored to sort by host or vulnerability, generate an executive summary, or compare scanning outcomes to highlight alterations
- Detect vulnerabilities that enable a remote attacker to access confidential data from the system
- Identifies both the remote faults of the hosts that are on a network and their local flaws and missing patches as well
Download: Nessus
7. W3af

It is a Web Application Attack and Audit Framework. W3af is a free tool. W3af secures web apps by searching and exploiting all web app vulnerabilities. It determines 200 or more vulnerabilities and controls your overall risk exposure on the website. It detects all sorts of vulnerabilities such as Cross-Site Scripting (XSS), SQL injection, unhandled application errors, Guessable Credentials, and PHP misconfigurations. It has both a console and graphical UI. It works on Mac, Linux, and Windows OS.
Core Features:
- Assimilation of web and proxy servers into the code
- Proxy support
- Injecting payloads into roughly every section of the HTTP request
- HTTP Basic and Digest authentication
- Cookie handling
- UserAgent faking
- HTTP response cache
- DNS cache
- File upload using multipart
- Add custom headers to requests
Download link: W3af
8. Zed Attack Proxy

Zed Attack Proxy is a free and open-source security testing tool, developed by OWASP. Popularly known as ZAP, Supported by Unix/Linux, Windows, and Mac OS, ZAP allows you to find a set of security risks and vulnerabilities in web apps, even at the time of the development and testing phase. This tool is simple to use, even if you are a novice in pen-testing.
Core Features:
- Authentication support
- AJAX spiders
- Automatic Scanner
- Forced Browsing
- Dynamic SSL certificates
- Web Socket Support
- Plug-n-hack support
- Intercepting Proxy
- REST-based API and so on
Download link: ZAP
9. Burpsuite

It is also essentially a scanner (with a restricted “intruder” tool), even though several security test experts swear that penetration test without this tool is unimaginable. It isn’t free, yet very lucrative. It generally works wonders with crawling content and functionality, intercepting proxy, web app scanning, etc. One can use this on Mac OS X, Windows, and Linux environments.
Core Features:
- Cross-Platform Supported
- Very Light Weight And Stable
- Can Work With Almost All Browsers.
- Perform customize attacks
- Well Design User Interface
- Can Assist in crawling Website
- Aid in scanning Https/ HTTP Request and Response
Website: Burp suite
10. Sqlninja

It is one of the best open-source penetration testing tools. The aim of Sqlninja is to exploit SQL injection threats and vulnerabilities on a web app. This automated testing tool utilizes Microsoft SQL Server as a back-end. Sqlninja has a command-line interface. Sqlninja works on Linux, as well as Apple Mac OS X. It comes with a slew of descriptive features, counting remote commands, DB fingerprinting, and its detection engine.
Core features:
- Direct and reverse shell, both for UDP and TCP
- Fingerprinting of the remote SQL Server
- Formation of a custom XP cmdshell when the original one has been disabled
- Withdrawal of data from the remote Database
- Operating System privilege escalation on the remote database server
- Reverse scan to seek a port that can be utilized for a reverse shell
Download: Sqlninja
Wrapping Up
These are the top cybersecurity testing tools that will give you security for your personal data, mitigate the rates of data breaches, as well as stolen hardware. Other advantages of these tools count tighter security and greater privacy. These must-have security tools will help you evade cyberattacks and secure your IT infrastructure. Lastly, such security software requires up-gradation and maintenance to constantly have top-notch security.
10 Cyber Security Tools to Watch Out for in 2021 was originally published in Dev Genius on Medium, where people are continuing the conversation by highlighting and responding to this story.





![Best USB WiFi Adapter For Kali Linux 2021 [Updated October] Best USB WiFi Adapter For Kali Linux 2021 [Updated October]](https://infocerts.com/wp-content/uploads/2021/12/Best-USB-WiFi-Adapter-For-Kali-Linux-2021-Updated-October-infocerts.jpg)













 The collaboration between Bahrain’s Tamkeen, a public authority responsible for the skills development of the Kingdom’s workforce, and EC-Council, a trusted global leader in cybersecurity workforce development, have resulted in Tamkeen endorsing the Certified Application Security Engineer program (CASE .Net & CASE Java) for all Bahrainis. These 2 programs were added to Tamkeen’s specially approved list of training programs curated to uplift the much-needed cyber skills development in […]
The collaboration between Bahrain’s Tamkeen, a public authority responsible for the skills development of the Kingdom’s workforce, and EC-Council, a trusted global leader in cybersecurity workforce development, have resulted in Tamkeen endorsing the Certified Application Security Engineer program (CASE .Net & CASE Java) for all Bahrainis. These 2 programs were added to Tamkeen’s specially approved list of training programs curated to uplift the much-needed cyber skills development in […]
 DUBAI, UAE, 30 July 2021 – With digital threats on the rise, Mindware, one of the leading Value-Added Distributors (VADs) in the Middle East and Africa, announced that it had signed a partnership with the International Council of E-Commerce Consultants (EC-Council). EC-Council is the owner and developer of the world-renowned Certified Ethical Hacker (CEH) program as well as multiple other […]
DUBAI, UAE, 30 July 2021 – With digital threats on the rise, Mindware, one of the leading Value-Added Distributors (VADs) in the Middle East and Africa, announced that it had signed a partnership with the International Council of E-Commerce Consultants (EC-Council). EC-Council is the owner and developer of the world-renowned Certified Ethical Hacker (CEH) program as well as multiple other […]
 Vertical Institute, a technology education provider in Singapore, recently announced their official partnership with EC-Council to offer in-demand tech programs such as Certified Blockchain Professional. “Since inception in 2019, we’ve digitally empowered more than 2,000 people from Singapore and Southeast Asia with the most in-demand skills in tech. We are thrilled to be working with EC-Council to offer courses like […]
Vertical Institute, a technology education provider in Singapore, recently announced their official partnership with EC-Council to offer in-demand tech programs such as Certified Blockchain Professional. “Since inception in 2019, we’ve digitally empowered more than 2,000 people from Singapore and Southeast Asia with the most in-demand skills in tech. We are thrilled to be working with EC-Council to offer courses like […]![Best USB WiFi Adapter For Kali Linux 2021 [Updated August] Best USB WiFi Adapter For Kali Linux 2021 [Updated August]](https://infocerts.com/wp-content/uploads/2021/08/Best-USB-WiFi-Adapter-For-Kali-Linux-2021-infocerts.jpg)
![Best USB WiFi Adapter For Kali Linux 2021 [Updated July] Best USB WiFi Adapter For Kali Linux 2021 [Updated July]](https://infocerts.com/wp-content/uploads/2021/07/Best-USB-WiFi-Adapter-For-Kali-Linux-2021-Updated-July-infocerts.jpg)
