Network Security Testing – What Should You know ?


May 3, 2022 A Russian state-sponsored threat actor has been observed targeting diplomatic and government entities as part of a series of phishing campaigns commencing on January 17, 2022. Threat intelligence and incident response firm Mandiant attributed the attacks to a hacking group tracked as APT29 (aka Cozy Bear), with some set of the activities …
Russian Hackers Targeting Diplomatic Entities in Europe, Americas, and Asia Read More »
Why You Should Become a Certified Cybersecurity Technician The overall economic cost of cybercrime is expected to reach more than USD 133 billion by the end of the year, with attacks ranging in scope from breaches of a single computer to thefts of as many as 3 billion records (Lazic, 2021). In 2019 alone, 63.8%…
The post Why You Should Become a Certified Cybersecurity Technician appeared first on Cybersecurity Exchange.
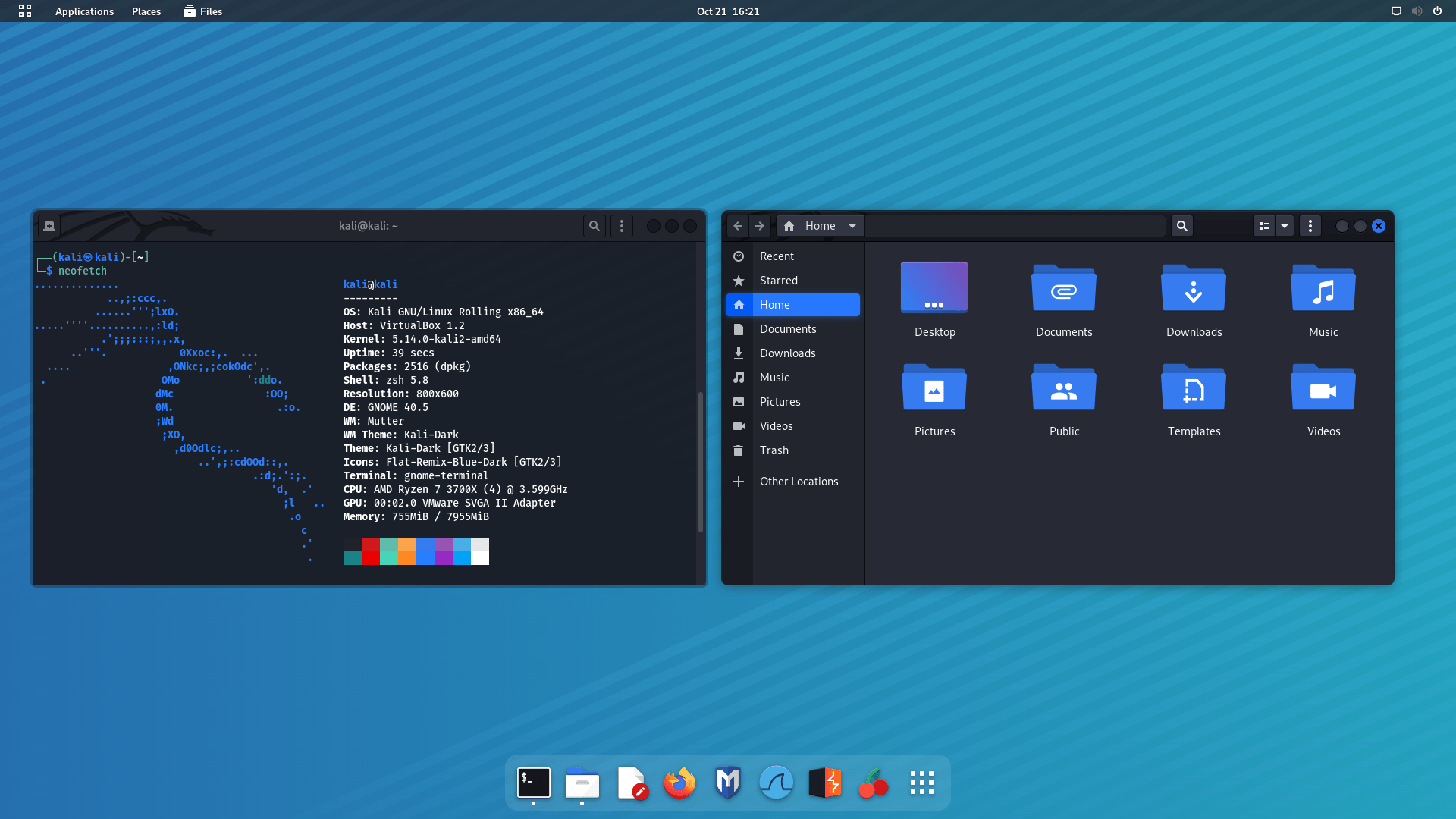
The last update of Kali Linux in 2021 is Rolling to ROCK.
Say Welcome to Kali Linux 2021.4! This release welcomes a mixture of new items as well as enhancements of existing features, and is ready to be downloaded (from our updated page) or upgraded if we have an existing Kali Linux installation.
The summary of the changelog since the 2021.3 release from September 2021 is:
As we announced in Kali 2021.1 we supported installing Kali Linux on Parallels on Apple Silicon Macs, well with 2021.4, we now also support it on the VMware Fusion Public Tech Preview thanks to the 5.14 kernel having the modules needed for the virtual GPU used. We also have updated the open-vm-tools package, and Kali’s installer will automatically detect if we are installing under VMware and install the open-vm-tools-desktop package, which should allow we to change the resolution out of the box. As a reminder, this is still a preview from VMware, so there may be some rough edges. There is no extra documentation for this because the installation process is the same as VMWare on 64-bit and 32-bit Intel systems, just using the arm64 ISO.
As a reminder, virtual machines on Apple Silicon are still limited to arm64 architecture only.
Starting Kali Linux 2021.4, the Samba client is now configured for Wide Compatibility so that it can connect to pretty much every Samba server out there, regardless of the version of the protocol in use. This change should make it easier to discover vulnerable Samba servers “out of the box”, without having to configure Kali.
This setting can be changed easily via the command-line tool kali-tweaks. In the Hardening section, one can choose the value Default instead, which reverts back to Samba’s usual default, and only allow using modern versions of the Samba protocol.
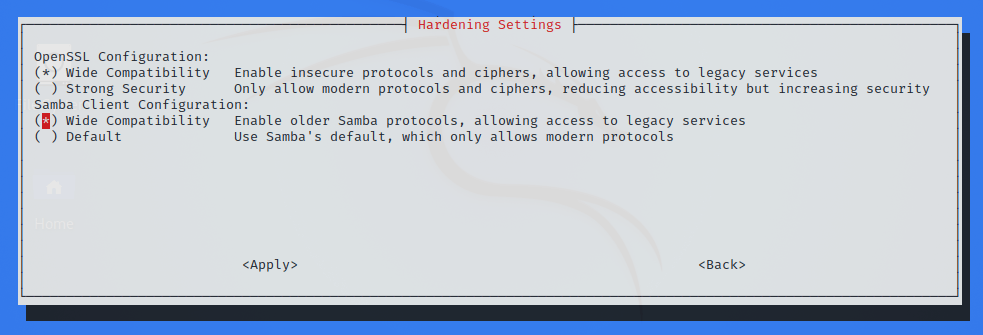
As one can see on this screenshot, there’s also a similar setting for OpenSSL. We might want to refer to the 2021.3 release announcement for more details on this setting.
By default, when a Kali system is updated, the package manager (APT) downloads packages from a community mirror nearby. But did we know that it’s also possible to configure Kali to get its package from the CloudFlare CDN? To be honest, this is old news. But what’s new is that we can now use kali-tweaks to quickly configure whether APT should use community mirrors or the CloudFlare CDN.
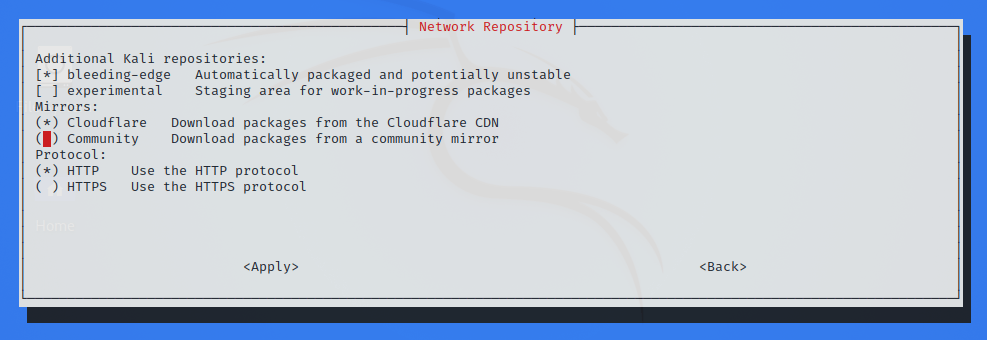
So which one is best, community mirrors or CloudFlare CDN? There’s no good answer. The time that it actually takes to update Kali can vary greatly and depends on many factors, including the speed of our Internet connection, our location, and even the time of day, if ever we live in a place where Internet traffic jam occurs at rush hour. The point is: if ever Kali updates are slow, the best we can do is to try to switch from community mirrors to CloudFlare CDN, or the other way round, and find what works best for we. And with kali-tweaks, it’s never been easier!
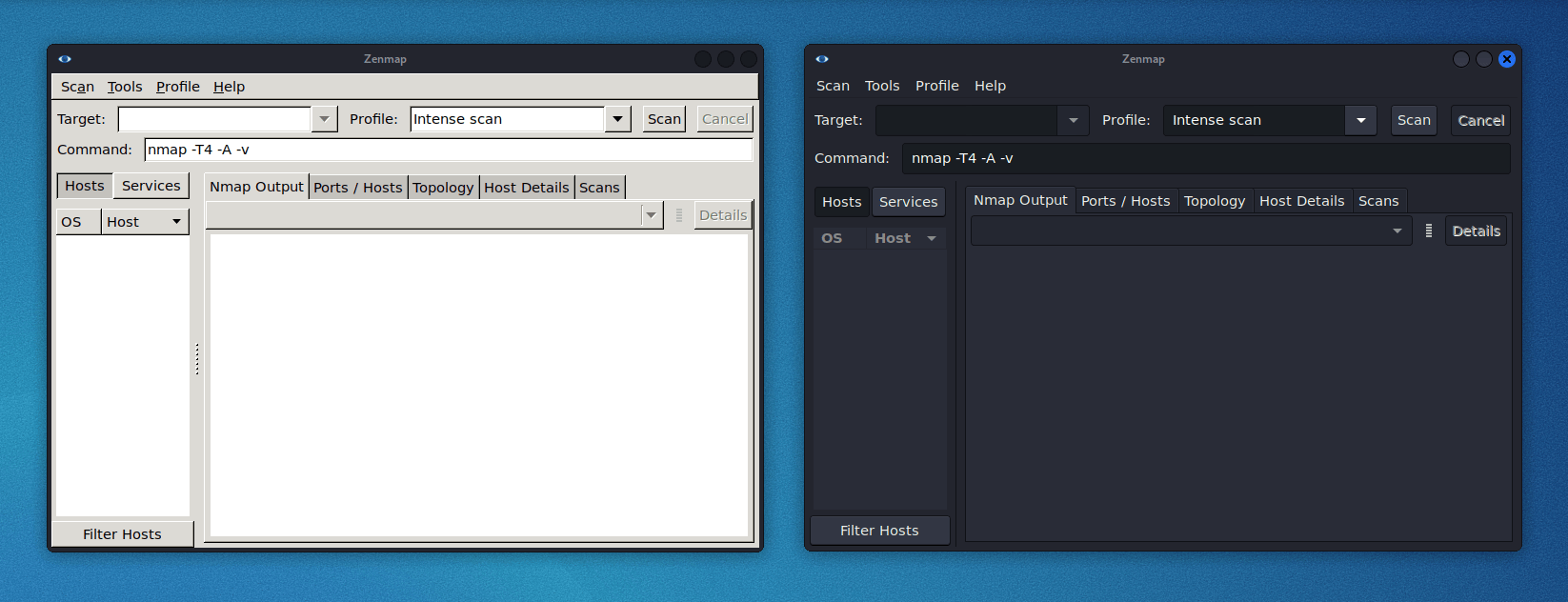
With the latest update of Kaboxer tools no longer look out of place, as it brings support for window themes and icon themes (placed respectively inside /usr/share/themes and /usr/share/icons). This allows the program to properly integrate with the rest of the desktop and avoids the usage of ugly fallback themes.
Here is a comparison of how zenmap (zenmap-kbx package) looks with the default Kali Dark theme, compared to the old appearance:
It would not be a Kali release if there were not any new tools added! A quick run down of what’s been added (to the network repositories):
This release brings updates for all the 3 main desktops (Xfce, GNOME, and KDE), but one that is common to all of them is the new window buttons design. Previous buttons were designed to fit the window theme of Xfce but did not work well with the other desktops and lacked personality. The new design looks elegant on any of the desktops and makes it easier to spot the currently focused window.

The panel layout has been tweaked to optimize horizontal space and make room for 2 new widgets: the CPU usage widget and the VPN IP widget, which remains hidden unless a VPN connection is established.
Following the steps of other desktops, the task manager has been configured to “icons only”, which, with the slight increase in the panel’s height, makes the overall look cleaner and improves multitasking in smaller displays.
The workspaces overview has been configured to the “Buttons” appearance, as the previous configuration “Miniature view” was too wide and a bit confusing for some users. Now that each workspace button takes less space in the panel, we have increased the default number of workspaces to 4, as it’s a usual arrangement in Linux desktops.
To finish with the modifications, a shortcut to PowerShell has been added to the terminals dropdown menu. With this addition, we can now choose between the regular terminal, root terminal, and PowerShell.
If we prefer the previous configuration for any of the widgets, we can modify or remove them by pressing Ctrl + Right-Click over it.
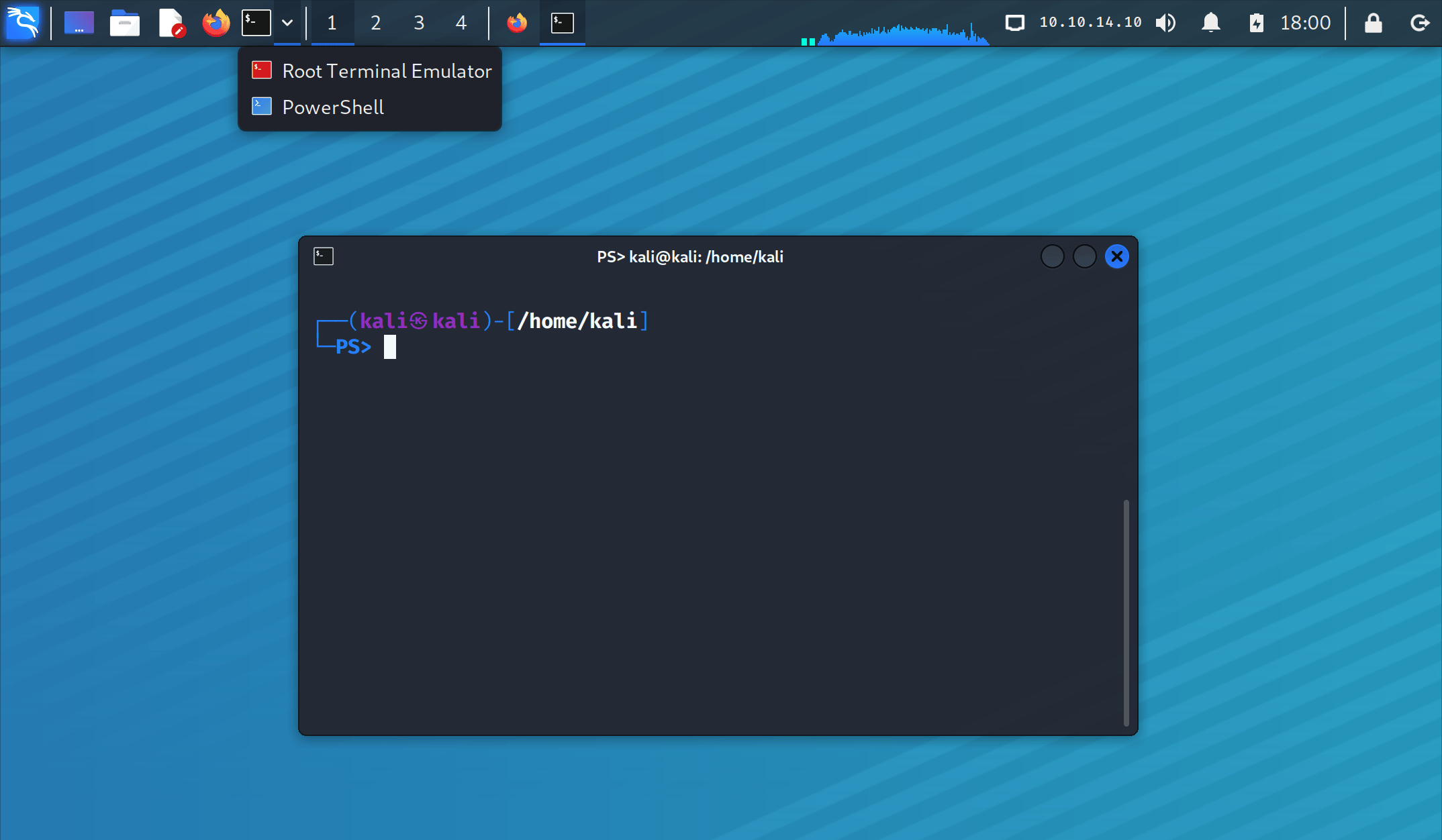
In addition to the Xfce design tweaks, In the image above, we can also observe the new customized prompt for PowerShell (in the two-line mode). Same as for zsh and bash, it includes an alternative one-line prompt that can be configured with kali-tweaks.
Bonus Tips For Virtual Desktops!
Alt + Insert / Alt + Delete
Ctrl + Alt + <ARROW_KEY> to move in the direction of the arrow key.
Shift we move the current focused window)Ctrl + Alt + <WORKSPACE_NUM> to move to a specific workspace, based on its number.Ctrl + Super + <WORKSPACE_NUM> to move a window to a specific workspace, based on its number.
In this update, GNOME desktop has received not one, but two version bumps. It’s been one year since the last major update of the GNOME desktop in Kali (with GNOME 3.38) and since then there have been two releases of the desktop environment:
All themes and extensions have been updated to support the new shell:
The KDE team celebrated its 25th anniversary releasing the update 5.23 of the Plasma desktop. This update, now available in Kali, brings a new design for the Breeze theme, which improves the look of Plasma with details that add glossiness and style to the desktop. Along with the theme improvements, the System Settings (Under Global Theme > Colors) brings a new option to pick the desktop accent color.
From Kali’s side, the new window theme for KDE is now based on the source code of the breeze theme instead of using the Aurorae theme engine. This fixes previous issues with window scaling for HiDPI displays.
With these theme changes, we may not get them if we upgrade Kali. This is because the theme settings are copied to our home folder when our user is first created. When we upgrade Kali, it is upgrading the operating system, so upgrading does not alter personal files (just system files). As a result, in order to get these theme tweaks, we need to either:
kali@kali:~$ mv ~/.config/xfce4{,-$(date +%Y.%m.%d-%H.%M.%S)}
kali@kali:~$
kali@kali:~$ cp -rbi /etc/skel/. ~/
kali@kali:~$
kali@kali:~$ xfce4-session-logout --reboot --fast
Thanks to the amazing work of @yesimxev, we have a new addition to the NetHunter app: The Social-Engineer Toolkit!
This release features the first module from SET: the Spear Phishing Email Attack, with many more to come – watch this space…
Now we can use the Kali NetHunter app to customise our own Facebook, Messenger, or Twitter direct message email notifications for our social engineering attacks:

Thanks to everyone that contributed to this feature by participating in the Twitter poll. We could not have done it without input!
Notable changes this release
kalipi-config will allow we to switch between them, if we would like to test different versions.echo 1 | sudo tee /sys/devices/system/cpu/cpufreq/boost to enableecho 0 | sudo tee /sys/devices/system/cpu/cpufreq/boost to disableKali ARM build-scripts have seen a massive amount of changes:
--minimal)--slim) if we would like to build a custom image up from scratchkali-tweaks that help we follow those best practices to enable (or disable) some of the supplementary repositories.Anyone can help out, anyone can get involved!
Kali-Cloud & Cron
Some users noticed that the venerable cron package was missing from the Kali AWS Cloud image. This was not intentional, and it’s now fixed.
Remote Desktop Protocol Audio
“The quieter you become, the more you are able to hear”, goes the saying. And for those running Kali in a VM and using RDP to connect, it’s been very quiet indeed, as the sound never worked with this configuration. However this long period of silence is coming to an end! Sound should be enabled and work out of the box from now on. If ever it does not, make ourself heard on the bug tracker 😉
Python Command
The command python is no more! Instead, we need to use python3 (or if we have to, python2 due it being at End Of Life). Alternatively we can install python-is-python3 to restore python as an alias for python3.
Fresh Images: So what are waiting for? Start downloading already!
Seasoned Kali Linux users are already aware of this, but for the ones who are not, we do also produce weekly builds that you can use as well. If you cannot wait for our next release and you want the latest packages (or bug fixes) when you download the image, you can just use the weekly image instead. This way you’ll have fewer updates to do. Just know that these are automated builds that we do not QA like we do our standard release images. But we gladly take bug reports about those images because we want any issues to be fixed before our next release!
Existing Installs: If you already have an existing Kali Linux installation, remember you can always do a quick update:
┌──(kali㉿kali)-[~]
└─$ grep VERSION /etc/os-release
VERSION="2021.4"
VERSION_ID="2021.4"
VERSION_CODENAME="kali-rolling"
┌──(kali㉿kali)-[~]
└─$ uname -v
#1 SMP Debian 5.14.16-1kali1 (2021-11-05)
┌──(kali㉿kali)-[~]
└─$ uname -r
5.14.0-kali4-amd64
NOTE: The output of uname -r may be different depending on the system architecture.
 In response to the expanding threat landscape, EC-Council and CyberArm, KSA, have entered into a strategic alliance to cultivate a security-aware culture. Riyadh, Kingdom of Saudi Arabia, September 27, 2021 –The tactical initiative between EC-Council and CyberArm aims to support workforce development and to assist businesses in the region to be cyber safe by equipping them with adequate resources and […]
In response to the expanding threat landscape, EC-Council and CyberArm, KSA, have entered into a strategic alliance to cultivate a security-aware culture. Riyadh, Kingdom of Saudi Arabia, September 27, 2021 –The tactical initiative between EC-Council and CyberArm aims to support workforce development and to assist businesses in the region to be cyber safe by equipping them with adequate resources and […] September 29th 2021, Kingdom of Saudi Arabia – Security awareness is a significant cause for concern for organizations, and never more so than when users are working remotely. The use of cloud-based collaboration tools to facilitate remote work has increased the amount of sensitive data accessed by end-users. As a result, organizations are more prone to security vulnerabilities and insider […]
September 29th 2021, Kingdom of Saudi Arabia – Security awareness is a significant cause for concern for organizations, and never more so than when users are working remotely. The use of cloud-based collaboration tools to facilitate remote work has increased the amount of sensitive data accessed by end-users. As a result, organizations are more prone to security vulnerabilities and insider […] Dubai UAE, 30th August 2021 – The upsurge in the hybrid work culture augments the need for critical infrastructure and resource availability. Consequentially, security knowledge becomes a concern for firms with end-users handling and accessing sensitive information. In response to this, EC-Council and Saiber Innovation Technologies team up to raise cybersecurity awareness in the Middle East by assisting businesses to […]
Dubai UAE, 30th August 2021 – The upsurge in the hybrid work culture augments the need for critical infrastructure and resource availability. Consequentially, security knowledge becomes a concern for firms with end-users handling and accessing sensitive information. In response to this, EC-Council and Saiber Innovation Technologies team up to raise cybersecurity awareness in the Middle East by assisting businesses to […]
The post EC-Council and Saiber Innovation Technologies, UAE Join Forces appeared first on EC-Council.
Reading Time: 4 minutes Banking and financial institutions have been under attack from various and considerable cyber-threats. Every year, this sector loses a massive chunk of its funds to criminal activities like phishing, ransomware, malware, etc. Due to this, cybersecurity has become a primary concern in this sector. The scale of attacks and damages have opened new vacancies in…
The post 3 Reasons Why Financial Institutions Need Penetration Testing appeared first on EC-Council Official Blog.
Reading Time: 3 minutes Many youngsters are interested in cybersecurity aspects with the increase and widespread of cybersecurity concepts and career opportunities. Ethical hacking is one of the major topics that gained a lot of attention and interest. There has been a rise in data breaches, ransomware, compromised data by various means, etc. To catch a hacker, it is…
The post What is Footprinting and its Techniques in Ethical Hacking? appeared first on EC-Council Official Blog.
During surfing the web sometimes we welcomed with a pop-up, after entering a web page. Even on our website now have a pop-up for the very first time. Suppose our system can be attacked by these pop-ups, may be malicious payloads comes in to our system or our sensitive data is stolen.
Today in our this article we will going to cover the Cross-Site Scripting and we also learn how an attacker executes malicious JavaScript codes over at the input field and generates pop-us to deface the web-application or hijack user’s session.
JavaScript is one of the most popular programming language of the web, more than 93% websites uses JavaScript. It is very flexible and easily mixes with the HTML codes.
A HTML webpage embedded with JavaScript shows it magic after the webpage loaded on the browser. JavaScript uses some functions to load an object over on a webpage. Functions like Onload, Onmouseover, Onclick etc. Then it prompts the alert as it coded. That’s why basically XSS payloads uses JavaScript codes.
Cross-Site Scripting aka XSS is a client side code injection attack where attacker is able to execute malicious scripts into trusted websites. All the websites are not vulnerable to XSS, only those websites or web-applications are effected where the input-parameters are not properly validated. From there attacker can send malicious JavaScript codes, and the user of the web-application has no way to know that it is loading attacker scripts. That’s why XSS is too much dangerous.
Confused with what we are talking about? Don’t like too much theory? Let we come to practical examples. Before that we should know that XSS are mainly three types, those are following:
“Stored XSS” is also known as “Persistence XSS” or “Type I”, as we can know from the name that it will be stored, that means attacker’s malicious JavaScript codes will be “stored” on the web-applications database, and the server further drops it out back, when the client visits the perticular website.
Because this happens in a very legitimate way, like when the client/user clicks or hovers a particular infected section, the injected malicious JavaScript code will get executed by the browser as it was already saved into the web-application’s database. For that being reason this attack doesn’t requires any phishing technique to trap the user.
The most common example of “Stored XSS” is the comment section of the websites, which allow any user to write his comment as in the form for comments. Now lets have a look with an example:
A web-application is asking to users to submit their feedback, in the following screenshot we can see the two fields one is for name and another is for the comment.
Now when we fill the form and hit “Sign Guestbook” button to leave our feedback, our entry gets stored into the database. We can see the database section highlighted in the following screenshot:
In this case the developer trusts us and hadn’t put any validator in the fields, or may be he forget to add validators. So this if this loophole found by an attacker, the attacker can take advantage of it. Without typing the comment in the Message section attacker may run any malicious script. The following script is given for an example:
When we put the JavaScript code into the “Message” section, we can see the web-application reflects with an alert poop-up.
In the database section we can see that the database has been updated with name, but the message section is empty.
This is a clear indication that our/attacker’s script is successfully injected.
Now let’s check if it really submitted on the database or not? We open another browser (Chrome) and try to submit a genuine feedback.
Here when we hit the “Sign Guestbook” button our this browser will execute the injected script, as we can see in the following screenshot:
We can see this also reflects our injected script, because it stored our input in the database. This is the stored based XSS.
Reflected XSS is also known as “Non-Persistence XSS” or “Type II”. When the web-application responds immediately on client’s input without validating what the client entered, this can lead an attacker to inject malicious browser executable code inside the single HTML response. This is also called “non-persistence”, because the malicious script doesn’t get stored inside the web-application’s database. That’s why the attacker needs to send the malicious link through phishing in order to trap the client.
Reflected XSS is the most common and it can be easily found on the “website’s search fields” where the attacker injects some malicious JavaScript codes in the text box/search box and, if the website is vulnerable, the web-page returns up the event described into the script.
Reflected XSS are mainly two types:
Lets check the concept of reflected XSS, we need to check the following scenario:
Here we have a webpage where we can enter our name and submit it. So, when we enter our name and submit it. A message prompts back over the screen, and say hello to us.
If we look at the URL then we can see the “name” parameter in the URL shows up that, that means the data has been requested over through the GET method.
Now we are going to try to generate some pop-ups by injecting JavaScript codes over into this “name” parameter as:
We need to put this script on the URL where our name was,
Now we can see that our JavaScript code is executed as an alert in the following screenshot:
Actually the developer didn’t set up any input validation over the function, and our input simply get “echo“.
This is an example of reflected XSS using GET method, for reflected XSS POST method we can’t see the request on the URL, in that case we need to use Burpsuite or WebScarab like tools to change the request and inject our JavaScript codes.
DOM-Based XSS is the vulnerability which appears up in a Document Object Model rather than in the HTML pages. But before that we need to know what is Document Object Model.
DOM or Document Object Model describes up the different web-page segments like – title, headings, forms, tables etc, and even the hierarchical structure of an HTML page. That because this API increases the skill of the developers to produce and change HTML and XML documents as programming objects.
When an HTML document is loaded into a web browser, it becomes a “Document Object”.
DOM-based XSS vulnerabilities normally arise when JavaScript takes data from an attacker-controllable source, such as the URL, and passes it to a sink (a dangerous JavaScript function or DOM object as eval()) that supports dynamic code execution.
This attack is different from stored and reflected XSS attacks because over in this attack developer can’t find the dangerous script in the HTML source code as well as in the HTML response, it only can be observed during the execution time. Didn’t understand well, let’s check out a DOM-based XSS example.
The following application permits us to opt a language shown in the following screenshot:
If we choose our language then we can see it on the URL. like previous (Reflected XSS GET) we can manipulate the URL to get the alert.
Then if we try to change the language we can see following:
After the language we put a ‘#’, this is the major diffrence between DOM-BAsed XSS and Reflected or Stored XSS is that it can’t be stopped by server-side filters because anything written after the ‘#’ (hash) will never forward to the server.
Haha ?, what the hell if we get an alert by doing these kind of stuffs, just this? nothing else? We click on the OK button and the pop-up alert is vanishing.
Wait, the pop-up speaks about a lot words. Let’s go back to the the first place, “We’ve come a long way from where we began”. Back to the Stored XSS section.
Here, in the stored XSS section, we know that our input is stored on the database of the web-application. In our previous example we created just an alert but we can do much more then it. For an example if we put any name in the name field and put the following JavaScript code on the message field.
And we captured the cookie as we can see in the following screenshot:
Now, if we navigate away from this page, from another browser, then return to the XSS stored page, our code should run again and present a pop-up with the cookie for the current session. This can be expanded upon greatly, and with a bit more knowledge of JavaScript, an attacker can do a lot of damage.
To know more about exploitation of XSS we can go though this official PortSwigger documentation, this is well written.
As a cybersecurity expert we try to find bugs on various services, not only that fixing them or giving an idea to fix them is also our duty. Forestalling Cross-Site scripting or XSS is trivial some times however can be a lot harder relying upon the intricacy of the application and the manners in which it handles client controllable information.
Normally we can stop XSS by using following guide:
There are tons of more article on this we can get from the internet. We found a very detailed article on preventing XSS attacks.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.