Best USB WiFi Adapter For Kali Linux 2021 [Updated August]
Best WiFi Adapter for Kali Linux
Here we have listed some best USB Wireless adapters Kali Linux in 2021. These WiFi adapters are 100% compatible with Kali Linux and supports monitor mode and packet injection, which will help a lot in WiFi penetration testing.
Best WiFi Adapter for Kali Linux
|
Sl No.
|
WiFi Adapter
|
Chipset
|
Best for
|
Buy
|
|
1
|
AR9271
|
Good Old Friend
|
||
|
2
|
RT 3070
|
Best in it’s Price Range
|
||
|
3
|
RT 3070
|
Compact and Portable
|
||
|
4
|
RT 5572
|
Stylish for the Beginners
|
||
|
5
|
RTL8812AU
|
Smart Look & Advanced
|
||
|
6
|
RTL8814AU
|
Powerful & Premium
|
||
|
7
|
RT5372
|
Chip, Single Band
|
Alfa AWUS036NH
We are using this USB WiFi adapter from the BackTrack days (before releasing Kali Linux) and still we consider it as one of the best. For it’s long range signals we can do our penetration testing jobs from a long distance.
Alfa AWUS036NH is plug and play and compatible with any brand 802.11g or 802.11n router using 2.4 GHz wavelength and supports multi-stream & MIMO (multiple input multiple output) with high speed transfer TX data rate up to 150 MBPS. It also comes with a clip which can be used to attach this adapter on a laptop lid.
- Chipset: Atheros AR 9271.
- Compatible with any brand 802.11b, 802.11g or 802.11n router using 2.4 Ghz wave-length.
- Includes a 5 dBi omni directional antenna as well as a 7 dbi panel antenna.
- Supports security protocols: 64/128-bit WEP, WPA, WPA2, TKIP, AES.
- Compatible with Kali Linux RPi with monitor mode and packet injection.
- High transmitter power of 28 dBm – for long-rang and high gain WiFi.
Alfa AWUS036NHA
Alfa again. Alfa provides the best WiFi adapters for Kali Linux. This adapter is the older version of Alfa AWUS036NH with Ralink RT3070 chipset. AWUS036NHA is the IEEE 802.11b/g/n Wireless USB adapter with 150 Mbps speed This is also compatible with IEEE 802.11b/g wireless devices at 54 Mbps.
This plug and play WiFi adapter supports monitor mode and packet injection in any Linux distribution and Kali Linux. Alfa AWUS036NHA comes with a 4 inch 5 dBi screw-on swivel rubber antenna that can be removed and upgrade up to 9 dBi.
- Chipset: Ralink RT 3070.
- Comes with a 5 dBi omni directional antenna as well as a 7 dBi panel antenna.
- Supports security protocols: 64/128-bit wep, wpa, wpa2, tkip, aes
- Compatible with Kali Linux (Also in Raspberry Pi) with monitor mode and packet injection.
Alfa AWUS036NEH
This Alfa WiFi Adapter is compact and tiny, but it has a good range. It supports plug and play so connect it with Kali Linux machine and start playing with WiFi security. The antenna is detachable and makes it very portable. We have used this to build our portable hacking machine with Raspberry Pi and Kali Linux.
Alfa AWUS036NEH is the ultimate solution for going out and red teaming attacks. The long high gain WiFi antenna will give us enough range to capture even low signal wireless networks. This adapter is slim and doesn’t require a USB cable to use.
- Chipset: Ralink RT 3070.
- Supports monitor mode and packet injection on Kali Linux and Parrot Security on RPi.
- Compact and portable.
Panda PAU09 N600
Besides Alfa, Panda is also a good brand for WiFi adapters with monitor mode. Panda PAU09 is a good WiFi adapter to buy in 2020. This dual-band plug & play adapter is able to attack both 2.4 GHz as well as 5 GHz 802.11 ac/b/g/n WiFi networks.
This adapter comes with a USB docker and dual antennas, which looks really cool. It is also detachable into smaller parts. This adapter is reliable even on USB 3 and works great and fully supports both monitor mode and injection which is rare on a dual band wireless card out of the box.
- Chipset: Ralink RT5572.
- Supports monitor mode and packet injection on Kali Linux, Parrot Security even in RPi.
- 2 x 5dBi antenna.
- It comes with a USB stand with a 5 feet cable.
- Little bit of heating issue (not so much).
Alfa AWUS036ACH / AC1200
In Kali Linux 2017.1 update Kali Linux was released a significant update – support for RTL8812AU wireless chipset. Now Alfa AWUS036ACH is a BEAST. This is a premium WiFi adapter used by hackers and penetration testers. It comes with dual antennas and dual band technology (2.4 GHz 300 Mbps/5 GHz 867 Mbps) supports 802.11ac and a, b, g, n.
These antennas are removable and if we require higher range, then we can connect an antenna with greater dbi value and use it as a long range WiFi link which makes this one of the best WiFi adapters. Also this adapter has an awesome look.
If budget is not an issue then this adapter is highly recommended.
- Chipset: RealTek RTL8812AU.
- Dual-band: 2.4 GHz and 5 GHz.
- Supports both monitor mode & packet injection on dual band.
- Premium quality with high price tag.
Alfa AWUS1900 / AC1900
Now this is the beast, then why is it at last? It is last because of its high price range. But the price is totally worth it for this USB WiFi adapter. If the previous adapter was a beast then it is a monster. Alfa AWUS1900 has high-gain quad antenna that covers a really long range (500 ft in an open area).
This is a dual band WiFi adapter with high speed capability 2.4GHz [up to 600Mbps] & 5GHz [up to 1300Mbps]. It also has a USB 3.0 interface.
Monitor mode and packet injection supported with both bands and it will be very useful for serious penetration testers. We also can attach this on our laptop display with it’s screen clip provided with the box.
What we got in the box?
- 1 x AWUS1900 Wi-Fi Adapter
- 4 x Dual-band antennas
- 1 x USB 3.0 cable
- 1 x Screen clip
- 1 x Installation DVD-Rom (doesn’t require on Kali Linux. Plug&Play)
- A consistent solution for network congestion!
- Chipset: RealTek RTL8814AU.
- Dual-band: 2.4 GHz and 5 GHz.
- Supports both monitor mode & packet injection on dual band.
- Premium quality with high price tag.
- Very long range.
Panda PAU 06
Extras
There are some more WiFi adapters that we did not cover because we didn’t test them on our hands. These WiFi adapters were owned by us and some of our friends so we got a chance to test these products. We didn’t listed some WiFi adapters like following:
- Leoxsys LEO-HG150N.
- TP Link N150 TL-WN722N Version 1 (Not available in Market Now).
Be Careful to choose from these, because we don’t know that they surely support monitor mode & packet injection or not. As per our own experience Alfa cards are the best in the case of WiFi Hacking.
How to Choose Best Wireless Adapter for Kali Linux 2020
Before going through WiFi adapter brands let’s talk something about what kind of WiFi adapter is best for Kali Linux. There are some requirements to be a WiFi penetration testing wireless adapter.
- Should support Monitor mode.
- The ability to inject packets and capture packets simultaneously.
Here are the list of WiFi motherboards supports Monitor mode and Packet injection.
- Atheros AR9271 (only supports 2.4 GHz).
- Ralink RT3070.
- Ralink RT3572.
- Ralink RT5370N
- Ralink RT5372.
- Ralink RT5572.
- RealTek 8187L.
- RealTek RTL8812AU (RTL8812BU & Realtek8811AU doesn’t support monitor mode).
- RealTek RTL8814AU
So we need to choose WiFi Adapter for Kali Linux carefully. For an Example, on the Internet lots of old and misleading articles that describe TP Link N150 TL-WN722N is good for WiFi security testing. But it is not true. Actually it was.
 |
| TP Link N150 TL-WN722N newer models doesn’t work |
The TP Link N150 TL-WN722N’s previous versions support monitor mode. The version 1 comes with Atheros AR9002U chipset and supports monitor mode. Version 2 has the Realtek RTL8188EUS chipset and doesn’t support monitor mode or packet injection. TP Link N150 TL-WN722N version 1 is not available in the market right now. So clear these things and don’t get trapped.
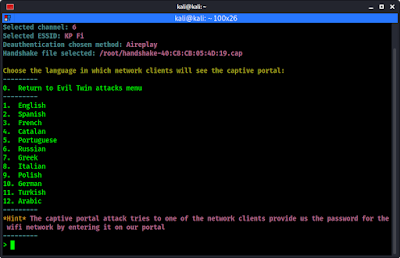
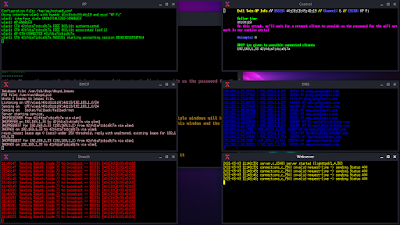
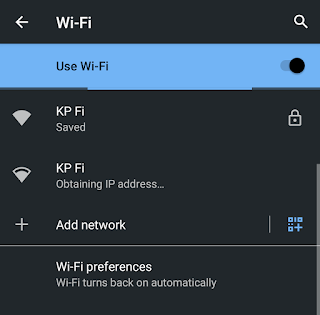
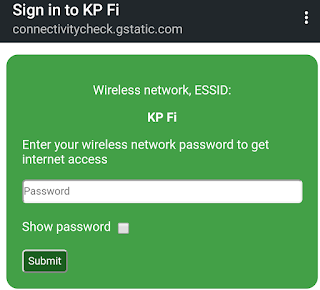
WiFi Hacking in Kali Linux
Kali Linux is the most widely used penetration testing operating system of all time. It comes with lots of tools pre-installed for cyber security experts and ethical hackers. We can perform web application penetration testing, network attack as well as wireless auditing or WiFi hacking. We have already posted some lots of tutorials on our website and some good WiFi auditing tutorials like AirCrack-Ng.
Why Do We Use External USB WiFi Adapters in Kali Linux?
A WiFi adapter is a device that can be connected to our system and allows us to communicate with other devices over a wireless network. It is the WiFi chipset that allows our mobile phone laptop or other devices which allows us to connect to our WiFi network and access the internet or nearby devices.
But most of the Laptops and mobile phones come with inbuilt WiFi chipset so why do we need to connect an external WiFi adapter on our system ? Well the simple answer is our in-built WiFi hardware is not much capable to perform security testing in WiFi networks.Usually inbuilt WiFi adapters are low budget and not made for WiFi hacking, they don’t support monitor mode or packet injection.
If we are running Kali Linux on Virtual Machine then also the inbuilt WiFi Adapter doesn’t work for us. Not even in bridge mode. In that case we also need an external WiFi adapter to play with WiFi networks. A good external WiFi adapter is a must have tool for everyone who has interest in the cyber security field.
Kali Linux Supported WiFi Adapters
It doesn’t make sense, when we are using Kali Linux then we are penetration testers so a basic WiFi adapter can’t fulfill our requirements. That’s why we should have a special WiFi adapter that supports monitor mode and packet injection. So in this tutorial Kali Linux supported means not only supported it means the chipset has ability to support monitor mode and packet injection.
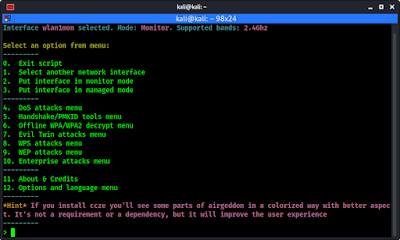
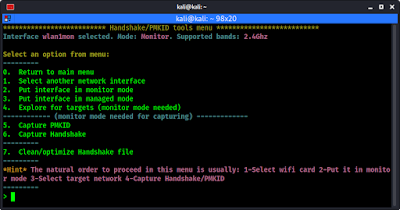
What is Monitor Mode
In wireless technology, the equivalent is monitor mode. This enables us to see and manipulate all wireless traffic passing through the air around us. Without this ability, we are limited to using our WiFi adapter to only connect to wireless Access Points (APs) that accept and authenticate us. That is not what we are willing to settle for.
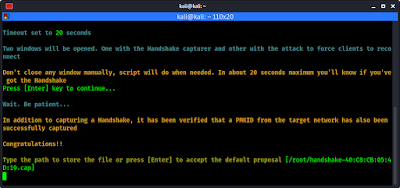
In the Aircrack-ng suite, we need to be able to use airodump-ng to collect or sniff data packets.
What is Packet Injection
Most WiFi attacks require that we are able to inject packets into the AP while, at the same time, capturing packets going over the air. Only a few WiFi adapters are capable of doing this.
WiFi adapter manufacturers are not looking to add extra features to their standard wireless adapters to suit penetration testers needs. Most wireless adapters built into your laptop are designed so that people can connect to WiFi and browse the web and send mails. We need something much more powerful and versatile than that.
If we can’t inject packets into the Access Point (in Aircrack-ng, this is the function of Aireplay-ng), then it really limits what we do.
If we are using Kali Linux and want to be a security tester or ethical hacker then a special WiFi adapter is a must have tool in our backpack. As per our own experience listed Alfa cards in this list are best USB wireless adapter for Kali Linux, going with them may be costly but they are really worth it. For more assistance comment below we reply each and every comment.












































.webp)