We are living in digital era. We are penetration testers, we need to protect the world. We need to be digital Sherlock Holmes. For that we need to find a criminal from a small clue. If we get a bad guy’s username or mail then we don’t need to manually search it on the internet. There are some OSINT (Open-Source Intelligence) tools to reduce our effort. Today we are going to talk about a tool called Profil3r on our Kali Linux. Not only for security experts even govt and law enforcement also can use the OSINT tools to gather information about some individuals or organizations from the ocean of internet.
Previously we already talked about Sherlock and Trape, we can use them to find someone on internet with some basic details, in our this article we are going to do the same using Profil3r in a very effective way.
Install Profil3r on Kali Linux
Profil3r is an OSINT tool that allows us to find potential profiles of a person on social networks, as well as their email addresses. This program also alerts us to the presence of a data leak for the found emails.
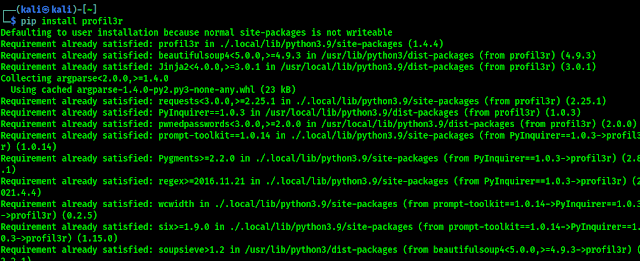
Installing is very easy, we need to just apply following command on our Kali Linux terminal to install Profil3r on our updated (latest python3 and pip3) system:
pip3 install profil3r
In the following screenshot we can see that Profil3r installation is started on our system, it will install the script and some dependencies to run it:
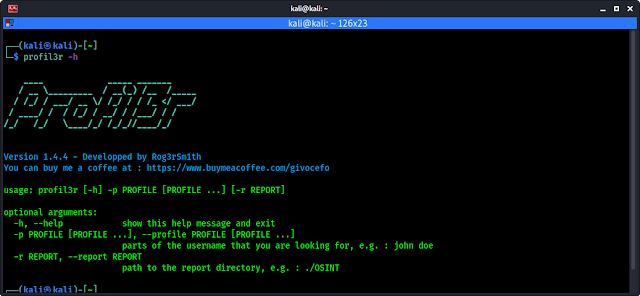
Now we can check it’s help by applying following command:
profil3r -h
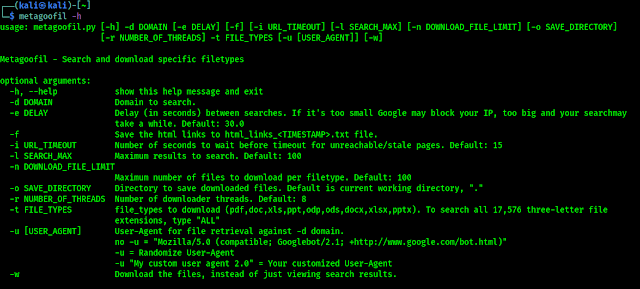
In the following screenshot we can see the help options of this profil3r tool.
We can see there are nothing much here, we can use -p flag to set the username or name of we are looking for. We can save the report output in HTML, JSON and CSV format using -r flag followed by directory location.
Running Profil3r on Kali Linux
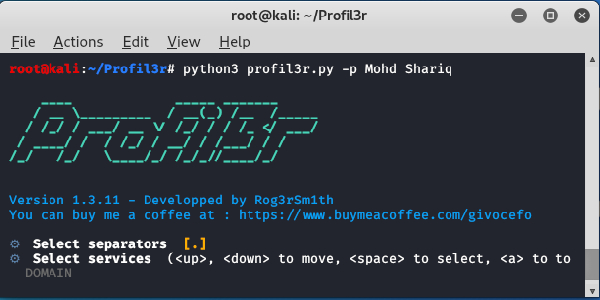
For an example we are looking for Jhon Doe, so we use following command on our terminal:
profil3r -p john doe -r /home/kali
After pressing Enter ↲ , Profil3r will prompt suggesting some possible usernames, as we can see in the following screenshot:
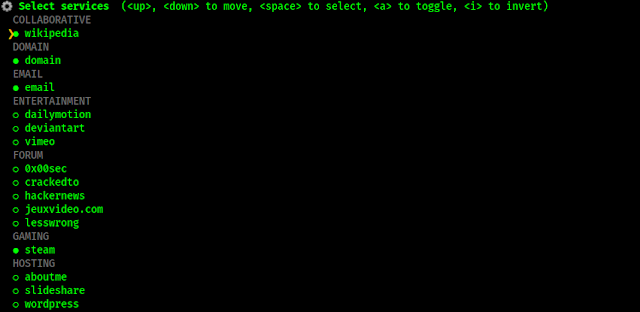
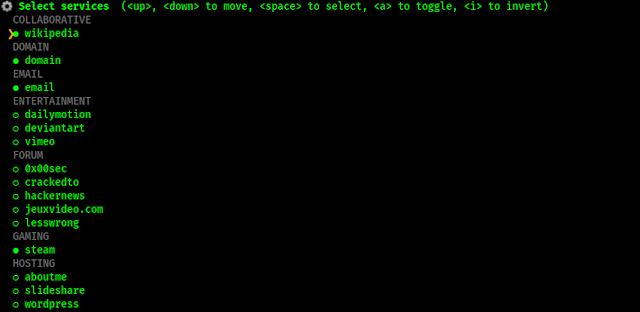
Here in the above screenshot we can see the suggested usernames, we can use UP⬆ and DOWN⬇ key to move our cursor, to select we need to use SPACE button (we can select multiple), also we can invert them by using I key, and toogle using A key. We need to press ENTER↲ after our selection to continue.
For an example we are going with john.doe username, Then we got a list of various type of sites, as we can see in the following screenshot:
Here also we need to select things we need to search (shown in following screenshot), because we are showing an example here so we are going with just few things. For a better search we need to select everythinng, but that is really time consuming.
After the selection we need to press Enter, it will take some time to complete the scans. In the following screenshot we can see how profil3r is working:
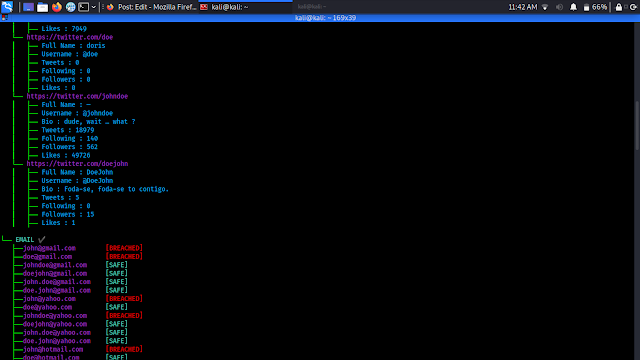
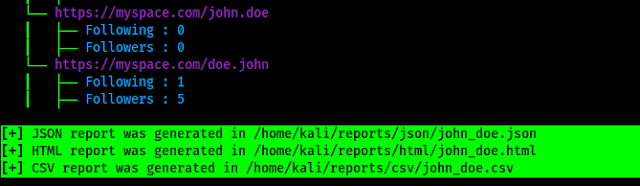
We can see that if founds some mail ids in data leak which may related to our target. After the scanning is complete is will generate a full report on our given path as we can see in the following screenshot:
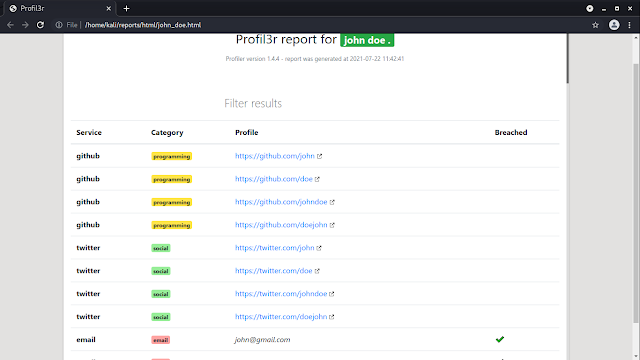
We can open this reports to see everything in a very organized way. In the following screenshot we have opened the HTML report output on browser.
This is how we can use Profil3r tool on our Kali Linux and easily get information about a human or organizations using the usernames. This OSINT tool is very important for finding someone on the internet.
Love our articles? Make sure to follow us on Twitter and GitHub, we post updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.