12 Best Anonymous Chat Apps to talk with Strangers (2021)
Anonymous chatting has its own set of perks. Firstly, you chat in complete anonymity- without history, without stereotypes, etc. Secondly, it is very liberating when the person you chat with has no idea about what you do or who you are.
This is why cam to cam chats are suddenly getting popular around the world. They have almost become like a fad. Owing to the trend, more and more sites are emerging to provide seamless chatting services. But, how do you choose the best one?
12 Best Anonymous Chat Sites
Online video chatting always has a set of concerns: is the chat going to be safe? Will there be any leakage of information, etc. So, to battle all these pre-conceived notions about online chats, below are the best anonymous chat apps to talk with strangers:
1. Bazoocam
Bazoocam is a nicely interfaced online video chatting platform. It functions in a fairly seamless way. With functions and features similar to ChatSites, Bazoocam too ensures an amazing chatting experience.
However, how does one ensure that the challenges faced under other cam chat sites will not be faced with Bazoocam? The below questions and answers on the issue will suffice:
How is Bazoocam different from other chat sites?
Bazoocam is different and somehow even superior to other chat sites. It has been designed with impeccable functions. The sheer structure of Bazoocam oozes convenience. You will be able to chat in one of the most comfortable interfaces. It does not matter whether you have done this before or not, you will still be comfortable with Bazoocam.
Can you chat anonymously on Bazoocam?
You can only chat anonymously on Bazoocam. The platform has its own set of protocols that only seek only very necessary information from its users. This means that the users are never asked for their personal details.
You can be relieved that the information you provide to Bazoocam will be completely discreet. You only provide very basic details that are sufficient enough for you to start chatting on the platform.
How much does one need to wait to be matched?
There is literally no wait time with Bazoocam. You can chat your time away with people day in and day out. As Bazoocam enjoys a lot of popularity, it has a plethora of users at all hours. Therefore, there will always be people willing and ready to chat.
So, you will always find a suitable match for yourself on the platform. You can further refine your search by opting for filtering your results. You can filter people based on their age, sex, location, etc. The more accurate your requirements are, the better you will be able to chat with people.
How much does Bazoocam cost?
The good news here is that Bazoocam is free. It does not cost at all to use the platform. It is extremely efficient as a webcam chatting platform, that too which is free. It has no hidden costs or subscription fees. You can be assured that you do not need to provide your payment details.
2. Chatrandom
Chatrandom is a very good online cam chatting alternative. It is a good way to find remote companionship. You choose who you want to chat with and whom you don’t want to chat with. With the feature of skipping people, you can just skip things you don’t want to engage with.
3. Chatki
The popularity of Chatki is also increasing because of its discreet features and functions. As the user base of the platform is proliferating each passing day, you will always manage to find companies on the platform. It is perfect and efficient.
4. Emerald Chat
Emerald Chat makes chatting fun and entertaining by adding some fun and entertaining elements. For instance, it offers its users with an avatar and username. The avatar and username will substitute for your real identity on the platform. You can engage in some fun role playing.
5. Chatroulette
Chatroulette is also a very popular online cam chatting site. It provides its users with the ease of chatting with someone based 1000 of miles away. Owing to its cosmopolitan user base, you will also be able to find some fun and entertaining people on the platform.
6. Camsurf
Camsurf is known to be one of the most user-friendly platforms. It has some incredible matching features. It will connect you with people who have the same tastes and interests as you. Further, with masking and masquerading features, it increases its lovability.
7. Flingster
As the name suggests, Flingster allows its users to have flings with people remotely. It is a fun and flirtatious platform wherein you can choose whom you want to chat with. There is no paucity of people on Flingster and you will always find the next person better than the previous.
8. Shagle
Shagle can get really addictive as a web based chatting service. It has been around for a while and has earned a lot of patronage from users around the world. It is fun, entertaining and immaculately designed. Even if you are a first timer, you will be able to use Shagle conveniently.
9. Dirtyroulette
Adults have different sets of needs and Dirtyroulette addresses them efficiently. This is a rather fun and uninhibited platform. You can be honest in your expectations with strangers. No one gets offended as everyone knows about their core purpose of being on the platform.
10. Coomeet
Coomeet lets its users meet with people from around the globe. It makes the world a really small place. Everytime is a busy time on Coomeet as people are honestly hooked to it. It is also very efficient in its interface.
11. Tinychat
Tinychat is a video chatting platform that provides you with multiple live feeds at the same time. This means that you could be chatting with many people at once. All this and more and none of the live feeds will ever get freezed.
12. Camzap
Camzap helps you in establishing some deep connections and bonds, that too with strangers. It is a really user-friendly platform. It has been around for long enough to have a lot of patronage. So, any time of the day you head to it, there will be people to chat with.
Conclusion
If you are looking for the perfect cam to cam chat site, it doesn’t get better or more extensive than the above sites. As compared to ChatSites, the kind of interface and engagement you get on these sites is far better than what you get anywhere else.












![Best USB WiFi Adapter For Kali Linux 2021 [Updated October] Best USB WiFi Adapter For Kali Linux 2021 [Updated October]](https://infocerts.com/wp-content/uploads/2021/12/Best-USB-WiFi-Adapter-For-Kali-Linux-2021-Updated-October-infocerts.jpg)




















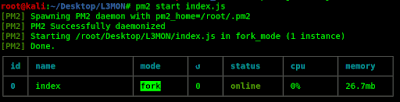
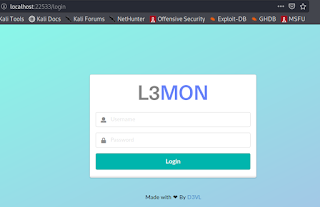
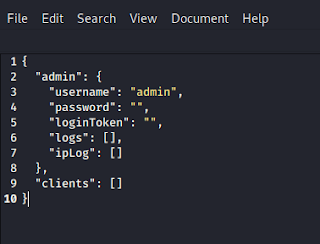
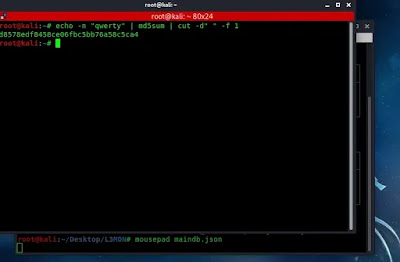
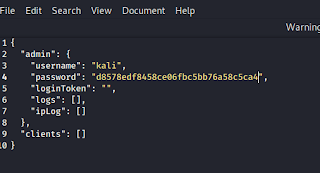



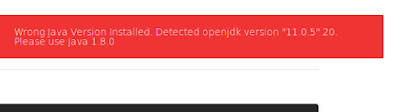
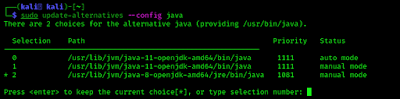




 November 29, 2021: WillCo Tech, a leading provider of compliance and readiness management software within the U.S. Federal government, is now partnering with EC-Council to offer cybersecurity training courses on their CyberSTAR software platform. With the recent attacks and increased threats facing government and critical infrastructure businesses, cybersecurity training within the federal government sector has never been more in-demand. Additionally, […]
November 29, 2021: WillCo Tech, a leading provider of compliance and readiness management software within the U.S. Federal government, is now partnering with EC-Council to offer cybersecurity training courses on their CyberSTAR software platform. With the recent attacks and increased threats facing government and critical infrastructure businesses, cybersecurity training within the federal government sector has never been more in-demand. Additionally, […]
 EC-Council, a leading cybersecurity certification body, collaborates with the Institute of Chartered IT Professionals (ICITP-SA) of South Africa to promote critical cybersecurity skills that align with IT and security business needs. South Africa, 15 November 2021: ICITP, a professional body recognised by the South African Information and Communications Technology (ICT) sector, announces a partnership with EC-Council to foster the growth […]
EC-Council, a leading cybersecurity certification body, collaborates with the Institute of Chartered IT Professionals (ICITP-SA) of South Africa to promote critical cybersecurity skills that align with IT and security business needs. South Africa, 15 November 2021: ICITP, a professional body recognised by the South African Information and Communications Technology (ICT) sector, announces a partnership with EC-Council to foster the growth […]
 FutureLearn division is proud to announce its partnership with EC-Council’s CodeRed to promote cyber security learning. With FutureLearn being one of the world’s largest providers of online courses and degrees, the partnership will bring EC-Council’s expertise in cyber security to over 16 million learners, and provide a much needed resource for the growing shortage of cyber security talent. The first […]
FutureLearn division is proud to announce its partnership with EC-Council’s CodeRed to promote cyber security learning. With FutureLearn being one of the world’s largest providers of online courses and degrees, the partnership will bring EC-Council’s expertise in cyber security to over 16 million learners, and provide a much needed resource for the growing shortage of cyber security talent. The first […]
 The Ministry of Communication and Informatics Indonesia collaborates with EC-Council, the leading global training certification body, to facilitate training in various cybersecurity domains under the Digital Talent Scholarship Program 2021. Jakarta, Indonesia, October 4th, 2021: To address the growing digital skills gap, Indonesia’s Ministry of Communication and Informatics has partnered with EC-Council to offer 1000 student scholarships for cybersecurity training […]
The Ministry of Communication and Informatics Indonesia collaborates with EC-Council, the leading global training certification body, to facilitate training in various cybersecurity domains under the Digital Talent Scholarship Program 2021. Jakarta, Indonesia, October 4th, 2021: To address the growing digital skills gap, Indonesia’s Ministry of Communication and Informatics has partnered with EC-Council to offer 1000 student scholarships for cybersecurity training […]