September 22, 2021 || Reading Time: 7 minutes || Artificial Intelligence has now been incorporated in various fields with vast development and implementation, which have been proven to be of great benefit. Artificial Intelligence, also known as AI, is the stimulation of human intelligence in machines.

They are programmed meticulously to think like human beings and replicate their activities. The main objective of an AI simulated machine is to achieve and perform all the activities done by a human being. Unlike human beings, AI machines are not forgetful as they are built with colossal storage to record all the required data. They never get tired, run on processers, and finish a specific task much faster than a human being. With the benefits it comes with, AI has now gained popularity and has been accepted into various sectors like the food industry as waiters and chefs, organizations to calculate and work on special projects, healthcare organizations to analyze and programmed to treat patients as well as perform operations and especially in the cybersecurity sector in training data modules to learn how to react to various situations and detecting anomalies/threats and risk based on patterns generated, vulnerability assessments, etc.
AI has been proven to be beneficial in cybersecurity and has many advantages when detecting vulnerabilities and managing them. AI techniques and machine learning can be a great combination to resolve cyber-related threats, risks, and attacks, especially in vulnerability management to prevent attacks beforehand.
Defining AI and Vulnerability Assessment
AI is a blanket term consisting of numerous advanced computer science areas ranging from voice detection to typical language processing, robotics, and deep representational learning. Scientists and researchers aim to automate intelligent behavior in machines that are capable of doing human tasks. Artificial Intelligence scientists and technologists are continuously seeking various methodologies to automate “intelligent” behavior. A single AI component used expansively in several applications is machine learning — the algorithms that support historical data/information to forecast or make decisions about a particular action. More extensive the historical data, the machine learning’s decision-making capabilities improve and make better and accurate predictions about situations or circumstances and are termed as getting smarter. It advances with time and without human interference.
Vulnerability assessment is defined as the systematic review of security weaknesses in a system or network. It assesses if the system is prone to any known vulnerabilities. If yes, it assigns severity levels to those vulnerabilities and suggests mitigation methods. The scanning process to identify vulnerabilities and resolve them are categorized into the following steps:
- Vulnerability Identification
- Analysis
- Risk Assessments
- Remediation
Development of a Significant Vulnerability Risk Score
The vulnerability score is significantly similar to the risk score attached to the vulnerabilities in the Critical Vulnerabilities and Exposures [CVE] program. The CVE comprises a list of records/data which contains a unique identification number. The unique identification number is used to identify, define, and catalog the vulnerabilities, which are publicly disclosed. It can also be incorporated into the products and services as per the terms of use. Though CVE is useful in determining the vulnerability and its possible risk severity, it lacks context, making it difficult to rationalize certain aspects. A vulnerability may be assigned a high-risk score but, on the specific network, the affected place may be secluded on a secured subnet, or not connected to the internet, or maybe on a device or program which has no operations or services, resulting in little or no risk to the organization. The CVE is excellent to kickstart for context-based risk analysis. Once the asset/device context is attained, it is combined with the knowledge and external threat environment, generating the context-driven priority that is accurate. This can be used to determine the vulnerability severity or the importance of the vulnerability risk/threats.
Vulnerability Exploitation: The Latest Trends
Various brand marketers use Artificial Intelligence-based analyses to assess the posts of their products or services on different social media platforms. The result enables the brand marketing employees to understand how the public perceives their products and how it changes and how it has changed over a period of time. This is achieved by AI application, and the data is collected over time and compared to decide what is lacking and what should be improved. Similarly, cybersecurity chat boards and other online sources of cybersecurity information and interaction can be collected and analyzed. This analysis is done by AI technology, which can identify the vulnerability that is exploited chiefly based on the data collected. The technology used to analyze the data collected from multiple interactions, polls, and other information is the Neural Networks and Natural Language Processing (NLP) techniques. The NLP technique can recognize the exact meaning, positive and negative traits, accurate technical information from the transcript. AI is responsible for interpreting vast amounts of data and merging their meanings to gain context for the risks of the given vulnerabilities.
Asset Detection
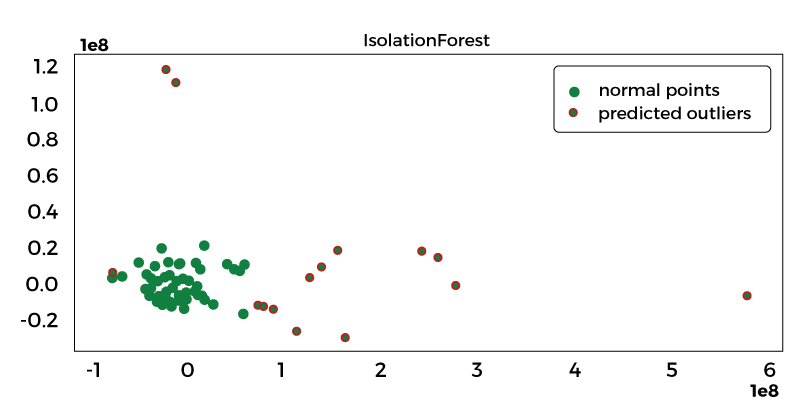
It is relatively important to detect all the assets/devices for an effective vulnerability assessment, especially those atypical/uncategorized in a given context. Conventional methods are not efficient to detect uncategorized information/data/assets, such as a Linux server in windows machine with database services. These types of conditions require at-most priority from security teams. Pattern recognition, Artificial Intelligence techniques are implemented to identify and distinguish uncategorized/unique assets. Novelty, Anomaly Detection, or outlier detection methods/algorithms are enforced to identify uncategorized assets. The most known effective algorithm is the Isolation Forest, where numerous multidimensional representations are used to compare the characteristics of the assets/devices. The uncategorized assets are detected and flagged for identification purposes.
Detection Reliability Assessment
It is crucial to determine whether a vulnerability is exploitable or not as the process of vulnerability detection involves a high range of false positives. Artificial Intelligence methods and techniques can be implemented in detecting the vulnerabilities, which significantly reduces the number of false-positive outcomes by detecting the misdetections. Various services like services running and others, and the vulnerability which was flagged as a result of the detection method, are used to confirm the legitimacy of the identified vulnerability. With experience, the ability of Artificial Intelligence machines can accurately detect false positives from legit vulnerabilities.
Bayesian Networks are used to improve the reliability of vulnerability detection, to determine if the vulnerability is legit or not. The technique includes other observations as pieces of evidence in the assessment procedure. Bayesian networks are far more efficient and effective and, when implied, promote intelligence analysis which results in balancing the defective scanning techniques with the help of proficient human knowledge.
Leveraging Industry Vulnerability Remediation Priority Data
Every contemporary vulnerability assessment product has cloud-based components in them, and some are completely cloud-based. Cloud-based vulnerability assessment/management platforms are extremely beneficial. One of the most important benefits is the anonymization of user data which can be reduced and discarded from the applications. Every single organization is regularly remediating vulnerabilities daily. Several remediation procedures over several customers are performed, and cloud-based vulnerability assessment products have a rich data source on which AI engine can be used. The source undergoes constant changes due to various factors and collects data. This can either strengthen or contradict the conventional remediation methods of vulnerability prioritization. Artificial Intelligence can be applied to actual vulnerability remediation data, resulting in yielding insights based on various sources’ shared judgments. Gradient Boosted Tree Regression is a machine learning technique that, when combined with user behavioral patterns and preferences, results in predicting what is essential, which helps understand and remediate vulnerabilities.
Gradient Boosted Tree Regression
Remediation Plan Recommendations
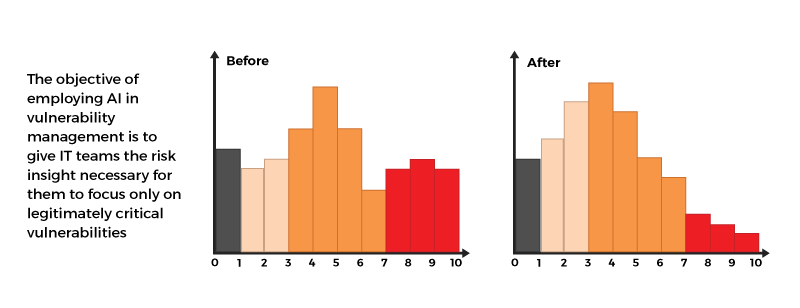
A list of vulnerabilities is entrenched based on a context that is achieved using AI techniques. Enhancing and focused on delivering solutions is the last step in the vulnerability assessment procedure. AI has a major role in achieving the necessary solutions based on vast programs and algorithms used to differentiate anomalies, threats, risks, etc. Artificial Intelligence techniques speed up the detection process and provide a solution in a lesser period, maximizing the risk reduction while still minimizing remediation activity. Risk-Aware Recommender System is a hybrid between collaborative filtering and content-based systems, resulting in multiple remediation situations. The vulnerability management Recommender System considers the risk degradation that the remediation situations can afford with the help of the AI-generated risk scores.
Many progressions have been made in the field of cybersecurity with the help of various AI techniques. There is lesser human interference with AI machines and techniques, resulting in greater accuracy of the results, and it is a fast process. With the increase in the complexity range and other risk factors, it can help take off the load from the conventional vulnerability management team and efficiently store data and detect situations detected long ago.
AI can be very useful in the field of cybersecurity. It is fast and can predict and identify potential threats, risks, and vulnerabilities present in the system. It is also responsible for mitigating the risk factors and obtaining a feasible solution. Though AI provides solutions, the security team needs to practice privacy enhancement methods, which is crucial in developing and implementing security habits that can help individuals take preventive measures beforehand in all aspects. One can learn how to imply the AI techniques and methodologies in the cybersecurity field by pursuing ethical hacking essential to understand the vulnerability assessment procedures and vulnerability assessment tools required to mitigate potentially exploitable vulnerabilities. One such top ethical hacking certification course is the EC-Council’s Certified Ethical Hacker (CEH) Certification which provides in-depth knowledge about the role of a hacker and other components which is essential to maintain the security of the cyber environment and provides ethical hacking training that is, practical – hands-on problems to train the individual to deal with real-world problems.
Certified Ethical Hacker is one such course that enables an individual to learn about the role of AI and how it is implemented in cybersecurity to reduce and mitigate risks, vulnerabilities, and other factors.
Recognized and Accredited by US Federal Agencies, FBI, and NSA.
Start your CEH certification and explore new career opportunities. Apply today.
FAQs
The post How Artificial Intelligence Is Favorable to Modernize the Methods Used for Vulnerability Assessments appeared first on EC-Council Official Blog.
Article posted by: https://www.eccouncil.org/
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com
This is the article generated by feed coming from KaliLinux.in and Infocerts is only displaying the content.