March 11, 2024
Organizations face an ever-changing digital landscape, which often results in new security risks. Cyberthreats continue to plague both governments and businesses around the world, highlighting the need for security professionals and leaders who can supply the skills and leadership to combat them.
As the world of information security evolves, so must the skills of those tasked with protecting online data and other digital assets. Chief information security officers (CISOs), who play a vital role in information security management, must possess a unique blend of leadership strength and technical ability.
CISOs must stay up to date with the latest trends and technologies to effectively handle security risks and incidents—a daunting task in light of the fast-moving tech landscape. To add to the challenge, many CISOs are also responsible for managing multiple teams and large security budgets.
Given that attack vectors and tactics are becoming increasingly sophisticated, information security leaders must ensure that they have the necessary skills to confront these challenges.
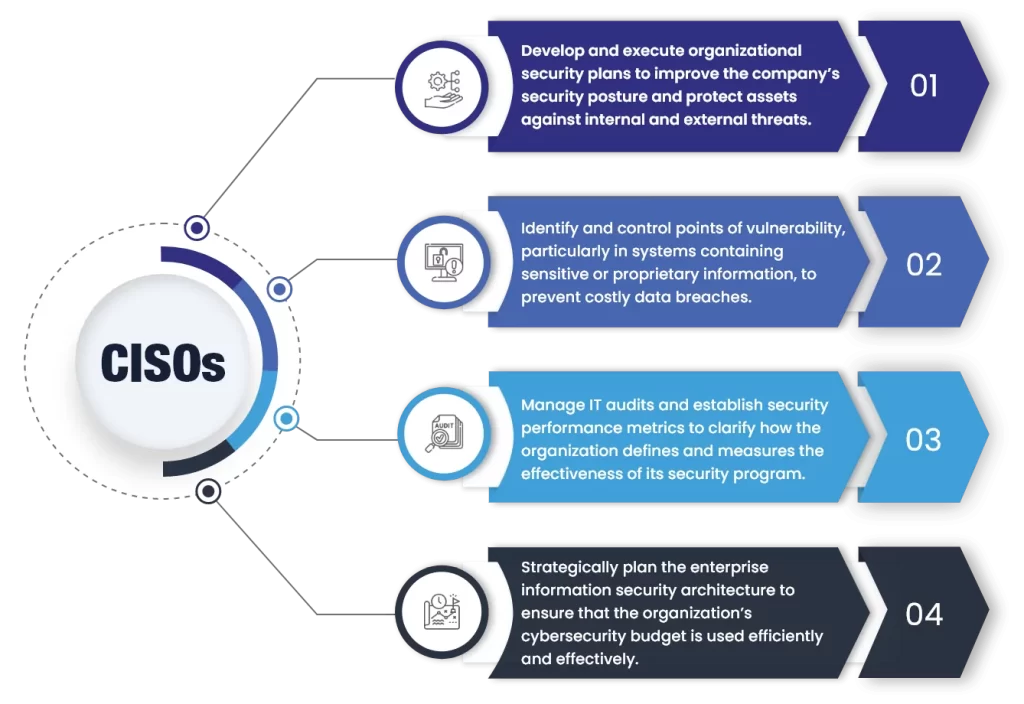
The following infographic sheds light on four core competencies for CISOs
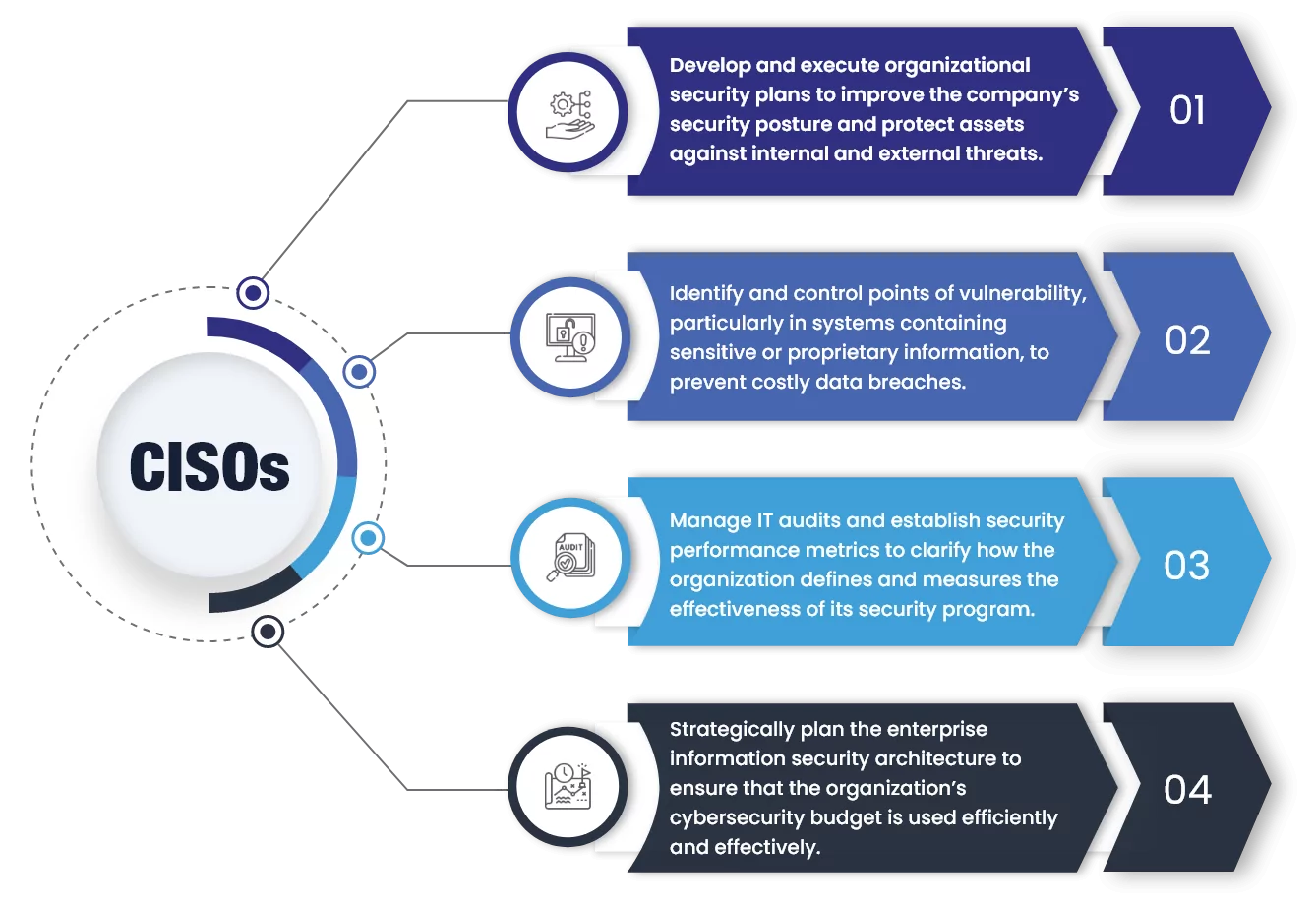
Core Skills for Today’s CISOs
01
Develop and Execute Organizational Security Plans
A sound security strategy is indispensable in protecting an organization against hacking, intrusion, and data theft. CISOs play a critical role in creating this strategy. A CISO is tasked with regularly assessing an organization’s security posture, helping to ensure that the organization is prepared to counter any threats that could appear. This is a significant undertaking, as security posture encompasses the overall security status of an entire company’s networks, software, and hardware. CISOs play a significant role in designing and implementing an organization’s security strategy, considering all aspects of data security. This includes creating security policies to minimize potential threats and vulnerabilities, coordinating compliance and certification requirements, managing security teams, and overseeing various security-related initiatives.
Security policies should include definitions of roles, responsibilities, and standards with corresponding accountability. It should describe the duties of various individuals and groups who would be involved in the response to a security incident, such as network administrators, security officers, and auditors. A security policy should also identify approved data handling and dissemination procedures and provide a means for periodic review of these procedures. A security policy is a guide that an organization follows to keep its information assets safe from internal and external threats. For example, a security policy could specify that all data on portable computing devices must be encrypted, including the levels of encryption that must be used, how they are to be applied, and the devices affected (e.g., all laptops, hard drives, mobile devices, and any storage devices connected to the organization’s computers).
02
Identify and Control Points of Vulnerability
03
Manage IT Audits and Establish Security Performance Metrics
Example Measures of Effectiveness*
- Number of security policies properly documented and in use
- Percentage of security incidents reported within required timeframe
- Percentage of security vulnerabilities that have been patched
Example Measures of Efficiency*
- Percentage of discovered vulnerabilities mitigated within target timeframe
- Frequency of audit reviews and analyses
- Percentage of system components that undergo maintenance on schedule
04
Strategically Plan the Enterprise Information Security Architecture
How Can You Become a Successful CISO?
If you want to move into a position of greater responsibility and authority in an organization by becoming a CISO, you’ll need strong skills in both cybersecurity and management. The role of a CISO or information security leader goes beyond standard cybersecurity tasks: CISOs also must have a broad understanding of an organization’s operations and vision and possess the strong management skills to successfully lead an organization’s information security efforts.
To meet the increasingly complex security demands faced by organizations today, cybersecurity leaders need to continually invest in themselves and stay up to date on the latest industry trends, knowledge, and skills. EC-Council’s Certified Chief Information Security Officer (C|CISO) program has been designed to bridge the gap between the executive management knowledge that CISOs require and the technical competencies that many aspiring CISOs have.
EC-Council’s C|CISO course is an industry-leading program that recognizes that real-world experience is crucial in developing and maintaining a successful information security program. The certification confirms an individual’s ability to provide strategic leadership and direction, manage enterprise-wide information security programs, and protect critical information assets.
If you are interested in learning more about the C|CISO certification, visit the C|CISO program site at https://ciso.eccouncil.org. The C|CISO website is a valuable resource for learning more about the C|CISO certification and the cybersecurity industry.
The post Essential Information Security Management Skills CISOS appeared first on Cybersecurity Exchange.
Article posted by: https://www.eccouncil.org/cybersecurity-exchange/cybersecurity/essential-information-security-management-skills-cisos/
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com
This is the article generated by feed coming from KaliLinux.in and Infocerts is only displaying the content.