March 30, 2023
CHFI v10 Practice Test (Full 600+ Questions)
https://www.udemy.com/course/chfi-v10-certmaster-exam-prep/?referralCode=79DFFB9D994A3B22461A
140. Matthew has been assigned the task of analyzing a suspicious MS Office document via static analysis over an Ubuntu-based forensic machine. He wants to see what type of document it is, whether it is encrypted, or contains any flash objects/VBA macros. Which of the following python-based script should he run to get relevant information?
oledir.py
oleid.py
oleform.py
pdfid.py
Matthew should run the “oleid.py” script to get relevant information about the suspicious MS Office document via static analysis on an Ubuntu-based forensic machine. oleid.py is a Python-based script that can analyze Microsoft Office documents to determine the type of document, whether it is encrypted, and whether it contains any flash objects or VBA macros. The script can be used to extract information from MS Office documents without executing any macros or other code, making it a useful tool for forensic analysis and incident response. By using oleid.py, Matthew can quickly gather information about the suspicious document and determine if it contains any potential indicators of compromise or other security risks.
Static analysis is a method of analyzing a file or artifact without executing it, which is often used in digital forensics and incident response to gather information about a suspicious file. In the case of a suspicious MS Office document, static analysis can be used to determine the type of document, whether it is encrypted, and whether it contains any flash objects or VBA macros.
The “oleid.py” script is a Python-based tool that can be used to perform static analysis of MS Office documents. The script is specifically designed to analyze Office documents and extract information about their structure and contents. When run against a suspicious MS Office document, oleid.py will provide information such as the type of document, whether it is encrypted, and whether it contains any flash objects or VBA macros. This information can be used to determine if the document contains any potential indicators of compromise or other security risks, and to make decisions about how to handle the document.
By using oleid.py, Matthew can quickly and easily gather information about the suspicious MS Office document without executing any code or macros that may be present in the document. This makes oleid.py a useful tool for forensic analysis and incident response, as it allows investigators to gather information about a suspicious file in a safe and controlled manner.
141. You are a digital forensic investigator at a large pharmaceutical company. You are responding to a security incident where you have found a computer on the scene, and you believe the computer contains evidence that is valuable to the case. The computer is running, but the screen is blank. What should you do first?
Gather the appropriate report forms, pens, and memory capture tools
Move the mouse slightly to wake the computer up
Unplug the computer
Press a single key on the keyboard, and document which key was pressed
The first thing you should do as a digital forensic investigator in this scenario is to unplug the computer. When responding to a security incident involving a live computer, it is important to preserve the evidence by preventing any further changes to the system. By unplugging the computer, you prevent any activity from occurring on the system and ensure that the evidence remains in its current state.
Once the computer has been unplugged, you can then gather the appropriate report forms, pens, and memory capture tools. You may also want to document the state of the computer at the time it was unplugged, including the time and date, the state of the screen, and any other relevant information.
It is generally not recommended to move the mouse or press a single key on the keyboard, as this may cause the system to perform some actions that could modify the evidence. Instead, the priority should be to preserve the evidence and prevent any further changes to the system.
142. Edgar is part of the FBI’s forensic media and malware analysis team; he is analyzing a current malware and is conducting a thorough examination of the suspect system, network, and other connected devices. Edgar’s approach is to execute the malware code to know how it interacts with the host system and its impacts on it. He is also using a virtual machine and a sandbox environment.
What type of malware analysis is Edgar performing?
Dynamic malware analysis/behavioral analysis
Static analysis
Malware disassembly
VirusTotal analysis
Edgar is performing dynamic malware analysis, also known as behavioral analysis. This type of analysis involves executing the malware code in a controlled environment, such as a virtual machine or a sandbox, to observe its behavior and understand how it interacts with the host system and its impacts on it. By executing the malware code, the analyst can gather information about its functionality, including how it spreads, what files it modifies or creates, and what network traffic it generates.
Dynamic malware analysis is different from static analysis, which involves analyzing the code of a malware sample without executing it. Malware disassembly is a technique used to reverse engineer malware code, while VirusTotal analysis involves uploading a malware sample to a public malware scanning service to obtain information about its detection rate and behavior.
By using a virtual machine and a sandbox environment, Edgar is able to safely and effectively execute the malware code without risking contamination of his own system or network. This allows him to gather valuable information about the malware’s behavior, which can be used to develop countermeasures and prevent future attacks.
143. Amber, a black hat hacker, has embedded a malware into a small enticing advertisement and posted it on a popular ad-network that displays across various websites. What is she doing?
Malvertising
Spear phishing
Compromising a legitimate site
Click-jacking

Amber is conducting an attack known as “malvertising.” Malvertising is the practice of embedding malicious code into online advertisements and distributing them through ad networks. When users click on the advertisement, the malware is delivered to their device and can compromise their system. This type of attack is particularly effective because it can reach a large number of users through a seemingly legitimate and trustworthy source, the ad network. The malicious code can be used to steal sensitive information, install additional malware, or even launch further attacks.
Spear phishing is a targeted form of phishing that targets specific individuals or organizations with personalized emails designed to trick the recipient into revealing sensitive information or downloading malware. Compromising a legitimate site involves hacking into a legitimate website and using it to distribute malware or launch attacks, while click-jacking involves tricking users into clicking on a button or link that appears to be for one thing but actually performs another action, such as installing malware.
144. You are a forensic investigator who is analyzing a hard drive that was recently collected as evidence. You have been unsuccessful at locating any meaningful evidence within the file system and suspect a drive wiping utility may have been used. You have reviewed the keys within the software hive of the Windows registry and did not find any drive wiping utilities. How can you verify that drive wiping software was used on the hard drive?
Load various drive wiping utilities offline, and export previous run reports
Document in your report that you suspect a drive wiping utility was used, but no evidence was found , chốt đáp án này
Check the list of installed programs
Look for distinct repeating patterns on the hard drive at the bit level
The correct answer is: Document in your report that you suspect a drive wiping utility was used, but no evidence was found.
Drive wiping utilities are designed to erase data from a hard drive, making it nearly impossible to recover the original data. If a drive wiping utility has been used, it may not be possible to find any meaningful evidence within the file system or the registry keys. In this case, the best course of action is to document in the report that you suspect a drive wiping utility was used, but no evidence was found to support this suspicion.
Exporting previous run reports from drive wiping utilities would only be useful if the utility was installed and run on the hard drive in question. Checking the list of installed programs would not necessarily indicate if a drive wiping utility was used, as the utility could have been run from a bootable CD or USB drive, rather than being installed on the hard drive. Looking for repeating patterns at the bit level may provide some indication of whether the hard drive has been wiped, but this is a complex and time-consuming process that may not necessarily provide conclusive evidence.
And it’s also possible that the answer is : Looking for distinct repeating patterns on the hard drive at the bit level may provide some indication of whether the hard drive has been wiped. If a drive wiping utility has been used, it is likely that the hard drive would contain distinct repeating patterns, indicating that data has been overwritten multiple times. This method of analysis is complex and time-consuming, but it may provide conclusive evidence of the use of a drive wiping utility.
145. “To ensure that the digital evidence is collected, preserved, examined, or transferred in a manner safeguarding the accuracy and reliability of the evidence, law enforcement, and forensics organizations must establish and maintain an effective quality system” is a principle established by:
EC-Council
NCIS
SWGDE
NIST

This principle is established by the Scientific Working Group on Digital Evidence (SWGDE). The SWGDE is a professional organization that provides guidelines and best practices for digital evidence management in law enforcement and forensic organizations. By establishing and maintaining an effective quality system, the organization can ensure the accuracy and reliability of the digital evidence collected and processed, and minimize the risk of contamination or loss of evidence.
146. Choose the layer in iOS architecture that provides frameworks for iOS app development?
Core OS
Cocoa Touch
Media services
Core services
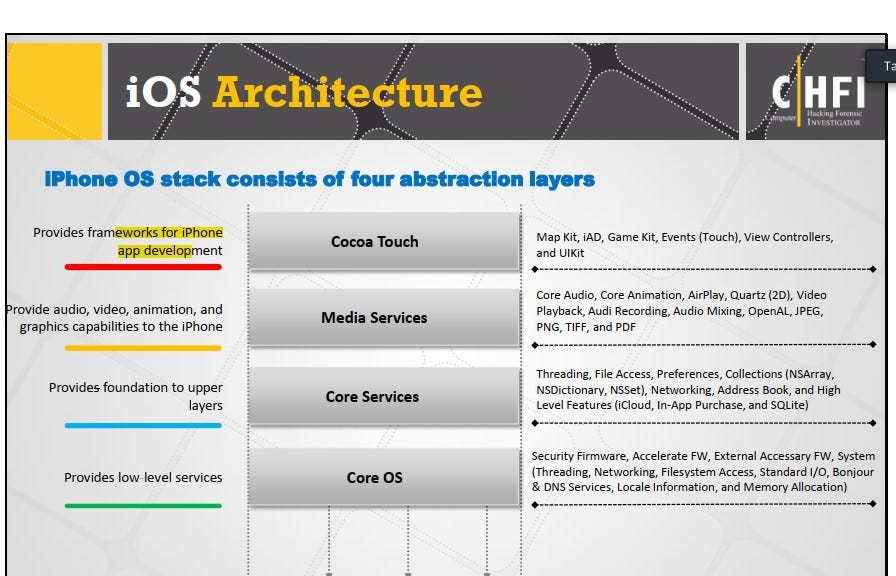
The layer in iOS architecture that provides frameworks for iOS app development is the Cocoa Touch layer. The Cocoa Touch layer is the top-level framework in the iOS architecture and is responsible for managing the user interface and user interaction with iOS applications. It provides a set of APIs and libraries for creating graphical user interfaces, managing touch and gesture-based interactions, and handling other user-related functionality. By using the Cocoa Touch framework, developers can create engaging and interactive iOS apps that are responsive to user input and provide a smooth user experience.
147. In which IoT attack does the attacker use multiple forged identities to create a strong illusion of traffic congestion, affecting communication between neighboring nodes and networks?
Jamming attack
Blueborne attack
Replay attack
Sybil attack

Sybil Attack: In a Sybil attack, an attacker creates multiple fake identities and uses them to deceive other nodes in a network. This type of attack is especially dangerous in IoT networks where the number of nodes is large, and the attack can create a strong illusion of traffic congestion, affecting communication between nodes and networks.
148. Which of the following statements is true with respect to SSDs (solid-state drives)?
Like HDDs, SSDs also have moving parts
Faster data access, lower power usage, and higher reliability are some of the major advantages of SSDs over HDDs
SSDs cannot store non-volatile data
SSDs contain tracks, clusters, and sectors to store data
1. Comparison between SSDs and HDDs: SSDs (Solid-State Drives) are a newer technology that has been designed to replace traditional HDDs (Hard Disk Drives). Unlike HDDs, SSDs do not have any moving parts, which makes them faster, more reliable, and consume less power. The main advantage of SSDs over HDDs is the faster data access time and lower power consumption. Unlike HDDs, SSDs do store non-volatile data and use flash memory to store data. They do not use the traditional method of storing data by tracks, clusters, and sectors.
149. Annie is searching for certain deleted files on a system running Windows XP OS. Where will she find the files if they were not completely deleted from the system?
C: $Recycled.Bin
C:RECYCLER ;
C:$Recycle.Bin
C:$RECYCLER
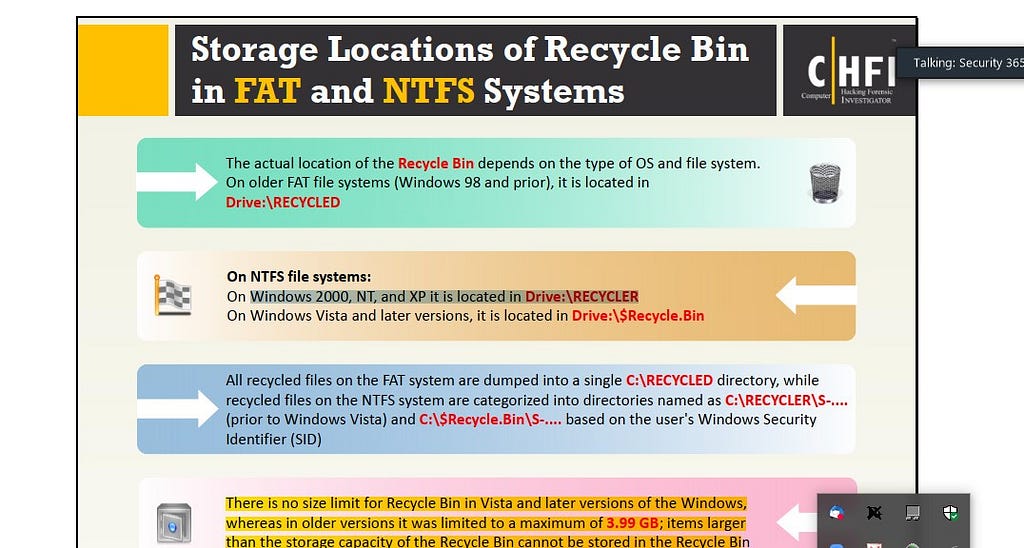
In Windows XP, deleted files can be found in the Recycle Bin folder, which is located at C:RECYCLER. The Recycle Bin folder is a special folder that holds deleted files and folders so that they can be easily restored if necessary. When a file is deleted from the system, it is moved to the Recycle Bin folder, and remains there until it is permanently deleted from the system, or until the Recycle Bin folder reaches its maximum size and starts overwriting older files.
150. Harry has collected a suspicious executable file from an infected system and seeks to reverse its machine code to instructions written in assembly language. Which tool should he use for this purpose?
Ollydbg
oledump
BinText
HashCalc
Harry should use a disassembler tool such as Ollydbg to reverse the machine code of the suspicious executable file into assembly language. A disassembler tool converts machine code, which is a series of binary instructions executed by the processor, into human-readable assembly language, which consists of mnemonics that represent the machine code instructions. This allows Harry to better understand how the executable file functions and whether it contains any malicious code.
………………………
…………………………………….
………………………………………………….
…………………………………………………………….
……………………………………………………………………….
…………………………………………………………………………………..
Article posted by: https://certmaster.me/chfi-v10-p4-91dfcce13c2?source=rss-d9e5f258a4e8——2
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com

