March 30, 2023
Let’s make a hot cup of coffee, and listen to the presentation.
………………………
………………………………..
………………………………………………..
CHFI v10 Practice Test (Full 600+ Questions)
https://www.udemy.com/course/chfi-v10-certmaster-exam-prep/?referralCode=79DFFB9D994A3B22461A
68. Cloud forensic investigations impose challenges related to multi-jurisdiction and multi-tenancy aspects. To have a better understanding of the roles and responsibilities between the cloud service provider (CSP) and the client, which document should the forensic investigator review?
National and local regulation
Service level agreement
Key performance indicator
Service level management
Service level agreement (SLA) is the document that a forensic investigator should review to have a better understanding of the roles and responsibilities between the cloud service provider (CSP) and the client in cloud forensic investigations. The SLA outlines the specific services and support that the CSP provides to its clients, such as data storage and retrieval, network connectivity, security, and privacy. It also sets out the responsibilities of each party in terms of maintenance and support, and any penalties or compensation in the event of service disruptions.
69. Maria has executed a suspicious executable file in a controlled environment and wants to see if the file adds/modifies any registry value after execution via Windows Event Viewer. Which of the following event ID should she look for in this scenario?
Event ID 4688
Event ID 4624
Event ID 4657
Event ID 7040
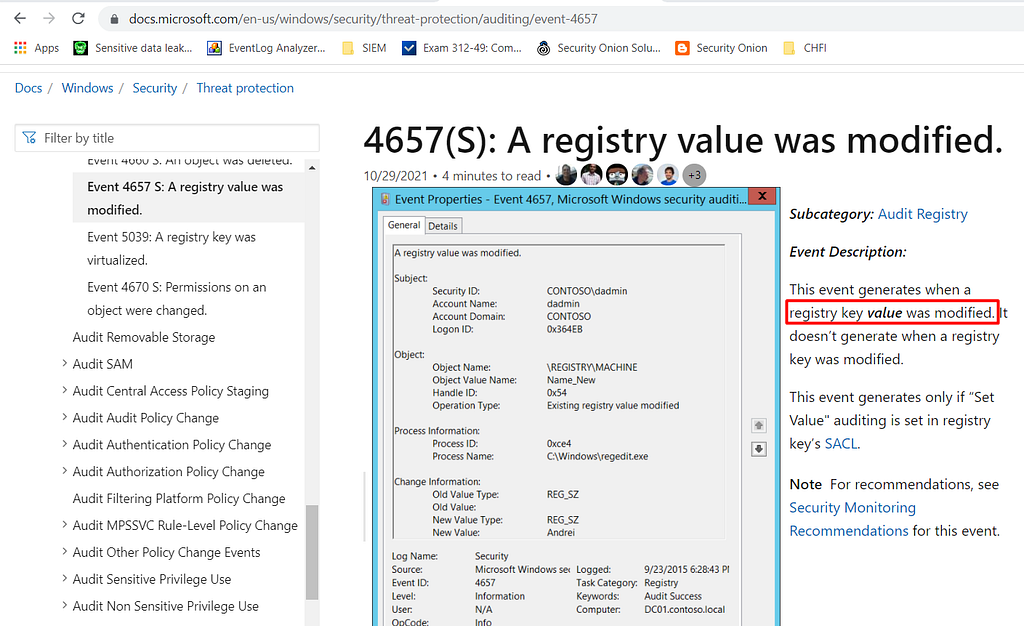
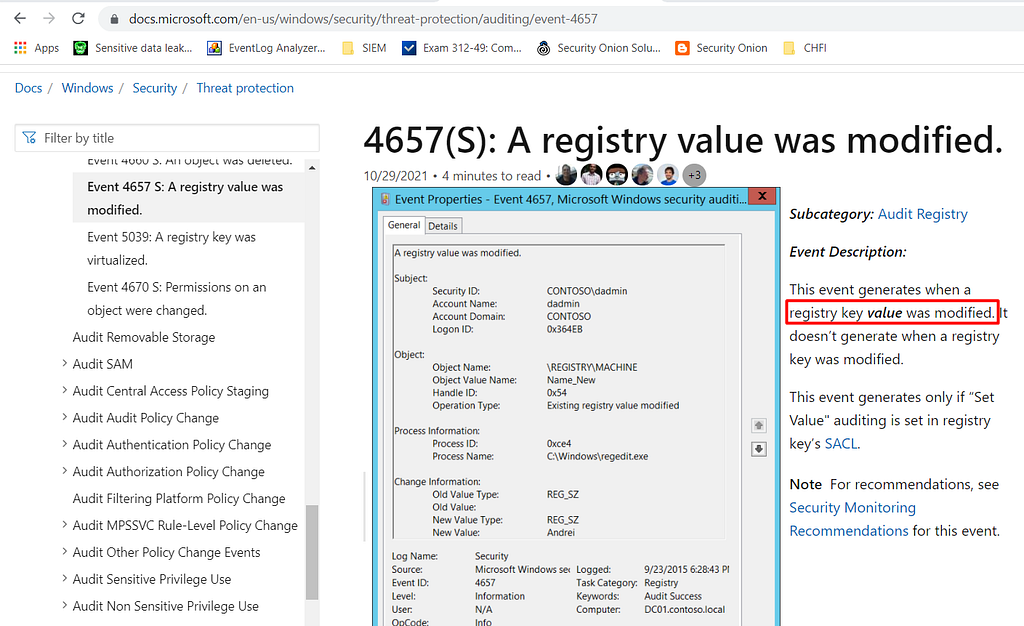
4657: A registry value was modified. This event documents creation, modification and deletion of registry VALUES. This event is logged between the open (4656) and close (4658) events for the registry KEY where the value resides. See Operation Type to find out if the value was created, modified or deleted.
70. Which layer in the IoT architecture is comprised of hardware parts such as sensors, RFID tags, and devices that play an important role in data collection?
Edge technology layer
Access gateway layer
Application layer
Middleware layer
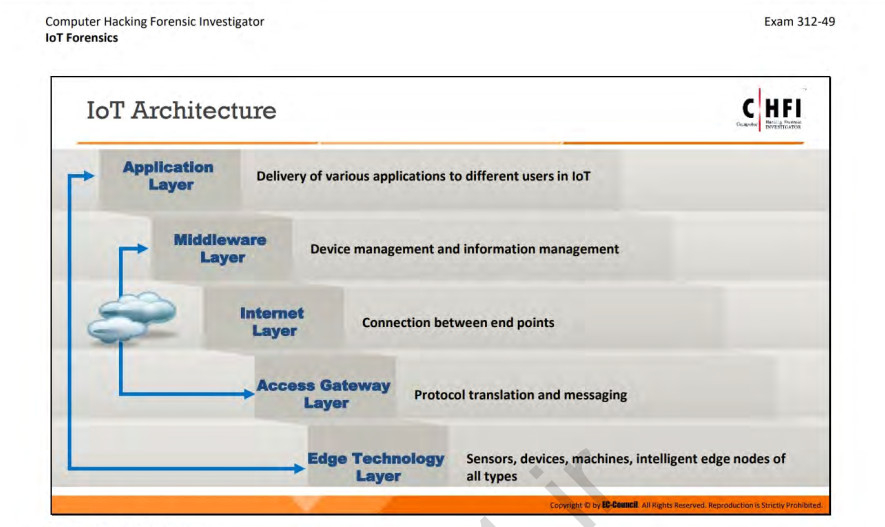
It ask about the layer in the Internet of Things (IoT) architecture that is comprised of hardware parts such as sensors, RFID tags, and devices that play an important role in data collection.
The answer is the Edge technology layer. The Edge technology layer refers to the layer in the IoT architecture that includes the physical devices and sensors that collect data. These devices are typically located at the edge of a network, near the source of the data being collected. They are responsible for collecting and transmitting data to other parts of the IoT system, such as the access gateway layer or the cloud.
In this layer, hardware components such as sensors, RFID tags, and other devices play a crucial role in data collection, as they are responsible for capturing the raw data from the environment. The data collected by these devices is then transmitted to other parts of the IoT system for further processing and analysis.
71. Williamson is a forensic investigator. While investigating a case of data breach at a company, he is maintaining a document that records details such as the forensic processes applied on the collected evidence, particulars of people handling it, the dates and times when it is being handled, and the place of storage of the evidence. What do you call this document?
Log book
Consent form
Chain of custody
Authorization form
Chain of custody Williamson is maintaining a document that records details such as the forensic processes applied on the collected evidence, particulars of people handling it, the dates and times when it is being handled, and the place of storage of the evidence. This document is known as the “chain of custody”.
72. BMP (Bitmap) is a standard file format for computers running the Windows OS. BMP images can range from black and white (1 bit per pixel) up to 24 bit color (16.7 million colors). Each bitmap file contains a header, the RGBQUAD array, information header, and image data. Which of the following element specifies the dimensions, compression type, and color format for the bitmap?
The RGBQUAD array
Header
Image data
Information header
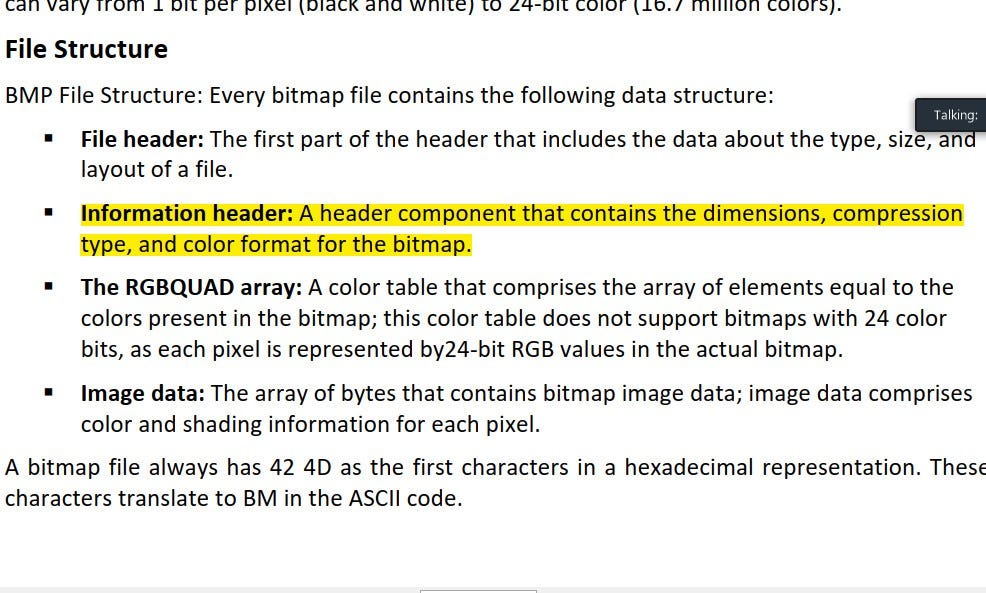
Information header : The information header in a BMP file specifies the dimensions, compression type, and color format for the bitmap.
73. Robert is a regional manager working in a reputed organization. One day, he suspected a malware attack after unwanted programs started popping up after logging into his computer. The network administrator was called upon to trace out any intrusion on the computer and he/she finds that suspicious activity has taken place within Autostart locations. In this situation, which of the following tools is used by the network administrator to detect any intrusion on a system?
Hex Editor
Process Monitor
Report Viewer
Internet Evidence Finder
Process Monitor : Process Monitor is a tool used by network administrators to detect any intrusion on a system by monitoring the activity of processes, file system, registry, and network operations.
74. You have been asked to investigate the possibility of computer fraud in the finance department of a company. It is suspected that a staff member has been committing finance fraud by printing cheques that have not been authorized. You have exhaustively searched all data files on a bitmap image of the target computer but have found no evidence. You suspect the files may not have been saved. What should you examine next in this case?
The registry
The Recycle Bin
The swap file
The metadata
The swap file is a possible place to examine next in this case. The swap file, also known as the paging file or page file, is a file on a hard drive that is used to store data temporarily when the RAM memory is full. This data can include data from applications that were running when the computer was turned off or shut down improperly, or data that has been deleted but not yet overwritten. As a result, the swap file can sometimes contain valuable information that can be useful in an investigation, so it’s worth examining as part of the investigation.
75. A file requires 10 KB space to be saved on a hard disk partition. An entire cluster of 32 KB has been allocated for this file. The remaining, unused space of 22 KB on this cluster will be identified as ________.
Cluster space
Sector space
Slack space
Swap space
In this case, you should examine the slack space or the unallocated space on the hard drive of the target computer. Slack space refers to the unused space in a cluster on a hard drive that occurs when a file is smaller than the cluster size. Slack space can contain remnants of deleted files, temporary files, and other data that can provide valuable information to an investigation. Since you have already searched all data files on the bitmap image of the target computer and found no evidence, examining the slack space might uncover hidden files or remnants of deleted files that could provide evidence of computer fraud.
76. During an investigation, the first responders stored mobile devices in specific containers to provide network isolation. All the following are examples of such pieces of equipment, except for:
Faraday bag
RF shield box
VirtualBox
VirtualBox is not a type of container used to provide network isolation during an investigation. VirtualBox is a type of software used for virtualization. Faraday bags, Signal Disruption Bags or Wireless StrongHold Bags, and RF-shielded boxes are examples of containers used to provide network isolation and prevent signals from reaching the mobile device, which may affect forensic evidence.
77. Jack is reviewing file headers to verify the file format and hopefully find more information of the file. After a careful review of the data chunks through a hex editor; Jack finds the binary value 0xffd8ff. Based on the above information, what type of format is the file/image saved as?
ASCII
GIF
BMP
JPEG
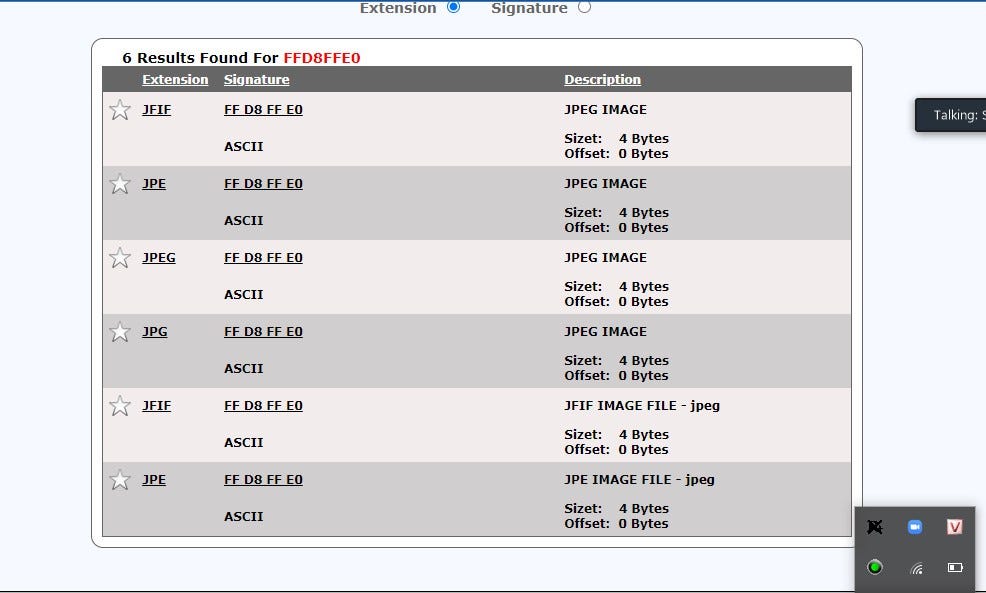
The file/image is saved in JPEG format. The binary value 0xffd8ff is the hexadecimal representation of the start of image (SOI) marker in JPEG files.
file header values for common file formats
JPEG (jpg), file header:ffd8ff
PNG (PNG), file header:89504E47
GIF (GIF), file header:47494638
TIFF (TIF), file header:49492a00
Windows Bitmap (BMP), file header:424D
CAD (DWG), file header:41433130
Adobe Photoshop (PSD), file header:38425053
78. Which “Standards and Criteria” under SWDGE states that “the agency must use hardware and software that are appropriate and effective for the seizure or examination procedure”?
Standards and Criteria 1.5
Standards and Criteria 1.7
Standards and Criteria 1.6
Standards and Criteria 1.4

The “Standards and Criteria” are a set of guidelines established by the Scientific Working Group on Digital Evidence (SWGDE), a non-profit organization that provides recommendations and best practices for digital evidence examination. The Standards and Criteria aim to provide guidelines for digital evidence collection, preservation, and analysis to ensure the validity and integrity of the evidence.
Standards and Criteria 1.5 specifically states that the agency responsible for the digital evidence examination must use hardware and software that are appropriate and effective for the seizure or examination procedure. This means that the agency must choose hardware and software that are suitable for the specific case and that will not compromise the evidence in any way. Additionally, the hardware and software must be able to produce accurate and reliable results. The objective of this criterion is to ensure that the digital evidence is handled in a way that maintains its integrity and that the results of the examination are trustworthy.
79. Before accessing digital evidence from victims, witnesses, or suspects, on their electronic devices, what should the investigator do first to respect legal privacy requirements?
Protect the device against external communication
Notify the fact to the local authority or employer
Obtain a formal written consent to search
Remove the battery or turn-off the device
CHFI v10 Practice Test (Full 600+ Questions)
https://www.udemy.com/course/chfi-v10-certmaster-exam-prep/?referralCode=79DFFB9D994A3B22461A
Article posted by: https://certmaster.me/chfi-v10-p3-9daa90f3070f?source=rss-d9e5f258a4e8——2
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com