Security Operations Center: The Nervous System of Cyber Defense
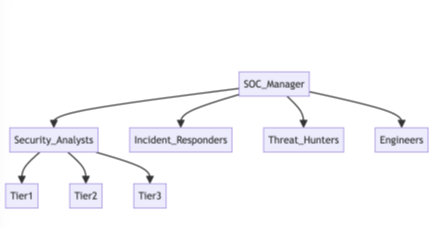
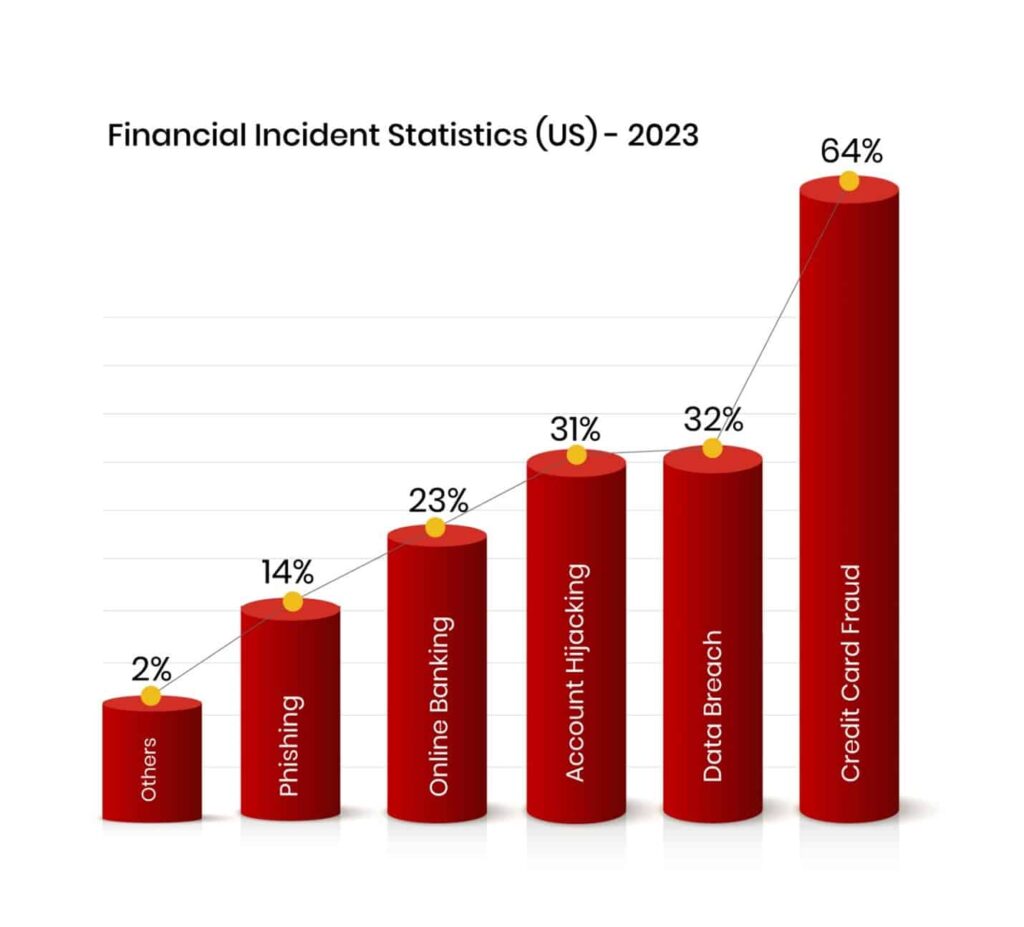
What is a Security Operations Center (SOC)? A Security Operations Center (SOC) is an exclusive security facility within an organization responsible for monitoring and responding to security incidents in a 24×7 format. The primary goal of a SOC is to detect, analyze, and respond to threats and security incidents using a combination of security tools, techniques,…
The post Security Operations Center: The Nervous System of Cyber Defense appeared first on Cybersecurity Exchange.