L3MON — Access Android Devices Remotely
In today’s detailed tutorial we learn how to install & configure L3MON on our Kali Linux system and use it. This l3MON tool has been archived by it’s owner. Seems it will not updated and may not work. We are also closing our support on this tools errors.
Using L3MON we can make an Android APK payload and send it to android device and after installing it on android device we can gain the access of Android device via L3MON’s web based interface, we can send commands from the easy web based interface and execute our commands on targeted devices.
L3mon have lots of beautiful features they are following:
- GPS Logging
- Microphone Recording
- View Contacts
- SMS Logs
- Send SMS
- Call Logs
- View Installed Apps
- View Stub Permissions
- Live Clipboard Logging
- Live Notification Logging
- View WiFi Networks (logs previously seen)
- File Explorer & Downloader
- Command Queuing
- Built In APK Builder
Installing L3MON in Kali Linux
We need Java Runtime Environment 8 and nodejs installed in our machine to run L3mon.
First we install the JRE (Java Runtime Environment) on our system by applying following command:
This command will install JRE version 8 on our system as shown in following screenshot:
 |
| We already have installed OpenJDK-8-JRE |
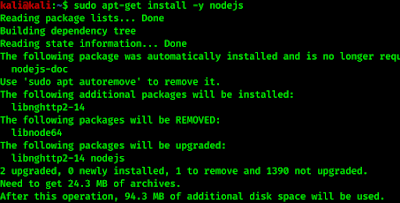
Then we need to install NodeJs on our system we apply the following commands to download nodejs in our system.
Then we run following command to install it.
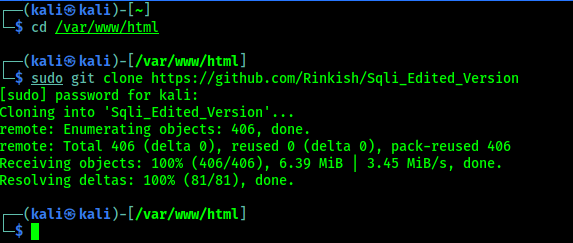
We download it from it’s GitHub by using git clone command:
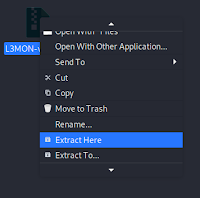
This command will download L3MON in our system. Now we create a new folder in our Desktop named L3MON and copy the downloaded zip file there.
Then extract it by right clicking on the zip file and choosing “extract here”.
Then we open a terminal window and navigate to L3MON in our Desktop by simply using cd command:
Here we install all the dependencies by using following command:
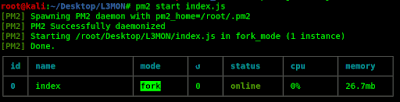
Let start the server by using following command:
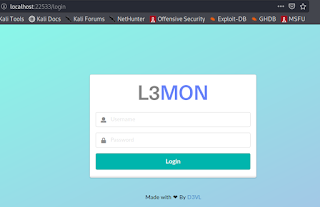
Now we can see our server in our browser http://localhost:22533 there will be a login page as following screenshot:
We create a login for our server here. But we cant login because we did not created a password to login. To create a password we stop our serve by using following command:
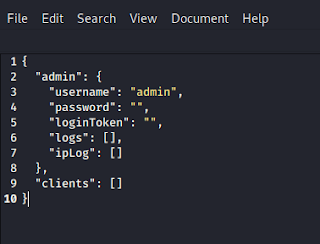
Now we need to edit maindb.json file using our favorite text editor mousepad.
Here we edit the username if we want it. But in the password field, we need to give our password’s md5 hash. Means if we fill here the password as plain text, will not work. We must need to put password’s md5 hash.
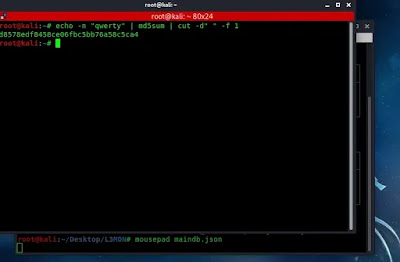
How to create a md5 hash of a password? Suppose our password is qwerty (This is for an example we shouldn’t choose easy passwords for security reasons). To convert it on md5 we need to use following command in another terminal window.
Here we got the MD5 hash of our password as we can see in the following screenshot.
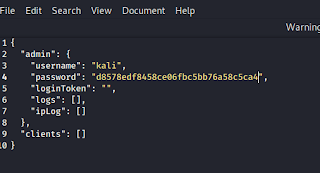
Then we fill our username and password in maindb.json file then save and close this file.
Now we again start the server by using following command :
Then again open our localhost in browser with 22533 port.
As we set our username kali and password qwerty we fill it and click on login.
We are successfully logged in.
Now we are in control. We need to open the APK builder tab.
Here we put our IP address (local or public) and leave the port as default and click on build.
Note: If we want to control android device on our local network (same WiFi) then we can use our local IP and to connect devices through internet we need to put our Public IP (Static IP is preferred for a long time use).
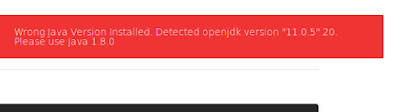
After clicking on build we got an error like this.
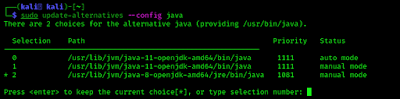
We solved this error by configuring JAVA in another terminal by running following command:
Here we can select Java versions. We need Java version 8 to run L3MON tool. In out case it is on number 2, as we can see in the following screenshot.
Then we restart our running L3MON server by using following command:
Bingo, the error goes now the build is ready to download.
Now we can download the L3MON.apk in our system, and send it to our targeted device anyway and make a successful installation.
After a successful installation it on targeted device and the phone user tries to open this L3MON will asks all the permission of devices and automatically hide itself from the app drawer.
After this we got the connection with the device. We can check it on our Devices tab.
Now we can control this phone from the manage button. Here in the following screenshot we are in the file manager of the phone. Now we can spy on this phone.
 |
| We are in the file manager of victim device |
Our downloaded data and recorded audio clips will be saved under assets/webpublic/client_downloads/ directory.
Our discussed method is for local network. To connect a device from internet we prefer to have a static IP address and forward our default port 22533 in our router settings or we can change the default port by changing these lines (inside includes/const.js).
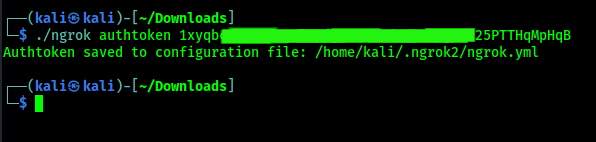
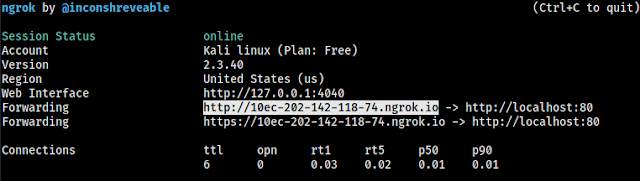
Using this method we can control phones connected in our same network. We also can control devices through internet by using ngrok services. Configuring L3MON on VPS will make it portable and useful.
Disclaimer
Provides no warranty with this software and will not be responsible for any direct or indirect damage caused due to the usage of this tool or this tutorial.
L3MON is built and our article is documented for both Educational and Internal use ONLY.
Getting any problem during installing or configuring L3MON ? This l3MON tool has been archived by it’s owner. Seems it will not updated and may not work. We are also closing our comment support on this tool’s errors. For more tutorials like this subscribe our newsletter to get updated. Also we post updates on our Twitter and GitHub.

































![How to Stay Anonymous Completely [100% Perfect] How to Stay Anonymous Completely [100% Perfect]](https://infocerts.com/wp-content/uploads/2021/09/How-to-Stay-Anonymous-Completely-100-Perfect-infocerts.jpg)