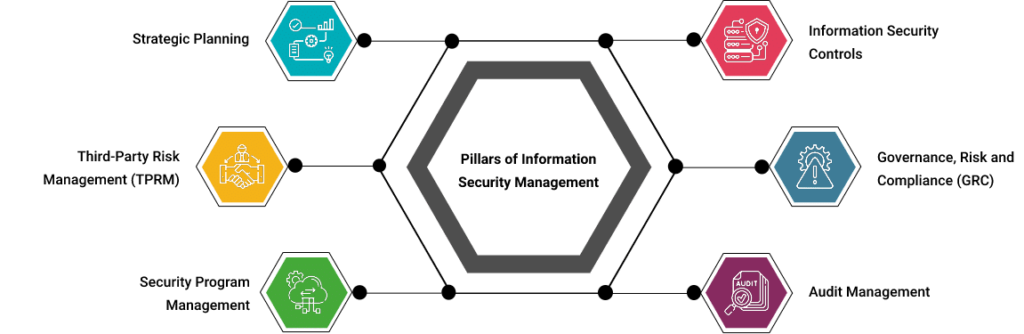
What is Information Security Management
Information security management is an organization’s approach to ensure the confidentiality, availability, and integrity of IT assets and safeguard them from cyberattacks. A Chief Information Security Officer, IT Operations Manager, or Chief Technical Officer, whose team comprises Security Analysts and IT Operators, may carry out the tasks involved in information security. It’s obvious that virtually…
The post What is Information Security Management appeared first on Cybersecurity Exchange.