Find Vulnerabilities using NMAP Scripts (NSE)
Nmap comes pre-installed with Kali Linux. Not just Kali Linux Nmap comes pre-installed with every security focused operating system. We have already discussed how to use Nmap for active reconnaissance in our previous article “NMAP — The Network Mapper“.
But cybersecurity experts don’t just use Nmap for scanning ports and services running on the target system, Nmap also can be used for vulnerability assessment and much more using NSE (Nmap Scripting Engine).
The Nmap Scripting Engine (NSE) has revolutionized the possibilities of a port scanner by allowing users to write scripts that perform custom tasks using the host information collected by Nmap. As of September 2021, when we are writing this article, Nmap has over 600+ scripts on Nmap version 7.91.
Penetration testers uses Nmap’s most powerful and flexible features, which allows them to to write their own scripts and automate various tasks. NSE (Nmap Scripting Engine) was developed for following reasons:
- Network Discovery:- This is the primary purpose that most of the people utilize Nmap for network port discovery, which we had learned in our “Nmap – The Network Mapper” article.
- Classier version detection of a service:- There are tons of services with multiple version details for the same service, so Nmap makes it more easy to identify the service.
- Backdoor detection:- Some of the Nmap scripts are written to identify the pattern of backdoors. If there are any worms or malicious program infecting the network, it makes the attacker’s job easy to short down and focus on taking over the machine remotely.
- Vulnerability Scanning:- Pen testers also uses Nmap for exploitation in combination with other tools such as Metasploit or write a custom reverse shell code and combine Nmap’s capability with them for exploitation.
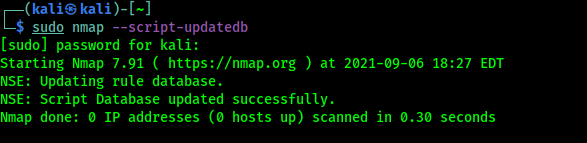
Before jumping in to finding vulnerabilities using Nmap we must need to update the database of scripts, so newer scripts will be added on our database. Then we are ready to scan for vulnerabilities with all Nmap scripts. To update the Nmap scripts database we need to apply following command on our terminal window:
In the following screenshot we can see that we have an updated Nmap scripts database.
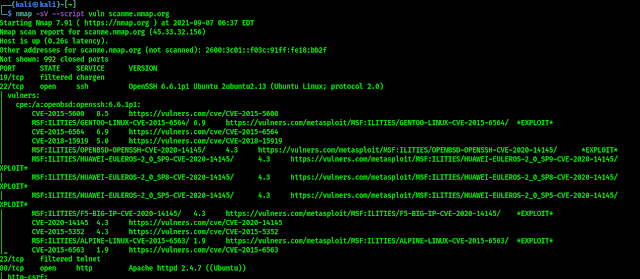
Now we are ready to scan any target for vulnerabilities. Well we can use following command to run all vulnerability scanning scripts against a target.
As we can see in the following screenshot:
When we are talking about Nmap Scripts then we need to know that, not only vulnerability scanning (vuln) there are lots of categories of Nmap scripts those are following:
- auth: This categorized scripts related to user authentication.
- broadcast: This is a very interesting category of scripts that use broadcast petitions to gather information.
- brute: This category is for scripts that help conduct brute-force password auditing.
- default: This category is for scripts that are executed when a script scan is executed ( -sC ).
- discovery: This category is for scripts related to host and service discovery.
- dos: This category is for scripts related to denial of service attacks.
- exploit: This category is for scripts that exploit security vulnerabilities.
- external: This category is for scripts that depend on a third-party service.
- fuzzer: This category is for Nmap scripts that are focused on fuzzing.
- intrusive: These scripts might crash system by generate lot of network noise, sysadmins considers it intrusive.
- malware: This category is for scripts related to malware detection.
- safe: This category is for scripts that are considered safe in all situations.
- version: This category is for NSE scripts that are used for advanced versioning.
- vuln: This category is for scripts related to security vulnerabilities.
So we can see that we can do various tasks using Nmap using Nmap Scripting Engine scripts. When we need to run all the scripts against single target we can use following command:
In the following screenshot we can see that all scripts are using against one target, but here every script will run so it will consume good amount of time.
That is all for this article. We will back again with Nmap. Hope this article helps our fellow Kali Linux users. Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.



 Dubai UAE, 30th August 2021 – The upsurge in the hybrid work culture augments the need for critical infrastructure and resource availability. Consequentially, security knowledge becomes a concern for firms with end-users handling and accessing sensitive information. In response to this, EC-Council and Saiber Innovation Technologies team up to raise cybersecurity awareness in the Middle East by assisting businesses to […]
Dubai UAE, 30th August 2021 – The upsurge in the hybrid work culture augments the need for critical infrastructure and resource availability. Consequentially, security knowledge becomes a concern for firms with end-users handling and accessing sensitive information. In response to this, EC-Council and Saiber Innovation Technologies team up to raise cybersecurity awareness in the Middle East by assisting businesses to […]
 Summary: The Scholarship aims to encourage skill-building and preparation for C|EH Practical Exams. The scholarship has also reserved 50% of its funds for women and neurodiverse individuals to increase diversity and representation.Albuquerque, NM, September 14, 2021 — EC-Council, a leader in cybersecurity certification and education programs, has announced the launch of the 2021 edition of the Certified Ethical Hacker (C|EH) […]
Summary: The Scholarship aims to encourage skill-building and preparation for C|EH Practical Exams. The scholarship has also reserved 50% of its funds for women and neurodiverse individuals to increase diversity and representation.Albuquerque, NM, September 14, 2021 — EC-Council, a leader in cybersecurity certification and education programs, has announced the launch of the 2021 edition of the Certified Ethical Hacker (C|EH) […]
 Summary: EC-Council’s Global Ethical Hacking Leaderboard for August was dominated by candidates from the U.S. Candidates from Asia made their mark on the leaderboard and showcased the growing popularity of Ethical Hacking in the region. Sep 08, 2021 Tampa, Fl : The Certified Ethical Hacker program has long been recognized as a benchmark of achievement for cybersecurity professionals, helping organizations combat cybercrimes. It has successfully changed the perception around ethical hacking from being a niche role to one […]
Summary: EC-Council’s Global Ethical Hacking Leaderboard for August was dominated by candidates from the U.S. Candidates from Asia made their mark on the leaderboard and showcased the growing popularity of Ethical Hacking in the region. Sep 08, 2021 Tampa, Fl : The Certified Ethical Hacker program has long been recognized as a benchmark of achievement for cybersecurity professionals, helping organizations combat cybercrimes. It has successfully changed the perception around ethical hacking from being a niche role to one […]
 Paris, Aug 26th 2021 EC-Council has expanded its highly successful Certified Secure Computer User (CSCU) program to French, specially tailored for the Francophone communities worldwide to promote greater awareness of computer security best practices. The translation was made possible through collaborative efforts with EC-Council’s official training partner, AdDo. Market data continue to demonstrate growth in the demand for certified cyber security training, with France ranking second in the EU and ninth globally. CSCU is one of EC- Council’s most popular programs. […]
Paris, Aug 26th 2021 EC-Council has expanded its highly successful Certified Secure Computer User (CSCU) program to French, specially tailored for the Francophone communities worldwide to promote greater awareness of computer security best practices. The translation was made possible through collaborative efforts with EC-Council’s official training partner, AdDo. Market data continue to demonstrate growth in the demand for certified cyber security training, with France ranking second in the EU and ninth globally. CSCU is one of EC- Council’s most popular programs. […]
 August 23, Hyderabad IN. The strategic partnership aims to assist organizations in the Middle East and Africa (MEA) region to combat cyberthreats and build cyber infrastructure by offering next-generation cybersecurity consulting services. As organizations turn to a hybrid work model, the need for secure infrastructure has become important. A critical aspect of any organization’s infrastructure is its people, which is why cybersecurity training for all employees is so important. […]
August 23, Hyderabad IN. The strategic partnership aims to assist organizations in the Middle East and Africa (MEA) region to combat cyberthreats and build cyber infrastructure by offering next-generation cybersecurity consulting services. As organizations turn to a hybrid work model, the need for secure infrastructure has become important. A critical aspect of any organization’s infrastructure is its people, which is why cybersecurity training for all employees is so important. […]
 The collaboration between Bahrain’s Tamkeen, a public authority responsible for the skills development of the Kingdom’s workforce, and EC-Council, a trusted global leader in cybersecurity workforce development, have resulted in Tamkeen endorsing the Certified Application Security Engineer program (CASE .Net & CASE Java) for all Bahrainis. These 2 programs were added to Tamkeen’s specially approved list of training programs curated to uplift the much-needed cyber skills development in […]
The collaboration between Bahrain’s Tamkeen, a public authority responsible for the skills development of the Kingdom’s workforce, and EC-Council, a trusted global leader in cybersecurity workforce development, have resulted in Tamkeen endorsing the Certified Application Security Engineer program (CASE .Net & CASE Java) for all Bahrainis. These 2 programs were added to Tamkeen’s specially approved list of training programs curated to uplift the much-needed cyber skills development in […]
 EC-Council’s new Web App certification contains web application hacking and security challenges to teach participants to secure applications using real-world scenarios. Albuquerque, New Mexico/Aug 03, 2021: EC-Council, creators of the Certified Ethical Hacker certification, have launched their latest training and certification program specifically for the extremely important area of web application and hacking. Vulnerabilities in web applications are increasingly a […]
EC-Council’s new Web App certification contains web application hacking and security challenges to teach participants to secure applications using real-world scenarios. Albuquerque, New Mexico/Aug 03, 2021: EC-Council, creators of the Certified Ethical Hacker certification, have launched their latest training and certification program specifically for the extremely important area of web application and hacking. Vulnerabilities in web applications are increasingly a […]
 DUBAI, UAE, 30 July 2021 – With digital threats on the rise, Mindware, one of the leading Value-Added Distributors (VADs) in the Middle East and Africa, announced that it had signed a partnership with the International Council of E-Commerce Consultants (EC-Council). EC-Council is the owner and developer of the world-renowned Certified Ethical Hacker (CEH) program as well as multiple other […]
DUBAI, UAE, 30 July 2021 – With digital threats on the rise, Mindware, one of the leading Value-Added Distributors (VADs) in the Middle East and Africa, announced that it had signed a partnership with the International Council of E-Commerce Consultants (EC-Council). EC-Council is the owner and developer of the world-renowned Certified Ethical Hacker (CEH) program as well as multiple other […]
 All India Council of Technical Education (AICTE) and EC-Council Academia join forces to encourage the participation of more students in cybersecurity and promote the cybersecurity academic ecosystem in an immersive hybrid learning experience. The Cybersecurity industry is currently facing a massive talent shortage, and it is estimated that more than three million professionals are needed to help close the skills-gap […]
All India Council of Technical Education (AICTE) and EC-Council Academia join forces to encourage the participation of more students in cybersecurity and promote the cybersecurity academic ecosystem in an immersive hybrid learning experience. The Cybersecurity industry is currently facing a massive talent shortage, and it is estimated that more than three million professionals are needed to help close the skills-gap […]