How To Decode VIN Numbers For Vehicle Identification
VIN number is a significant number that helps you know a lot of information about any vehicle. There are a number of VIN decoders available online. You can use any decoder, but the Mercedes VIN decoder is the best option to go for.
What is a VIN Number?
VIN is the short form to Vehicle Identification Number. It is an identifying code that is unique to each and every vehicle. VIN number defines a lot of details about the particular vehicle.
The code is 17 characters long which involves numerical digits and letters. What if the code is not 17 characters long? You can cross-check it several times from several places. If the correct code is, then definitely the vehicle has been manufactured before 1981 and has limited information.
VIN is termed the DNA of vehicles. As DNA tells the traits of a human, VIN reveals essential information about the car.
How To Decode The VIN?
Analysing the VIN Number itself is sufficient to know a number of details about the vehicle. This 17 character code is a combination of codes that represents many different things about the vehicle.
How Can You Identify or Decode the VIN Number?
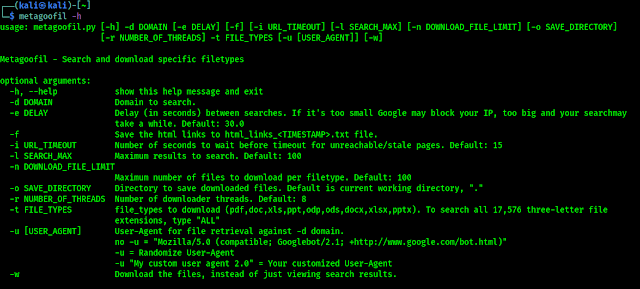
Each character of VIN represents something or the other. You can understand what each character means.
- The 1st character specifies where the vehicle is manufactured. It is the country code where the manufacturing unit is located.
- 2nd character tells about the manufacturer of the vehicle.
- 3rd character represents the vehicle type or division.
- The 4th to 8th characters represents the portrait of the vehicles that is vehicle’s brand, body style, engine size and type, model, series, etc.
- The 9th character is a security code that identifies the VIN as being authorised by the manufacturer.
- The 10th character is a representation of the model year of the car.
- The 11th character indicates which plant assembled the vehicle.
- The last six characters are the serial number or production number of the vehicle.
How is VIN Decoder Useful?
A VIN number decoder is straightforward yet effective. It uses enormous data culled from sources just like the National Highway Traffic Safety Administration (NHTSA) to extract vehicle info stored within the VIN.
A VIN decoder will provide accurate information related to a vehicle. It will help you verify the information provided manually to you. The VIN has in it several details about your car. And you might need that information while you are trying to purchase a car or get a spare for your vehicle.
How to Decode VIN Numbers for Identification of Vehicle?
Now that you know you can get a big piece of information about the vehicle through its VIN, the question arises of how anyone can decode it. VIN decoders are available to ease out your process.
Here are some quick, simple steps through which you can decode any VIN
1. Get VIN Number
The foremost step is to get the VIN number. You can get this on different locations of the car, insurance card or vehicle title.
2. Go to the Mercedes VIN Decoder
Once you get the VIN number, now you look for a VIN decoder. You will get an ample amount of options to choose from. Or a simpler and much convenient option is to go for Mercedes VIN Decoder. This is the best VIN decoder you can have.
3. Search Your VIN Number
On the homepage, you will see a tab named ‘VIN Decoder ’. Click on that tab to get the VIN decoder search bar.
Now next step is to type the VIN number and press search. You will get all the desired results within a couple of seconds.
The VIN number has now been successfully decoded for the identification of the vehicle.
VIN Decoder Results
Now that you have searched the VIN number and got your desired results. You should know beforehand that what can you expect from a VIN decoder.
You can run a VIN decoder to figure the full vehicle history report in one go.
Theft history
With the help of a VIN decoder, you will get to know if the car has ever been stolen or there has been a theft record of this car.
Accident history
Nobody’s going to tell you that the car had met an accident ever in past. This reduces the value of the vehicle. There may be some hidden damages to the vehicle that you are unable to identify.
VIN number helps you with the full accidental history of the vehicle.
Year of production
You will be able to know in which year the vehicle was manufactured.
Safety information related
Mercedes VIN decoder provides you with all the safety-related information associated with the vehicle.
Location of vehicle registration
The registration details of the vehicle, along with the location of registration, can also be obtained through the VIN decoder.
Other Vital information
VIN decoder lets you know all other vital information about the car.
With these search results, you will get to know all the above-mentioned information that you use and how you need it.
End Notes
VIN number is truly an identification code of any vehicle. You can decode a large piece of information through the VIN. Mercedes VIN decoder is a really useful tool that helps to decode the VIN numbers for vehicle identification.
You will not just be able to identify the vehicle but also get in-depth knowledge about the minute details of any vehicle.
There are many VIN decoders in the market. You can try those decoders by yourself. Although, the Mercedes VIN decoder is the most recommended VIN decoder ever. It has been highly reviewed and liked by users across different countries. When you have an option, why not go for the best.
Try the Mercedes VIN decoder now, use all its features, and you will definitely like it. All the information provided is very useful and must be known. You can use the features and results of the tool to your utmost benefit.