July 10, 2023
The main use of canarytokens is track malicious activity on our own network, application, web server and start an alert.
Now these days cyber crimes are increasing day by day and new vulnerabilities and bugs in software is founding every single day. This is very challenging job to save our application or website from cyber criminals, here canarytokens can help. Obviously this can’t save us, but it can alert us on suspicious activities on our system.
 |
| Image Copyright : stationx.net |
Previously we have covered about Honeypots. Honeypots are used to trap the attackers. Canarytokens are also one type of honeypots, with the help of canarytokens we can set trigger on our system networks website, application. Whenever someone trying to do anything wrong canarytokens can send send notifications to us.
Let’s start some practical of canarytokens. First we see how we can find someones information with canarytokens. To start this we open this link on browser https://canarytokens.org/generate
The screenshot is following :
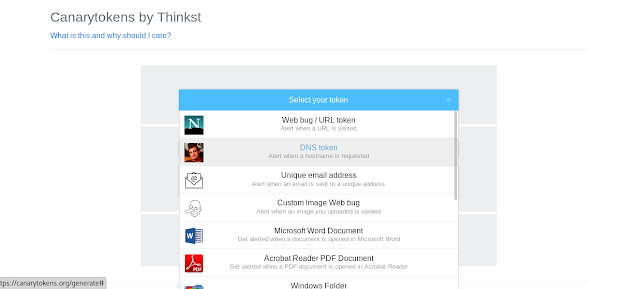
After clicking “Select your token” we got following screen:
Here we can see we can generate canarytokens for different type of works like :
- Web-bug / URL token (Alert when URL is visited)
- DNS token (Alert when a hostname is required)
- Unique email address token (Alert when an email is send to a unique address)
- Custom Image Web bug token (Alert when an image you uploaded is visited)
- Microsoft Word Document token (Get alerted when a document is opened is Microsoft Word)
- Acrobat Reader PDF Document token (Get alerted when a PDF document is opened in Acrobat Reader)
- Windows Folder token (Be notified when a windows folder is browsed in Windows explorer)
- Custom exe / binary token (Get notified when an EXE or DDL is executed)
- Cloned website token (Get an alert when your website is cloned)
- SQL Server token (Get notified when MS SQL server databases is accessed)
- QR Code token (Generate QR Code for physical token)
- SVN token (Alert when someone checks out an SVN repository)
- AWS keys token (Alert when AWS key is used)
- Fast Redirect token (Alert when url is visited. User is redirected)
- Slow Redirect token (Alert when url is visited. User is redirected, grab more information)
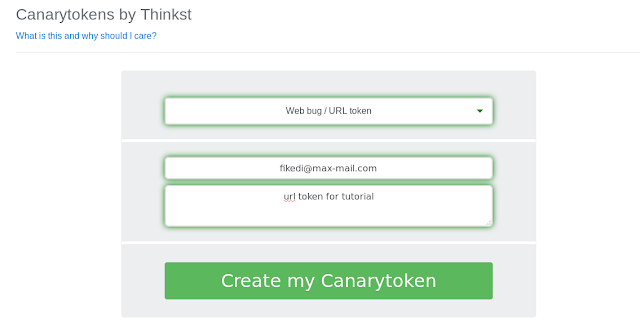
Here we choose web-bug or url token, then we need to type our e-mail address for alert notification. Then we need to put a note that when the alert comes we can identify from which tokens alert comes. This note is totally depends on us that what note we typed here.
Now we click on “Create my Canarytoken”, see the screenshot:
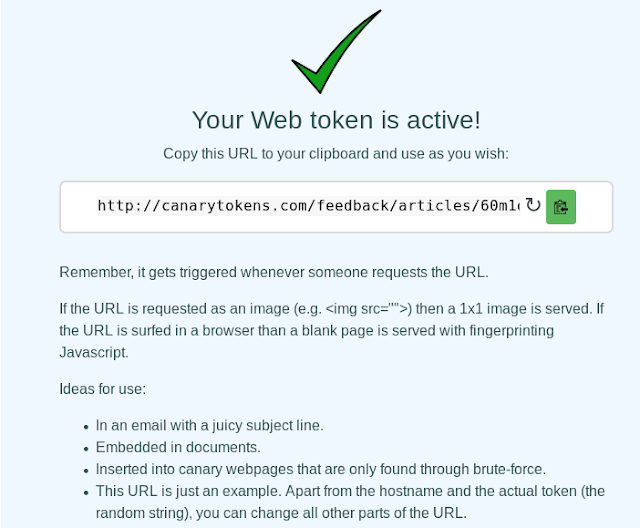
After clicking on create canarytokens we can see our canarytokens for web-bug is ready. See in the following screenshot:
Now we can copy and send this link to victim. Here is some idea about how to send this link.
- We can send this on email with a juicy subject.
- We can embedded this link with some documents.
- We also can set this link on any web page image with <img src=””> , we need to make sure that the image must be attractive so victim will click on it.
- We can use social engineering to track someone by sending this link.
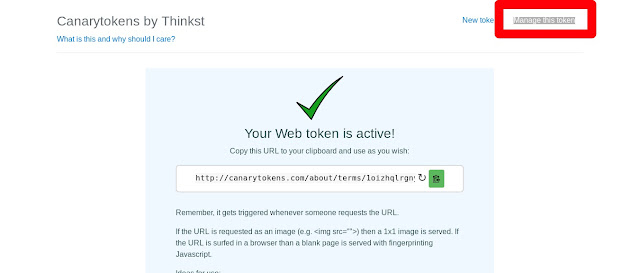
When our target clicks on this link we will get various information. I have clicked on my own link and for checking the information we are going “Manage this token” as shown in the following screenshot:
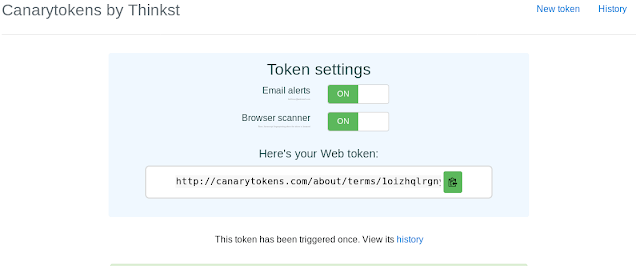
Check the next screenshot that we have successfully triggered our token, and we can now check the history.
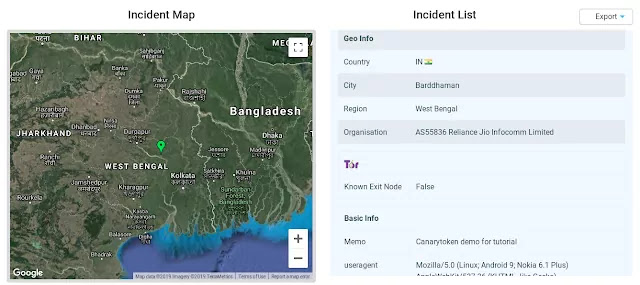
Now we got many information on target here we got
- Targets IP.
- Location of ISP.
- Target is using tor or not.
- User agent information.
- Browser have enabled java script or not.
- Platform and Operating System.
Check the following screenshot:
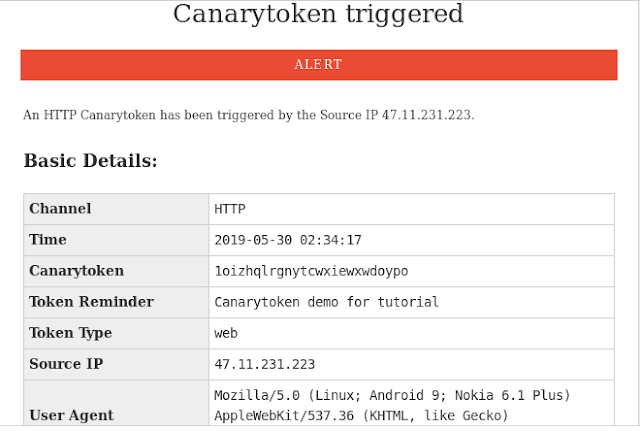
We also get same information on our provided email address.
So, we have successfully created and triggered our url canarytoken. Even we choose Microsoft word document , then we got Microsoft word file to download. After Downloading we can give the file a juicy name and send this word file by email or any other way or we can save it in some sensitive folder in our system or server. When target opens this word file we got all the information.
Same we can choose windows folder token, here we got a zip file and we need to extract the folder and rename with a spicy name, whenever someone opens our this folder in windows explorer canary token will triggered and we got all the information. So this is the way to use Canarytokens.
If it happens with us means someone send us canarytokens link then how save our identity and privacy.
If someone sen the direct link like
Here clearly seen that it is a canarytoken link but when someone use url shortner to short the link then before clicking the link we can expand the link with the help of some online services like :
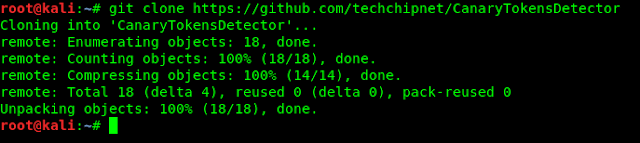
And there is a tool on Github that detects canarytoken link on Microsoft office document. We can clone this tool by applying following command:
The screenshot is following :
Then we go to the cloned folder and we also need to copy the Microsoft Word document into the same directory.
And give the file execute permission using the following command:
Then we can run the script by using following command :
The screenshot is following :
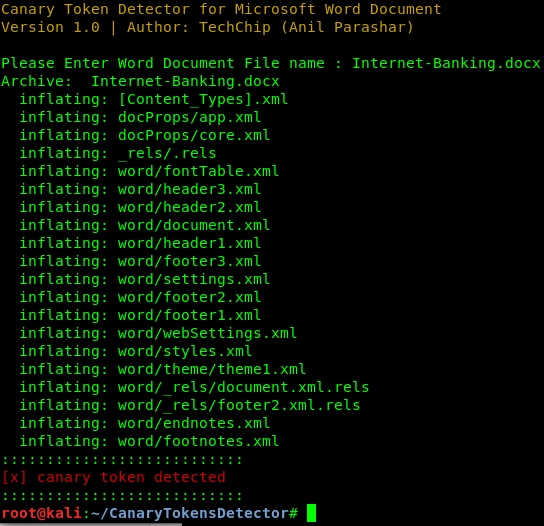
And then we type the name of the Microsoft Word file and hit Enter.
We can clearly see in the above screenshot the our this file is contains Canarytoken link.
Do you enjoy reading our articles? Be sure to follow us on Twitter and GitHub for regular updates on new articles. If you want to join our KaliLinuxIn family and be part of a community focused on Linux and Cybersecurity, feel free to join our Telegram Group.
We value building a strong community and are always here to help. Feel free to leave your comments in the comment section, as we read and reply to each one. We appreciate your engagement and look forward to connecting with you.
Article posted by: https://www.kalilinux.in/2019/05/canarytokens.html
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com
This is the article generated by feed coming from KaliLinux.in and Infocerts is only displaying the content.