Table of Contents
- Pegasus Spyware
- What is MVT ?
- Installation of MVT on Linux and Mac
- Checking for Pegasus Spyware on Android Device
- Checking for Pegasus Spyware on iPhone
- How to Remove Pegasus Spyware from Mobile Phone
Pegasus Spyware
Pegasus Spyware is a very trending topic in the world media now. It is really debatable whether, it is abused for spying on people like activists, or journalists etc or not. Without making our article controversial we directly jump into the topic. How can we find out if our phone is infected with this Pegasus Spyware or not?
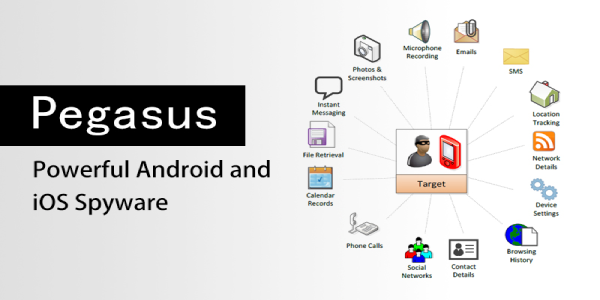
Pegasus is a spyware developed by the Israeli infosec firm NSO Group that can be covertly installed on mobile phones (and other devices) running most versions of iOS and Android. The 2021 Project Pegasus revelations suggest that current Pegasus software is able to exploit all recent iOS versions up to iOS 14.6. According to the Washington Post and other prominent media sources, Pegasus not only enables the keystroke monitoring of all communications from a phone (texts, emails, web searches) but it also enables phone call and location tracking, while also permitting NSO Group to hijack both the mobile phone’s microphone and camera, thus turning our phone into a constant surveillance device.

First of all we don’t know exactly how this malware comes into our devices and uses which vulnerability. But when it is on our device it can spy on us, by reading SMS, tracking our GPS locations, using our microphone and camera and downloading our files from our phones. Here to do everything it requires permissions from our Android or iOS. So it can be detected from there, but we need to perform some forensics test to detect it. Don’t worry it will be very easy when we are here. We are going to use MVT or Mobile Verification Toolkit on our system to detect this Pegasus Spyware. MVT was created by Amnesty International Security Lab in July 2021.
What is MVT ?
Mobile Verification Toolkit aka MVT is a collection of tools designed to facilitate the consensual forensic testing of Android and iOS devices for the purpose of identifying any signs of compromise even it can identify Pegasus. MVT’s capabilities are continuously evolving, but some of its key features include:
- Decrypt encrypted iOS backups.
- Process and parse records from numerous iOS system and apps databases, logs and system analytics.
- Extract installed applications from Android devices.
- Extract diagnostic information from Android devices through the adb protocol.
- Compare extracted records to a provided list of malicious indicators in STIX2 format.
- Generate JSON logs of extracted records, and separate JSON logs of all detected malicious traces.
- Generate a unified chronological timeline of extracted records, along with a timeline of all detected malicious traces.
Installation of MVT on Linux and Mac
Before going to install MVT we need to have Python 3.6 installed on our computer. Python is available for most of the desktop operating systems.
Installing MVT on Linux
To install MVT on Linux we need to install some dependencies, to install them we need to run following commands on our terminal window:
sudo apt install python3 python3-pip libusb-1.0-0
libusb-1.0-0 is not required if you intend to only use mvt-ios and not mvt-android, coming to these things later.
Then we need to run the following command to install MVT on our system:
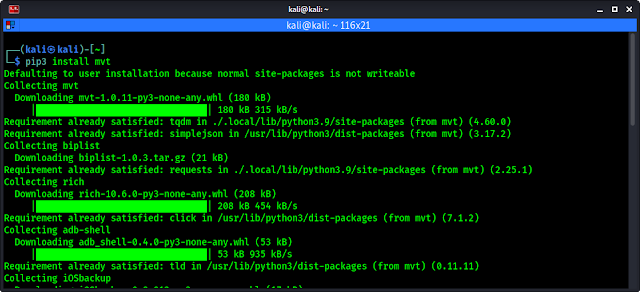
pip3 install mvt
MVT will start downloading on our system, as we can see in the following screenshot:
After a couple of minutes (time will depend on our system performance and internet speed) MVT will be installed on our Linux system.
Installing MVT on MAC
To install MVT on MAC requires Xcode and homebrew to be installed. Further the process is almost the same. We need to install dependencies to run MVP on MAC by using following command on the terminal:
brew install python3 libusb
Then we need to install MVT by using following command:
pip3 install mvt
Path correction after installation
After installing MVT on our system we can run it to check Pegasus on our mobile device, but before running it we need to fix our path to easily run this. This step sometimes already comes with some operating system. We suggest to skipping this and forward to the next step if that doesn’t work then try this.
We need to open our .bash or .zshrc (depending which shell we are using BASH or ZSH) on nano editor by using following command:
nano .zshrc
Then we need to add the following line at the end of the code (in a new line), then save and close it (by pressing ctrl+x, then Y, then Enter).
export PATH=$PATH:~/.local/bin
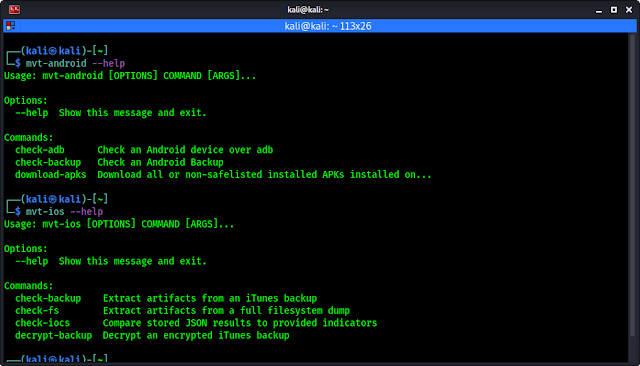
So we had installed MVT to run a forensics scan on our Mobile phones to check if our device is infected by Pegasus spyware or not. Firstly we check the help/options of this tool by applying two commands on our terminal. Two commands ? Yes one help menu is for Android another is for iOS. Both are in following:
mvt-android --help
mvt-ios --help
In the following screenshot we can see the output of above commands.
Checking for Pegasus Spyware on Android Device
If we have a suspected android device then we need to connect our Android device via ADB (Android Debug Bridge). So ADB needs to be in our system. On Linux systems we can use sudo apt install adb android-tools-adb, We can install it also on Mac. The phone’s ADB connection must be allowed inside developer options, details about ADB can be found here.
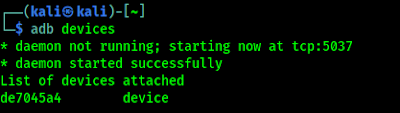
Then we need to connect our android device via USB with our computer and check that ADB is working and our mobile device is connected properly.
In the above screenshot we can see that our device is properly connected with ADB. Now we also can check the connection using MVT by using following command:
mvt-android check-adb
We may got some error like the following screenshot:
If we get this common error (already adb-server is running, we need to kill it) then we need to run the following command to solve it and check-adb again.
adb kill-server
Now here there are two type of scans we can perform on our Android devices:
- Check APKs: We can scan all installed apps.
- Check Android Backup: Create a backup of the device and scan it.
Check APKs
We can run the following command to start downloading all our Android applications on our PC and scan them.
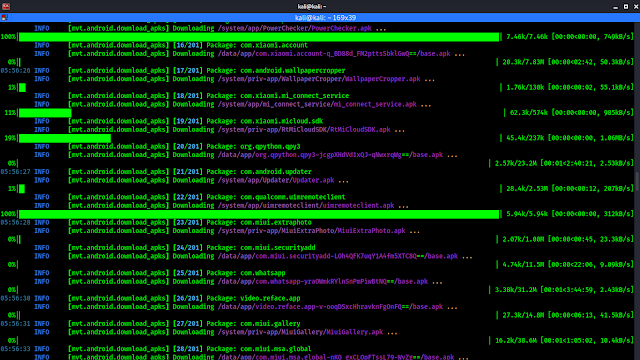
mvt-android download-apks --output androidapps --all-checks
The above command will start the work and save our all applications on a folder called androidapps, then start all checks as we commanded it.
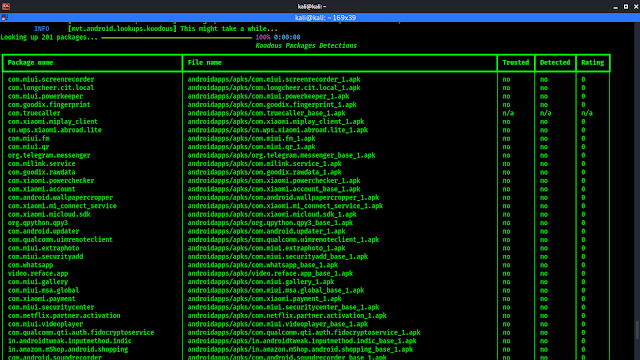
In the above screenshot we can see that we are extracting all the installed applications on our PC. After the download complete MVT will start scanning every applications, after scan it will show us a result as we can see in the following screenshot:
Here in a chart we can see MVT didn’t detect any spyware on our phone.
Check Android Backup
Some attacks against Android phones are done by sending malicious links by SMS. The Android backup feature does not allow to gather much information that can be interesting for a forensic analysis, but it can be used to extract SMSs and check them with MVT. To do so, we need to connect our Android device to our computer. We will then need to enable USB debugging on the Android device.
If this is the first time we connect to this device, we will need to approve the authentication keys through a prompt that will appear on our Android device. Then we can use adb to extract the backup for SMS only with the following command:
adb backup com.android.providers.telephony
We need to approve the backup on the phone and potentially enter a password to encrypt the backup. The backup will then be stored in a file named backup.ab on our working directory on PC.
We need to use Android Backup Extractor and download abe.jar file to convert it to a readable file format. Make sure that java is installed on our system (mostly Linux comes with it) and use the following command:
java -jar ~/Downloads/abe.jar unpack backup.ab backup.tar
We can see the output in the following screenshot:
Now we extract it by using following command:
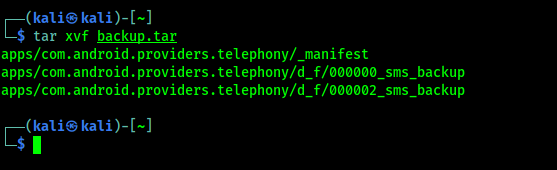
tar xvf backup.tar
Screenshot shows the output of the above command.
Then we can extract SMSs containing links with MVT:
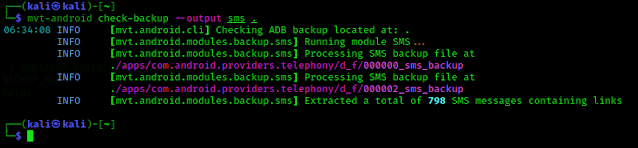
mvt-android check-backup --output sms .
The output will be saved in a folder named “sms”. In the screenshot we can see our device has lots of SMS with links, which may be dangerous.
This is how we can test an Android device to find Pegasus or any other potential spyware.
Checking for Pegasus Spyware on iPhone
Before jumping into acquiring and analyzing data from an iOS device, we should evaluate what is our precise plan of action. Because multiple options are available to us, We should define and familiarize with the most effective forensic methodology in each case.
Filesystem Dump
We will need to decide whether to attempt to jailbreak the device and obtain a full filesystem dump, or not.
While access to the full file system allows to extract data that would otherwise be unavailable, it might not always be possible to jailbreak a certain iPhone model or version of iOS. In addition, depending on the type of jailbreak available, doing so might compromise some important records, pollute others, or potentially cause unintended malfunctioning of the device later in case it is used again.
If we are not expected to return the phone, we might want to consider to attempting a jailbreak after having exhausted all other options, including a backup.
iTunes Backup
An alternative option is to generate an iTunes backup (in the most recent version of mac OS, they are no longer launched from iTunes, but directly from Finder). While backups only provide a subset of the files stored on the device, in many cases it might be sufficient to at least detect some suspicious artifacts. Backups encrypted with a password will have some additional interesting records not available in unencrypted ones, such as Safari history, Safari state, etc.
The use of MVT is almost the same here. If we read the android part then we can easily get the point, but iOS forensics and backup has some little bit different. Here we suggest to going with the Official Documentation of MVT. This is detailed enough to follow easily.
How to Remove Pegasus Spyware from Mobile Phone
OK we got this. We know that we can check for Pegasus on our mobile phone, but what if our phone is affected? In that case we suggest the following methods.
- If our Android or iPhone is not rooted (Jailbroken term used for iPhones), then we can easily remove it by doing a factory reset or hard reset to remove Pegasus. Keep the backup aside. Backing them up again on the mobile is not recommended, because we don’t know which loophole used by Pegasus (It can be media files or something can be stored).
- If we have a rooted Android device then full format or factory reset will not work here, because on rooted devices spywares are installed as default applications. Updating the Android version also doesn’t work here. Best solution can be to install a custom ROM. That can remove the entire OS with the spyware.
- If we are on a Jailbroken iPhone then we already violated Apple’s policy, they will not be going to help us. Because iOS is not open-source and uses different kernels it don’t have any practical custom ROM. In this case we can suggest a full reset of the device and check again. If Pegasus was still there we would need to buy a new phone.
- Using a feature phone may be a solution, but in this digital era this is next to impossible, so we can use some Linux phones (Smart phones comes with Linux operating system).
This is how we can find and remove if our mobile phone device is infected with Pegasus Spyware using MVT. Pegasus has been called the most sophisticated hacking software available today to intrude phones. NSO Group has, time and again, claimed that it does not hold responsibility in case of misuse of the Pegasus software. The NSO group claims that it only sells the tool to vetted governments and not individuals or any other entities.
Love our articles? Make sure to follow us on Twitter and GitHub, we post updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we are always happy to help everyone in the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.

 ‘
‘







































![Best USB WiFi Adapter For Kali Linux 2021 [Updated July] Best USB WiFi Adapter For Kali Linux 2021 [Updated July]](https://infocerts.com/wp-content/uploads/2021/07/Best-USB-WiFi-Adapter-For-Kali-Linux-2021-Updated-July-infocerts.jpg)











