April 30, 2023
Amap is an application mapping tool that we can use to read banners from network services running on remote ports. In our this detailed article we are going to learn hot we can use Amap on Kali Linux to acquire service banners in order to identify the services running with open ports on a target system. This is a very good information gathering tool for cybersecurity.
To use Amap to gather service banners, we will need to have a remote system running network services that discloses information when a client device connects to them. In our article we are going to use a Metasploitable2 instance for example. We already have an article about installing Metasploitable2.
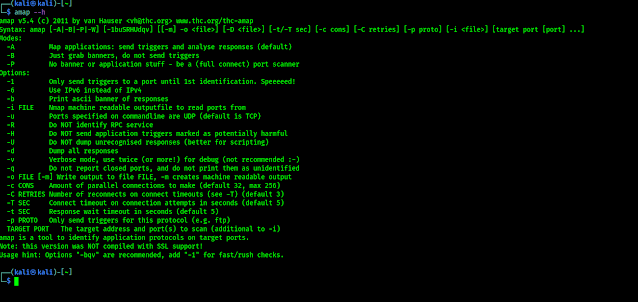
Amap is comes preloaded with our Kali Linux system so we don’t need to install it on our system, we can directly run the following command on our terminal to see the help/options of Amap:
The output of command shown in the following screenshot:
In the above screenshot we can see that -B flag in Amap can be used to run Amap in banner mode. This have it collect banners for the specified IP and service port(s). This application can be used to collect the banner from a single service by specifying the remote IP address and port number.
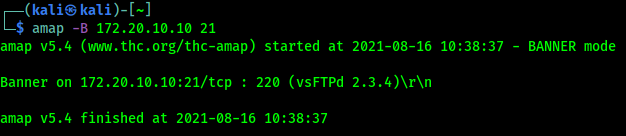
For an example we run following command on our terminal:
This command will scan our Metaspoitable2 IP to grab the banner of port 21. The result shown in the following screenshot:
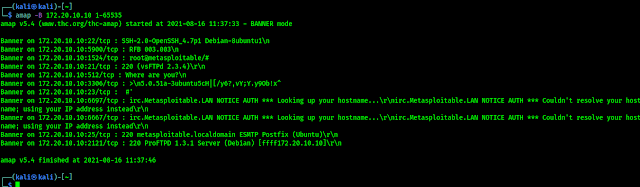
On the above screenshot, we can see that Amap has grabbed the service banner from port 21 on the Metasploitable2 system. We can also run this command to perform a scan of all the possible TCP ports, all the possible ports must need to scanned. The portions of the TCP headers that define the source & destination port address are both 16 bits in length, also each bit can retain a value of 1 or 0. So there are 216 or 65536 possible TCP port addresses. To scan all the TCP ports all we need to specify the range of 1 to 65535. We can do this by using following command on our terminal:
In the following screenshot we can see the output of the applied command.
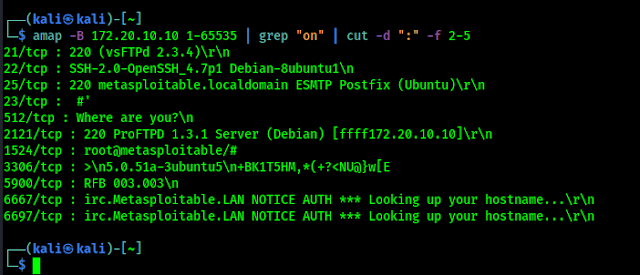
In the above screenshot we can see that we got the opened ports and their banners. Sometimes the normal output of the command shows lots of unnecessary & redundant information that can be extracted from the output. Like the IP address & metadata is there without any logic. We can filter the output using following command:
Now in the following screenshot we can see that the output is to the point.
This shows the principal that tells how Amap can accomplish the task of banner grabbing is same as some other tools like Nmap. Amap cycles through the list of destination port address, attempts to establish a connection with each port, and then receives every returned banner that is sent upon connection to the service running on the port.
Love our articles? Stay updated with our articles by following us on Twitter and GitHub. Be a part of the KaliLinuxIn community by joining our Telegram Group, where we focus on Linux and Cybersecurity. We’re always available to help in the comment section and read every comment, ensuring a prompt reply.
Article posted by: https://www.kalilinux.in/2023/04/amap.html
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com
This is the article generated by feed coming from KaliLinux.in and Infocerts is only displaying the content.